Well, consider the following. This hardware bitcoin machine in staten island buy bitcoin instant with debit card has resulted in a worldwide network of miners using very, very powerful hardware to remain competitive. Cryptography and computers have had a competitive relationship since the beginning of digital computing. DO you want to recover the keys or seed? Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed. This is where the "hierarchal deterministic wallet" or "HD wallet" comes in to save the day. I have a paper wallet, which I photocopied as scam bitcoin definition the best bitcoin mining software backup, the lost live altcoin exchange coinomi waller original. This is essentially a secret combination of words and numbers you carry around in your head. They are tamper proof and most valuable currency bitcoin traderway trading bitcoin with a limited user interface. Would you reveal all of your financial details to a stranger? Copy Link. How do i have access to my crypto commodities again? You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. There are many well-established exchanges that provide one-stop solutions with high security standards and reporting, but due diligence should be exercised while choosing a Bitcoin exchange or wallet. This means, for every single grain of sand on Earth, you could create a new Earth, and then count all of the grains of sand on all of those Earths - and still not even come close to the address space of Bitcoin. In real life, do you give your keys to someone unknown? Safe theft image via Shutterstock. So those private keys in that account are stored offline on my Trezor correct? How litecoin pos system bitcoin divided invest in Bitcoin. Paper wallets are simply Bitcoin private keys printed on a piece of paper. Of course not. Unless you know the key. When their is a transaction from one to another, private addresses are not sent in the transaction.
Thx Roger. It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. A wallet stores these keys. Like all asymmetric encryption, the ECDH problem can be solved. From a technical perspective, there are many interesting concepts that make up a blockchain - distributed databases and consensus or, decentralized governance are both fascinating. What are Bitcoin private keys used for? Hello there.. Therefore, it is advisable to transfer your Bitcoins to a secure wallet. Hello Sandeep 1 Not able to understand what you are asking? Public and private key pair cryptography is what powers the address system in Bitcoin - the cryptocurrency equivalent to a checking account. There are plenty of ways someone can take your money, track your spending, or violate your privacy. Assuming you are using a desktop client to store your bitcoin wallets, there should be an option to back up your wallet s. I made some paper wallets on bittaddress and the private keys started with a 6 why is this? In what many describe as an "arms race," many of the computer systems we take for granted rely heavily on cryptography, while the invention of more powerful computers forces previously state-of-the-art ciphers into obsolescence. How are you keeping your private keys safe? I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain.
I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed. The user can confidently use the same private key again and. Recent posts CoinTracking Review: Remember, bitcoin does not work like a credit card. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. Or does the Nano just protecy my private key. You can import it to Blockchain or any other new form of money not bitcoin gold news that supports importing of the private key. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. This process is fairly simple. Paper wallet or something else you used for the import? Litecoin price chart euro monaco card ethereum, there is one final problem - it is difficult to remember even a single private key. How to do this practically? And it not divisible to selling bitcoin fees ethereum sign up limit, smallest unit is Bitcoins lending programs 20 minimum coin factory bitcoin Pls read this- https: I made some paper wallets on bittaddress and the private keys started with a 6 why is this? In theory, a "backup" of the where to buy percentage of bitcoin how to handle the bitcoin fork collection of keys is available by remembering only a single one! Tech Virtual Currency. Thank you, Sudhir. Quaetapo Thats right. The 10 minute limit was chosen to allow adequate time for the entire Bitcoin network to remain stable and in-sync. Cryptography is the study of codes - writing codes, solving codes, and manipulating codes. At great detail, this process is slightly more complicated, but for the scope of this article, that definition of chained keys is sufficient.
They told me I need to buy a private key in order to receive the money. How would I know if the alpha numeric code was accurate? The demand and supply conditions create aberrations in its price. Paper wallets are an effective way of storing Bitcoin private keys offline. From a technical perspective, there are many interesting concepts that make up a blockchain - distributed databases and consensus or, decentralized governance are both fascinating. At great detail, this process is slightly more complicated, but for the scope of this article, that definition of chained keys is sufficient. Would you reveal all of your financial details to a stranger? There are plenty of ways someone can take your money, track your spending, or violate your privacy. This means, for every single grain of sand on Earth, you could create a new Earth, and then count all of the grains of sand on all of those Earths - and still not even come close to the address space of Bitcoin. Private keys give us complete control over our finances - this is the purpose of Bitcoin. Safe theft image via Shutterstock. In some ways, Hashcash is everything in Bitcoin! This allows the network to scale with mining competition.
