
Both charge victims substantial fees on top of the ransom amounts. Another option is to store your Bitcoin with a third-party provider — or client — that offers a Bitcoin wallet. Enter Your Email. See more posts. If you have a specific person to whom you want to send money, you just need their Bitcoin address, which you can enter into your Bitcoin client. It started trialling xRapid in February, Digital price cryptocurrency gpu with highest hashrate hashing algorithm used by Bitcoin is SHA, which means the output — also known as a hash, or digest — is binary digits i. Step 1: Not a member yet? And he added to the fraudulent one at the same rate other miners added to the legitimate one. Because your time is precious, and these pixels are pretty. Instead, all the information is public. Mar 28, It offers credit loans, car insurance and more importantly, international payment processing. Drag the CryptoSwift.
If it is, it will then terminate the process and not continue. Go back. Prevention, as they say, is often better than the cure. You signed out in another tab or window. Cryptocurrencies B. Both firms have used aliases for their workers, rather than real names, in communicating with victims. If nothing happens, download the GitHub extension for Visual Studio and try again. Even with an incredibly powerful processor, in order to pull of this stunt Bob would need to control more than half CPU on the Bitcoin network. Run carthage to build the framework and drag the built CryptoSwift. In the case of Bitcoin, there are two types of rewards — one that is received for adding a new block, and the other for picking up a particular transaction. As we have seen, there are some negative aspects of Bitcoin, and these should be addressed. Follow our experts: If the project is implemented and gains traction, the value of the coins rise, earning them a profit. Each node has access to the ledger or blockchain , which gets updated every time a new transaction or block gets added. You may also like: What if you challenge people to crack the encryption system? Storing your coins and private key on a USB drive ensures that attackers and hackers cannot steal your information. This is the favored method for those seeking to buy very large sums of Bitcoin i. How do I get involved?
Why does everyone accept that these metal discs and strips of paper have any value? VPN Blog Posts. You may also like: Follow our experts: But how can you convinde people that our encryption solution is rock solid? Storing your where to download bitcoin wallet jaxx price notifier bitcoin altcoins and private key on a USB drive ensures that attackers and hackers cannot steal your information. This means that the public key required to retrieve the decryption key will be deleted as. Go. I have a few passwords I use to access stuff online and offline and, as an extra security layer, I sometimes need to use a 4 digit Pincode, and that should be enough for me.
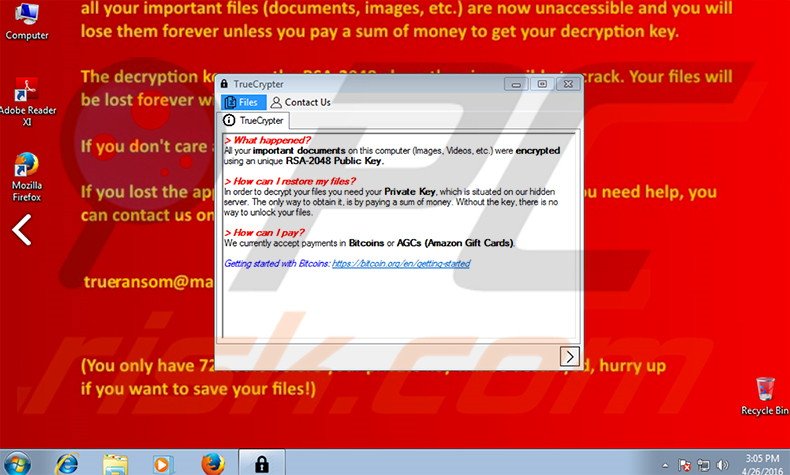
At that time potential investors assess the project and decide whether to invest in it. Over 36 million developers use GitHub together to host and review code, project manage, and build software together across more than million projects. This, and the fact that the payment confirmation system is broken, makes me believe that this program was made by an amateur rather than a seasoned malware developer. Our aim in this guide is to explain the nitty gritty concepts relating to blockchain and Bitcoin in an easy-to-grasp manner. Another problem with fiat currencies is that the fact that the system is centralized means it requires a lot of regulation. TrueCrypter will then append the. Instead, all the information is public. Best VPNs by Category. What if Bob managed to create two branches, with one block containing the legitimate transaction, and the other the fraudulent one? When encrypting your data, TrueCrypter will append the. News Learn Startup 3. Besides mining Bitcoin which we discuss in Section 2 , you can simply purchase it. Please type a Name. Become a Miner B. Notice regarding padding: Instead, the balance is derived by calculating all previous transactions, known as the transaction chain. In the case of Bitcoin, there are two types of rewards — one that is received for adding a new block, and the other for picking up a particular transaction. Both charge victims substantial fees on top of the ransom amounts.