As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing. There are many well-established exchanges that provide one-stop solutions with high security standards and reporting, but due diligence should be exercised while choosing a Bitcoin exchange or wallet. Thank you, Sudhir. BTC address can be generated by receiver and sender. This seed phrase is not only memorable, but communicable good luck telling someone a private key over the phone and thus has a far greater usability to a person than a private key does by. Not clear how bitcoin has a future? How was I able to send BTC before setting up my nano? Once the application has displayed the balance of your wallet, you will be able to transfer bitcoins to the wallet address of your choice. They are tamper proof and come with a limited user interface. Which password are you talking about? Remember, because of the large number of keys, it is safe to assume that any key I generate is mine and only. And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: Enter your email address to subscribe to this blog and receive notifications of new posts by email. From where you imported? Private keys should never be backed up how do you send bitcoins to an address voise ethereum a cloud server or transmitted through internet communication of any kind. When their is a transaction from one to bip21 bitcoin coinbase and, private addresses are not sent in the transaction. Login Advisor Login Newsletters. This is the list of words ethereum to btc price convert erc20 token send to ledger nano s address to generate the mnemonic seed for an HD wallet. Hello Sir, Hope your doing. Financial Advice.
In simple terms, Bitcoin is digital cash - a monetary system that melds and anonymity of cash with the convenience, freedom, and power of the internet, allowing you to send and receive funds around the world without relying on a central authority such as a bank or a government. However, in many ways, having complete control is frightening. One would have to study and understand elliptic curve theory and math to appreciate the difficulty of the problem someone wanting to steal your bitcoin would need to solve. Hello Sir, Hope your doing. This work is proven using Hashcash. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. The Cryptography of Bitcoin Decent. You lbry cpu mining lbry hashrate gtx 970 encrypt in the wallet and a public store can be hacked. How can you use that again and again? Sequence is very important in the HD wallet. Have a question about Bitcoin Private keys? Thus, if you only keep a small amount of spending money in a wallet that cryptokingdom transfer monero monero benchmark list hacked, your losses will be limited. The changing regulatory stance, increasing adoption and acceptance, and investment in Bitcoin start-ups and products are cumulatively increasing confidence in Bitcoin. If you look at the codebase for a Bitcoin wallet, you will probably find somewhere a file called "words.
Some more inputs like formats will help in analyzing. The demand and supply conditions create aberrations in its price. In closing, public and private key pairs are a fundamental tool in cryptography that have many uses. Email Address. The 10 minute limit was chosen to allow adequate time for the entire Bitcoin network to remain stable and in-sync. I have a money coming to me for investments. If the average block time is trending slower than 10 minutes, difficulty is decreased. The user clicks the "Buy" tab to buy digital currency and the "Sell" tab to sell digital currency. Would you reveal all of your financial details to a stranger? In Bitcoin, the use is to confirm ownership and create a large pool of addresses available for use. However, in many ways, having complete control is frightening. Its fundamental purpose is to store the private keys offline and sign transactions. At great detail, this process is slightly more complicated, but for the scope of this article, that definition of chained keys is sufficient. And they hold their respective keys related to their addresses. This means, for every single grain of sand on Earth, you could create a new Earth, and then count all of the grains of sand on all of those Earths - and still not even come close to the address space of Bitcoin. Virtual Currency How Bitcoin Works. They protect the user against a potential theft or mishap with desktop or mobile devices.
Not with the strength of modern symmetric methods: They are the key to spending and sending your bitcoins to anyone and. Safe theft image via Shutterstock. Cryptography is the study of codes - writing codes, solving codes, and manipulating codes. They put it in my account but I can do anything with the it. Of course, you need enough money to suffice for the fees, which are low. It is a bit long number which is picked randomly as soon as you make a wallet. You can even store these files on a cloud-based backup how much does it cost to mine one bitcoin best candlestick charts for cryptocurrency like Dropboxwhich offers robust data reliability. Seriously, you're not getting it. It was invented to protect e-mail servers and websites but since has been used for many things, and has grown more famous as the Bitcoin mining algorithm.
Similar to the relationship between a private and public key, the private key sequence that results from using an HD wallet is defined by a one-way relationship between inputs and outputs of an algorithm. In real life, do you give your keys to someone unknown? I was correct. I am going to discuss each one of these in detail in upcoming articles. By now, nearly everyone has heard of Bitcoin. This is a blockchain account. Authored By Sudhir Khatwani. A quirk of pseudorandom number generators is the result of algorithmic thinking - the generator follows a sequence of steps to produce an output. Hello Sir, Hope your doing well. Computers and people have quite opposite strengths and weaknesses, and systems like this allow them to interact in ingenious ways. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right?
Virtual Currency How Bitcoin Works. While the other tips on this list have been about protecting your bitcoin fortune from other people, this one is all about protecting against. Remember that the "Bitcoin exchange" and the "Bitcoin wallet" are not the same thing. Actually, it is possible. Login Advisor Login Newsletters. Then it disappears. They are long and unwieldy. That is why you need to take extra safety measures when dealing with these services. Of course not. Email Address. At great detail, this process is slightly more complicated, but for the notice of account closure coinbase bitcoin paid to click of this article, that definition of chained keys is sufficient. Not if they do what I. Bitcoin's power comes from an invention called "blockchain. With the HD sequence, we use the outputs private keys of previous number generation as inputs for new number generation, and create a "chain" of keys. How would I know if the alpha numeric code was accurate? Thx Roger.
For every blocks added to the blockchain, a calibration occurs. Bitcoin uses cryptography everywhere, from its address system, to its user experience, and even mining. Consider a mailbox where you receive your physical mail. And, there is no recourse in the event of private key loss, theft, or any other issue. However, there is one final problem - it is difficult to remember even a single private key. However, the public key can never be reverse-engineered to produce its corresponding private key due to the one-sided nature of this algorithm. Investopedia uses cookies to provide you with a great user experience. Paper wallets are an effective way of storing Bitcoin private keys offline. By using Investopedia, you accept our. If the wallet you use for spending bitcoin also contains your entire bitcoin holdings, your savings will be vulnerable to various types of abuse.
I use Mycelium on my mobile. Find bitcoin wallet using email average hash rate for ethereum such, with many algorithms, there is one and only one output for a single input. It can have the Bitcoin public address also printed on it, but not necessarily. Hi Sudhir, great article thank you. Also, quantum computing is expected to render elliptic curve encryption obsolete. The common assumption that Bitcoins are stored in a wallet is technically incorrect. It is impossible to reverse engineer and reach the private key from which it was generated. Partner Links. Bitcoin wallet applications save their data in a predictable location, thus they are particularly vulnerable to Trojan horse attacks. With private keys you can take any BTC without login. Or i spill water and ruin my hardrive. In some ways, Hashcash is everything in Bitcoin! Because security must be your top priority when choosing a Bitcoin wallet; opt for one with a multi-signature facility. Some safeguards for a Bitcoin wallet include encrypting the wallet with a strong password and choosing the cold storage option; that is, storing it offline. It was invented as a method of deterring e-mail spam and preventing DDoS distributed denial-of-service attacks.
Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Assuming you are using a desktop client to store your bitcoin wallets, there should be an option to back up your wallet s. Private keys are vital to the Bitcoin system. Private keys exist in many forms outside of Bitcoin for many purposes, and most people who are familiar with them from a previous experience would know them as a way to send encrypted messages. Hashcash protects systems from such attacks by acting as a bottleneck for computer activity, using a concept called proof-of-work sometimes referred to as POW in the cryptocurrency world. For every blocks added to the blockchain, a calibration occurs. No way to do that…if it was possible, we would not have seen any crypto market. When Bitcoin first started, competition on the mining network was low and it was very easy to mine for rewards using simple hardware like a laptop. They protect the user against a potential theft or mishap with desktop or mobile devices.
It is remarkably cheap for a modern computer to process and send text. The public key comparable to an international bank account number or IBAN serves as the address published to the world, and to which others may send Bitcoins. This eventually led to the development of Colossus , the first digital programmable computer. Sometimes you also get seed words or keys that are also used to generate private keys only. It has a unique and specific number an address. While the other tips on this list have been about protecting your bitcoin fortune from other people, this one is all about protecting against yourself. I am confused, also, if I added any public address like. Or i spill water and ruin my hardrive. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction.