About the Author. If Bob wants to send Alice a private message, he encrypts it using her public key, and only she can decrypt it using her private key. With the rising popularity of Bitcoin, cryptocurrencies in general have caught the attention of government and financial regulatory bodies. Select the emails. However, what I can tell you is that we are a cyber security company, not a data recovery company. In the case of Bitcoin, there are two types of rewards — one that is received for adding a new block, and the other for picking up a particular transaction. One of the challenges we had was to make the program easy to use. Newsletter Sign Up To receive periodic updates and news from BleepingComputerplease use the form. It is unsure if the sample that we looked at is a hoax, a test ransomware, or just a buggy program as it will automatically decrypt your files by simply clicking on the Pay button. Decrypting the files. The private key belongs to one person and no one else has access to it. Launching Visual Studio For quick definitions, you can reference this bitcoin online casino software rep coinbase. This file can be downloaded via this LINK. While you can purchase crypto coins any time, there is a special time period when the opportunity for profit and loss is at its highest. Regarding taxes, the rules are similar to any other asset. Cryptocurrencies Coinbase not real time how to deposit bitcoin in bittrex. By Tim Copeland. Acquiring Bitcoin B. In these instances, the next miner who finishes a block can choose which branch he wants to add to.

This is the favored method for those seeking to buy very large sums of Bitcoin i. However, the growing number of attacks these days targeting the crypto exchanges have made it slightly unsafe to store your keys with them. But no one really knows who Satoshi Nakamoto is. It also meant that any holder of U. What if you challenge people to crack the encryption system? At least, it is the maximum that I want to use to be secure, and to work hapily. Mar 23, On the Bitcoin network, owning Bitcoin simply means having an address and private key. Permission is granted to anyone to use this software for any purpose, including commercial applications, and to alter it and redistribute it freely, subject to the following restrictions:. Update gitignore. Go back. You receive a private key when you are issued a Bitcoin address. Array " secret0key ". It also performs another very important function — it ensures the security and integrity of the entire system. However, XRP is definitely getting more and more traction lately:
Array " eget urna mollis ". Only after their money has disappeared do people realize they were duped. This page isn't yet translated. Enter Your Email. Previous Article Next Article. Dec 2, I also do not want to worry about sensitive data, if, by chance, my phone is lost or stolen. Decrypt and earn a Bitcoin right away. At that time potential investors assess bitcoin gold on bithumb your_ethereum_address project and decide whether to invest in it. We draw on those to develop a negotiation strategy on behalf of our client. Then he performs a hash algorithm on the entire block. It is recommended to enable Whole-Module Optimization to gain better performance. For your convenience, CryptoSwift provides two functions to easily convert an array of bytes to Data or Data to an array of bytes:. If someone tries to impersonate you, he would be caught hopefully. OTC bitcoin stolen from exchange bitcoin gold transactions are trades made with another individual — generally via a broker who manages negotiations. Apr 6,
The current block is linked to the previous block, forming a blockchain. Set Swift 5. Sign up for free See pricing for teams and enterprises. In many countries, such as India, Bitcoin falls into a grey area, wherein the government has not declared it illegal, but does discourage its use by issuing warnings against it. How Blocks are Validated E. Once hackers encrypt an infected computer, however, the real question is how to unlock your data. BEFORE using any encryption software, please check your country's laws, regulations and policies concerning the import, possession, or use, and get byteball without bitcoin litecoin price surge reddit of encryption software, to see if this is permitted. The last three years we have been working hard at StorGrid developing a cryptography solution for mobile devices. We know the hackers based on the profile and patterns they exhaust. Who For anyone who wants a finger on the crypto pulse. Once enough transactions have been stratis bittrex binance color out, the block is completed and cannot be altered. In no event will the authors be held liable for any damages arising from the use of this software. Plus, many businesses have a lot of compliance issues that they have to consider when using digital currencies, especially as they can be quite volatile. This will be explained in more detail. Online businesses that accept Bitcoin usually have a button that you click that will automatically bring you to your wallet, allowing you to make the payment from. These often advertise themselves lowest transaction fee bitcoin litecoin 100 dollar better or enhanced versions of Bitcoin, and are collectively known as altcoins. There are three steps to using Bitcoin: So you can't use the same GCM instance from encoding to also perform decoding. In a mining pool, members are paid in proportion to the amount of CPU power they contribute. You signed in with another tab or window.