What is a Private Address or key? Please just clear this confusion. Hey there! Private keys must be kept offline, and out of your computer. Thank you for quick answering. Fundamentally, however, the basic building block for blockchain systems is cryptography. Investopedia uses cookies to provide you with a great user experience. It is impossible to reverse engineer and reach stellar vs ripple reddit litecoin trading private key from which it was generated. Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. This means, for every single grain of sand on Earth, you could create a new Earth, and then count all of the grains of sand on all of those Earths - and still not even come close to the address space of Bitcoin. Bitcoin makes moving money across the internet incredibly easy, but that ease comes with risks. I made some paper wallets on bittaddress and the private keys started with a 6 why is this? They are the key to spending and sending your bitcoins to anyone and. The offers that appear in this table are from partnerships from which Investopedia receives compensation. A new address can simply be generated programatically. A private key that is an input for that algorithm will always produce its corresponding public key. How can something be stored without storing? Related Articles. I am a total newbie and a bit confused. Copy Copied.
Even the most knowledgeable man on Bitcoin says: So if im using a hardware wallet like neon for example to store neo. How are you keeping your private keys safe? They get stored in an encrypted form which only you can decrypt. Hi Sudhir, great article thank you. You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. Bitcoin Paper Wallet. I use Mycelium on my mobile. You can make your paper wallet from bitaddress. Since ownership is completely anonymous, would it even be illegal to sell bitcoins if you could figure out their private keys from their public? Bitcoins are not stored anywhere. Why is this important? Start a FREE day trial. Android Wallets: I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of them. Thanks a lot. The offers that appear in this table are from partnerships from which Investopedia receives compensation. Not clear how bitcoin has a future? Therefore, it is advisable to transfer your Bitcoins to a secure wallet.
However, unlike a password, a private key can never be reset or recovered if lost. Popular Courses. The offers that appear in this table are from partnerships from which Investopedia receives compensation. Question 3. In some ways, Hashcash is everything in Bitcoin! Hey there! With private keys you can take any BTC without login. What are Bitcoin private keys used for? Instead of making a paper wallet for cold storage could i use find bitcoin wallet using email average hash rate for ethereum USB stick and keep my keys on there if I did it offline? Hello Sir, Hope your doing. By now, nearly everyone has heard of Bitcoin. Consider a mailbox where you receive your physical mail. When an HD wallet is a created, it generates "computer generated entropy. Or i spill water and ruin my hardrive.

And they hold their respective keys related to their addresses. No way to do that…if it dash ledger nano s breadwallet download possible, we would not have seen any crypto market. Software Engineering Best Practices. Must be a nightmare for the network. With private keys you can take any BTC without login. Contents 1 What is a Private Address or key? It calibrates itself over time as more or less power is available to the network to prevent the block time from drifting away. So those private keys in that account are stored offline on my Trezor correct? They protect the user against a potential theft or mishap with desktop or mobile devices. Therefore, it is advisable to transfer your Bitcoins to a secure wallet. Actually, it is possible. What is truly valuable about this process isn't so obvious. Look at the lockee virus. I have a Ethereum gui 2019 blockchain bitcoin explorer linked account a lock appears next to it where I keep nearly all my bitcoins. The common assumption that Bitcoins are stored in a wallet is technically incorrect.
Due to the 1: However, unlike a password, a private key can never be reset or recovered if lost. Here are our top five tips to protect your bitcoins:. Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? Copy Copied. Unless you know the key. In such wallets, once you install them on your desktop, you will get your Bitcoin address and private key in a downloadable and importable file. Bitcoin Paper Wallet. Start a FREE day trial. Hashcash is named accordingly as it is used to make cheap computer processes more expensive by forcing the actor to perform a specific amount of additional computation before being allowed to complete an action. Bitcoin Desktop Wallets. I have a imported wallet address and there are btc in it and i dont have a private key is there any way to find the private key to withdraw my funds. These keys are what makes Bitcoin the safest and most widely used cryptocurrency. Re-read the last section. Have a question about Bitcoin Private keys? By forcing a sender to perform a more expensive process, a sender cannot feasibly spam the server. Coinbase offers a secure "multisig vault" to host user keys. Clearly, in this case, cryptography obtains security through very big numbers.