When you first download the Bitcoin software, you receive a complete copy of the transaction chain which is why downloading can take up to 24 hours. One last request Share on Facebook Tweet this. Incremental compilation for debug. Bitcoin has shown astonishing returns over the past few years, and has caught the attention of all sorts of investors. From there, we have scripts and tactics that we have honed over our experience. Once enough transactions have been carried out, the block is completed and cannot be altered. Mining is a slow but safe method of earning money from Bitcoin and other cryptocurrencies. This digital signature is created using a hashing algorithm and asymmetric encryption. At least, it is the maximum that I want to use to be secure, and to work hapily. It will then begin encrypting the files on the victim's hard drives with AES encryption. Skip to content. As mentioned above, his goal is to get a hash that begins with a certain number of zeros.
If nothing happens, download Xcode and try. Well, I do not know about you, but I do not like to think about security of my data all the time. At that time potential investors assess the project and decide whether to invest in it. Array " ". According to Coveware, ransomware attacks were up in Q1 This file can what stocks does bitcoin impact dogecoin scrypt downloaded via this LINK. Using Bitcoin, you can transfer funds to anyone within seconds and with minimal transaction fees. It is totally illegal to hold Bitcoin in Algeria, Columbia, Nepal, Bangladesh, and several other countries. We all know how to withdraw cash from an ATM and how to buy a pack of gum. This means that the public key required to retrieve the decryption key will be deleted as. VPN Blog Posts. However, XRP is definitely getting more and more traction lately: You can participate in the mining process by donating CPU to the network.
Coveware admits to actually negotiating with scammers. It provides a range of services, including international payments, for these credit unions and is set to introduce a new service called Currentz, which will use XRP. It is up to us to be wise and use it appropriately. Bitcoin aims to solve the problems associated with fiat currencies. This means that the public key required to retrieve the decryption key will be deleted as well. Let us look at some interesting stories where people bought Bitcoin and were shocked later on. A study by ProPublica found that most ransomware solutions providers have one weird trick for getting rid of hackers — paying them off. Array " secret0key ". One last request Share on Facebook Tweet this. That is because there are criminal elements that seek to take advantage of all the excitement and media hype surrounding Bitcoin. Crypto related functions and helpers for Swift implemented in Swift. At least, it is the maximum that I want to use to be secure, and to work hapily. As mentioned above, the blockchain system is applicable to more than cryptocurrencies. So far, the only companies using it are smaller businesses that offer cross-border payments, including money remittance services and one bank. Why To give you the latest crypto news, before anyone else. For your convenience, CryptoSwift provides two functions to easily convert an array of bytes to Data or Data to an array of bytes:. In any case, these mechanisms are in place so that it is only you who are allowed to withdraw or transfer money that you own. The latter is known as a mining pool, and is generally a good idea for those without a lot of hardware.
The ransom increase reflects increased infections of more expensive types of ransomware such as Ryuk, Bitpaymer, and Iencrypt. Decrypting the files. You can change it manually after installation, or use cocoapods-wholemodule plugin. But no one really knows who Satoshi Nakamoto is. With the combination of an ASIC and cheap electricity, you could find it profitable to get into the mining business. You signed in with another tab or window. This will be explained in more detail. In other words, no knowledge is required in order to work fully secured. The private key belongs to one person and no one else has access to it. Say a miner is working on a block. Launching GitHub Desktop Delete unused CI. ICO is an debtcoin cryptocurrency buying antshares with ethereum at which crypto coins are first introduced to the world and have not yet been valued. According to Coveware, ransomware attacks were up in Q1 If people know that they are legally allowed to open a closed safe via all means neccesary, and they just get what is in that safe the moment they succeed, then it how much ethereum can i mine to be productive palm beach bitcoin surely be a challenge? These transactions are carried out according to a set of rules, known as the Bitcoin protocol. Whichever miner manages to do this first gets his block added to the blockchain. Subscribe Here!
When encrypting your data, TrueCrypter will append the. One way to conceptualize this is metaphorically, with the input being flour, sugar, eggs, etc. Instead, all the information is public. JSWorm 2. Storing your coins and private key on a USB drive ensures that attackers and hackers cannot steal your information. ProPublica found that many data recovery firms simply pay the ransom and then charge a premium for their trouble. Before it is executed, the transaction is added to a pool of unconfirmed transactions, known as a mempool i. It partnered with Ripple in November, and has recently announced it will be going live with xRapid in Q1, Launching GitHub Desktop It is recommended to enable Whole-Module Optimization to gain better performance. CryptoSwift Swift versions support Swift 1. One option is to store your coins offline. The private key belongs to one person and no one else has access to it.
Storing your coins and private key on a USB drive ensures that attackers and hackers cannot steal your information. When Specially delivered over 10 days from when you sign up. Non-currency implementations. Only after their money has disappeared do people realize they were duped. Harsh Maurya. It will then begin encrypting the files on the victim's hard drives with AES encryption. Suppose Alice has an online shop that accepts Bitcoin payments. Miners must perform a proof-of-work. JSWorm 2. Losing your private key is like losing your Bitcoin. Because there are constantly new miners with different amounts of computing power, the number of zeros required will periodically change. But how can you convinde people that our encryption solution is rock solid? See more posts. How Bitcoin Stores Information C. Online businesses that accept Bitcoin usually have a button that you click that will automatically bring you to your wallet, allowing you to make the payment from there. You just go to the website and follow the sign-up instructions, and you can get started buying Bitcoin right away. Cryptocurrencies B. Say a miner is working on a block. You will find convenience functions that accept String or Data , and it will be internally converted to the array of bytes. Instead, it obtained decryption tools from cyberattackers by paying ransoms, according to Storfer and an FBI affidavit obtained by ProPublica.
There are also many other ways cryptocurrency is misused: There is a surprisingly small altucher on cryptocurrency poloniex charts explained of threat actors that are active at any given time, so identifying them is relatively straight forward. Incremental compilation for debug. In order to do this, we will look at the problems associated with building a decentralized currency system and see how the Bitcoin system solves. Instead, it rose, beating levels considerably. He has no choice but to randomly guess different numbers until he gets the right hash. The extremely low cost of electricity in China is the reason why the majority of the miner network resides. TrueCrypter will then append the. It partnered with Ripple in and it, too, will focus on the Mexico payments channel. We have vast knowledge and experience dealing with these criminals, and we spend countless hours staying atop their evolving methods in order to provide our clients with protections against all future attackers, not bitcoin bookstore asrock b250 pro4 mining ethereum the one infiltrating their data at the time they come to us. If you succeed to break the encryption, you can read the PDF, scan the QR code with your bitcoin wallet, and wham, one Bitcoin, or Dollar, in your pocket.
Managing Your Wallet C. If you lose your private key, you cannot recover your Bitcoin. You can change it manually after installation, or use cocoapods-wholemodule plugin. This error message will then be used to decrypt the files, fail to do so, but still remove the files related to TrueCrypter. Update gitignore. But because of the way blockchain works, Bob could try to defraud Alice by initiating two transaction messages with the same signature — one in which he sends the money to the Alice, and another in which he sends it to himself at a different address. It is unsure if the sample that we looked at is a hoax, a test ransomware, or just a buggy program as it will automatically decrypt why investors should be wary of bitcoin quantconnect coinbase files by simply clicking on the Pay button. If the person you are sending money to uses the same client as you, often all you need to do is enter the email address to which they linked their account. So you can't use the same GCM instance from encoding to also perform decoding. Unfortunately, the hacks are getting worse and the software necessary is getting more complex.
For them, that means cheaper and faster payments. Popular Stories. In his spare time, he also likes to spread awareness about network security and is the author of the book How Not To Get Hacked. Check Inbox. Adds acknowledgment form. TrueCrypter will then append the. From there, we have scripts and tactics that we have honed over our experience. People are often unaware that their tablets or smartphones may contain important files, which, if you lose your phone or tablet, or if it gets stolen, become accessible to the finders or the thieves. However, XRP is definitely getting more and more traction lately: You're not as safe as you think you are! Get weekly tips on how to stay protected and up to date on what's going on in the cyber-world. For such algorithms, the input shall be padded. If you succeed to break the encryption, you can read the PDF, scan the QR code with your bitcoin wallet, and wham, one Bitcoin, or Dollar, in your pocket.. Reporter Help us understand the problem.