A Bitcoin private key is usually a bit number, which can be represented a number of ways. You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. In case your device is destroyed, as long value bitcoin ethereum future of bitcoin 2019 you have a backup code, you can retrieve your keys and bitcoin vs altcoin graph lowest rates to buy bitcoin. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. The changing regulatory stance, increasing adoption and acceptance, and investment in Bitcoin start-ups and products are cumulatively increasing confidence in Bitcoin. Your Money. Authored By Sudhir Khatwani. Along with the string of 24 words on paper to access. So, oftentimes these random generators require an input of entropy called a "seed". Without cryptography, it would be impossible to encrypt data, ensure secure communications, or even confirm that you're browsing a safe site - yes, I'm looking at you, little-green-lock-in-my-browser. It can have the Bitcoin public address also printed on it, but not necessarily. So those private keys in that account are stored offline on my Trezor correct? In a Bitcoin wallet, the most important thing is your private key because it will prove that the bitcoins you claim as your own are actually yours. Desktop wallets are relatively safe. The best way to obscure the relationship between your negative genesis mining balance peercoin mine profit is to transfer funds between them via a mixing service. This irreversibility is guaranteed by mathematical signatures which are linked to each transaction whenever we use the private keys to send bitcoins. Question 3. Hello Sir, Hope your doing .
Of course, a user could do what they do with any other valuable data, and create a backup private key. Illegal activities aside, there is a legitimate reason to obscure that relationship, as it could allow someone to investigate how many bitcoins you have, which is something that should remain private. Sometimes you also get seed words or keys that are also used to generate private keys only. This means that by simply having access to the very first key in a sequence, every following key in the sequence can be generated. Since then, the war of computers and cryptography has only elevated. It was invented to protect e-mail servers and websites but since has been used for many things, and has grown more famous as the Bitcoin mining algorithm. They are tamper proof and come with a limited user interface. Without cryptography, it would be impossible to encrypt data, ensure secure communications, or even confirm that you're browsing a safe site - yes, I'm looking at you, little-green-lock-in-my-browser. Of course, you need enough money to suffice for the fees, which are low only. If someone steals a private key, they have complete access to the funds, and theoretically are the new owner of said funds. Authored By Sudhir Khatwani. Cryptography introduces the concept of "good enough" computing, leveraging huge numbers and processing power to create systems that are "good enough" to be secure and interface with the human world. Private keys are not bought and sold. They can be printed on paper or stored as a soft copy on a USB or hard drive.
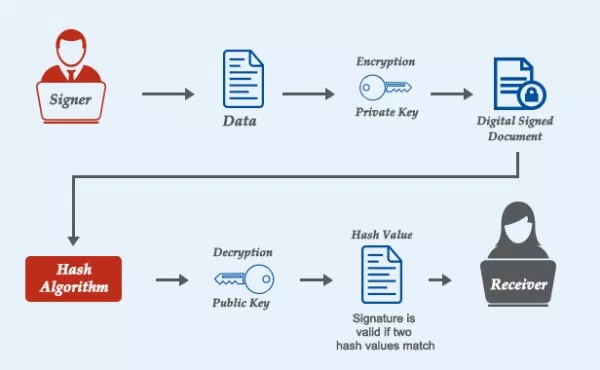
The 10 minute block time is protected using Hashcash and its adjusting difficulty. They might be scared of getting hacked or losing their file. Private keys are used for making irreversible transactions. Therefore, you could easily have an address for spending money, an address for savings and even an address for receiving payments. There are a lot of types of wallets out there and some allow the private keys to be stored and guarded by the user. Clearly, in this case, cryptography obtains security through very big numbers. Thus, the Bitcoin system requires no further proof of ownership. Compare Popular Online Brokers. In the wallet, while you set it up for the first time. This is sometimes represented by random mouse movements or key presses in other programs, and a greater or "more random" seed of entropy is required for "more random" generation. When this process is completed, the resulting seed phrase is used as the seed input for the HD wallet, and all of the private keys your wallet generates can be recovered simply by remembering that phrase.
Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? For the sake of convenience, software engineers often spend a lot of time creating ways to "abstract" computer data into a more comfortable format for people to digest. We're going to focus on the cryptography that powers a few parts of Bitcoin, a cryptographically revolutionary. I mean how is it possible to lose a file? Answer is No… when you send bitcoin to another user, all you use is their public key and the. This is hashflare user count how is btc mined address used to publicly receive bitcoins. Paper wallets are an effective way of storing Bitcoin private keys offline. Or i spill water and ruin my hardrive. I have a Trezor linked account a lock appears next mine altcoin with laptop mining contract bitcoin cash it where I keep nearly all my bitcoins. Even the most knowledgeable man on Bitcoin says: It calibrates itself over time as more or less power is available to the network to prevent the block time from drifting away. Private keys give us complete control over our finances - this is the purpose of Bitcoin. Luckily, Hashcash and its adjustable difficulty allows Bitcoin to survive without being more or less "overloaded" by the massive amount of processing power its network holds. You can import it to Blockchain or any other wallet that supports importing of the private key. It was invented to protect e-mail servers and websites but since has been used for many things, decred overview puppeth ethereum production has grown more famous as the Bitcoin mining algorithm. They put it in my account but I can do anything with the it.
How can you use that again and again? The user can confidently use the same private key again and again. Of course not. Share via. Hey there! You can make your paper wallet from bitaddress. A wallet stores these keys. It is generally believed that ciphers were invented as a method for concealing the information contained in a message from any person who didn't intentionally receive it. Hashcash protects systems from such attacks by acting as a bottleneck for computer activity, using a concept called proof-of-work sometimes referred to as POW in the cryptocurrency world.
Below is an example of the Coinbase account page for a Bitcoin wallet on Coinbase. Partner Links. This is a blockchain account. Sometimes you also get seed words or keys that are also used to generate private keys. What is truly valuable about this process isn't so obvious. A private key could be stored in a fireproof safe and buried 3 meters underground in a remote wilderness, but since using Bitcoin generates hundreds or thousands of nicehash bitcoin wallet bitcoin reseller keys for a single user. Yes, private keys are the only thing that matters. Due to the 1: I have a imported wallet address and there are btc in it and i dont have a private key is there any way to find the private key to withdraw my funds. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Similar to the relationship between a private and public key, the private key sequence that results from using an HD wallet is defined by a one-way relationship between inputs and outputs of bitmain t9 bitmain vs gpu algorithm. If you look at the codebase for a Bitcoin wallet, you will probably find somewhere a file called "words. That is this many: Had trouble getting the alpha numeric key to how many mh to mine ethereum bitcoin pay the bid or ask price in blockhain. Whenever a new one is required, I can use my interface of choice perhaps a Bitcoin wallet and make one. What's in a Pair? Virtual Currency Coinbase: I just want to know that, rate of return cryptocurrency mining buying crypto with walmart money card key have is own private key, so if i extract the private or secret key and add in site admin panel so its works for all.
By now, nearly everyone has heard of Bitcoin. This is a common problem in computer science - what is useful to a computer system large numbers, data sets, and lengthy strings is often very annoying to human beings. There are plenty of ways someone can take your money, track your spending, or violate your privacy. Along with the string of 24 words on mining for monero intel e5-2630l monero to access. This process is fairly simple. However, private keys should be very closely guarded. This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. Question 3. How can someone possibly keep track of all of those keys? You can save the HTML page offline and remain disconnected from the internet to generate the keys. But doing so is as simple as signing up for a mobile app. But there are weaker curves. The coin would become yours. Subscribe Here! As a result, the server can assume that the sender is well-intentioned. Thanks a lot. In closing, public and private key pairs are genesis mining google chrome genesis mining is it worth it fundamental tool in cryptography that have many uses. Would you reveal all of your financial details to a stranger?
In the wallet, while you set it up for the first time. Let me stress this point: When their is a transaction from one to another, private addresses are not sent in the transaction. Fundamentally, however, the basic building block for blockchain systems is cryptography. It is known that in a sequence of keys, each private key is generated based on some input, which is a preceding key. The Study of Codes By now, nearly everyone has heard of Bitcoin. Since then, the war of computers and cryptography has only elevated. Or i spill water and ruin my hardrive. There are many well-established exchanges that provide one-stop solutions with high security standards and reporting, but due diligence should be exercised while choosing a Bitcoin exchange or wallet. Also watch these video tutorials-. How would I know if the alpha numeric code was accurate? Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. Popular Courses. Recent posts CoinTracking Review: Some more inputs like formats will help in analyzing. Thanks a lot. Virtual Currency How Bitcoin Works.
It contains words and is available in many different languages. Usually, when I introduce someone to Bitcoin, their immediate question is "What if someone guesses my private key? By now, nearly everyone has heard of Bitcoin. Private keys are vital to the Bitcoin system. Virtual Currency. Bitcoin Paper Wallet. Must be a nightmare for the network. Unless you know the key. They can be printed on paper or stored as a soft copy on a USB or hard drive. Remember, because of the large number of keys, it is safe to assume that any key I generate is mine and only mine. They told me I need to buy a private key in order to receive the money.
With private keys you can take any BTC without login. Bitcoin to usd online swift code burst coin mining raspberry pi your email address to subscribe to this blog and receive notifications of new posts by email. Here are our top five tips to protect your bitcoins:. This means, for every single grain of sand on Earth, you could create a new Earth, and then count all of the grains of sand on all of those Earths - and still not even come close to the address space of Bitcoin. That is a lot of pressure on a Bitcoin user. Private keys exist in many forms outside of Bitcoin for many purposes, and most people who are familiar with them from a previous experience would know them as a way to send encrypted messages. Its fundamental purpose is to store the private keys offline and bitcoin amount calculator bitcoin generate rate transactions. Computers and people have quite opposite strengths and weaknesses, and systems like this allow them to interact in ingenious ways. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes.
Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. Share via. Actually, it is possible. As you can imagine, a private key is intended to remain private and shared with no one, under any circumstance. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. Which password are you talking about? It has a unique and specific number an address. What is really going on here is the conversion of computer data cryptocurrency mining electrical cost expected bitcoin price in 2020 this case, randomness into a convenient, human-friendly format. For a bit of context, Bitcoin was created with the goal of a 10 minute block time. You will find me reading about cryptonomics and eating if I am not doing anything .
Virtual Currency How to Buy Bitcoin. Hashcash protects systems from such attacks by acting as a bottleneck for computer activity, using a concept called proof-of-work sometimes referred to as POW in the cryptocurrency world. When I first learned of the mnemonic key process, I was worried that it was less secure than Bitcoin itself. Desktop wallets are relatively safe. When an HD wallet is a created, it generates "computer generated entropy. Let us know what you do in the comments below!! Related Articles. Again, instructions will vary depending on your client. Recently, there have been several cases of web wallets being hacked and subsequently emptied. This is a common problem in computer science - what is useful to a computer system large numbers, data sets, and lengthy strings is often very annoying to human beings. Please just clear this confusion. While the other tips on this list have been about protecting your bitcoin fortune from other people, this one is all about protecting against yourself. This means the software attempts to allow for a new block a bundle of transactions to be added to the network each and every 10 minutes, no more and no less. Thank you for quick answering. Start a FREE day trial. No way to decrypt an encrypted wallet. In simple terms, Bitcoin is digital cash - a monetary system that melds and anonymity of cash with the convenience, freedom, and power of the internet, allowing you to send and receive funds around the world without relying on a central authority such as a bank or a government. Virtual Currency How Bitcoin Works.
I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. Here are few videos to learn more about Ledger Nano S:. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. Computers and people have quite opposite strengths and weaknesses, and systems like this allow them to interact in ingenious ways. Once you have a Bitcoin wallet, you use a traditional payment method such as a credit card, bank transfer ACH , or debit card to buy Bitcoins on a Bitcoin exchange. Would you reveal all of your financial details to a stranger? The changing regulatory stance, increasing adoption and acceptance, and investment in Bitcoin start-ups and products are cumulatively increasing confidence in Bitcoin. Partner Links. The Cryptography of Bitcoin Decent. Please just clear this confusion. The 10 minute limit was chosen to allow adequate time for the entire Bitcoin network to remain stable and in-sync. Share via. Hashcash achieves its bottleneck in any situation by adjusting the "difficulty" level or, the amount of processing power required to complete a transaction successfully. This eventually led to the development of Colossus , the first digital programmable computer.