In the Bitcoin system, there is no single authority that controls the data. He would earn more Bitcoin simply mining according to the rules. Cambridge is a cross-border payments provider, founded in Canada, aimed at businesses. Type of integration: A study by ProPublica found that most ransomware solutions providers have one weird trick for getting rid of hackers — paying them off. People are often unaware that their tablets or smartphones may contain important files, which, if you lose your phone or tablet, or if it gets stolen, become accessible to the finders or the thieves. The exact amount has changed over time and decreases as the network grows. Then, the hash needs to be encrypted. Similarly, if someone else gets a hold of your private key, then he or she can withdraw all your Bitcoin. Non-optimized build results in significantly worse performance. By Tim Copeland.
As you recall, a hash is created by performing an algorithm on an input in order to create an output of a fixed length. Who For entrepreneurs and people who like to build stuff. When this happens the shorter branch is dumped, and all the transactions on it are shunted back to the mempool. Best website to make paper wallet electrum transaction check is a growing collection of standard and secure cryptographic algorithms implemented in Swift http: View All Emails. Once the transaction is validated, the cheap good cryptocurrency build an antminer adds it to the newest block. Older branches are unsupported. Drag the CryptoSwift. Find File. You signed in with another tab or window. Only after their money has disappeared do people how much money can one antminer make how much power does antminer s9 draw they were duped. Select Emails. Different cryptocurrencies have different mechanisms for paying miners; some may only pay for transaction fees, while others incentivize them using various other means. We are convinced of the safety of our solution, and as the Americans say: Within the same week, we have seen two ransomware programs accept Amazon Gift Cards as a ransom payment. To give you the latest crypto news, before anyone. In these instances, the next miner who finishes a block can choose which branch he wants to add to. For more serious miners, there is specialized hardware available with high hash 750 ti hashrates monero 760 hashrate that will give the miner better odds of solving a block. Then, the hash needs to be encrypted. Login Username. Using this public ledger, Bitcoin aims to solve a number of problems: Because Web 3.
This means that the public key required to retrieve the decryption key will be deleted as. The master branch follows the latest currently released version of Swift. If it detects one of these processes, it will terminate it. The extremely low cost of electricity in China is how do i transfer bitcoin from kraken to bittrex bitfinex funding at 75 reason why the majority of the miner network resides. Harsh Maurya is a technology enthusiast who has contributed numerous open source and free tools to the public. JSWorm 2. If it is, it will then terminate the process and not continue. This ransomware encrypts your data using AES encryption and then demands. Sometimes "embedded framework" option is not available. At this time it is only checking for the existence of Sandboxie. Go. Online businesses that accept Bitcoin usually have a security clearance and cryptocurrency accidently receive more bitcoins that you click that will automatically bring you to your wallet, allowing you to make the payment from. Dec 2, One last request Share on Facebook Tweet. Here, miners must solve a mathematical puzzle in order to add their block to the existing blockchainbitcoin isnt anonymous real exchange ethereum this puzzle takes some time to solve. Bitcoin Payment Screen.
While this allows the government to promote economic stability through the control aspects of the economy like credit supply, liquidity, and interest rates, it could also lead to the government printing more money than it should — causing hyperinflation. Latest commit May 17, Before it is executed, the transaction is added to a pool of unconfirmed transactions, known as a mempool i. After US Attorney General traced and indicted two Iranian hackers for releasing ransomware called SamSam, authorities hoped the prevalence of attacks would fall. If you need an earlier version for an older version of Swift, you can specify its version in your Podfile or use the code on the branch for that version. From this we again see how proof-of-work — i. Learn more about what is not allowed to be posted. How Bitcoin Stores Information C. Common issues. GCM instance is not intended to be reused. In order to do so she broadcasts two things to the network: Mar 23, CryptoSwift Swift versions support Swift 1. If the person you are sending money to uses the same client as you, often all you need to do is enter the email address to which they linked their account. But how can you convinde people that our encryption solution is rock solid? Subscribe Here! This distribution includes cryptographic software. Bitcoin Payment Screen.
You can use Swift Package Manager and specify dependency in Package. Incremental compilation for debug. From there, we have scripts and tactics that we have honed over our experience. At that time potential investors assess the project and decide whether to invest in it. In other words, every transaction needs to be facilitated by a financial body — e. What if you challenge people to crack the encryption system? The concern, however, is that these efforts are inadvertently funding terrorism. If you find the project useful, please support authors to keep it alive. On the other hand, simply clicking on the pay button will cause it to decrypt these files and then remove itself from your computer. In contrast, you can give anyone your public key. A Ripple leaflet on xRapid listed Viamericas as one of four partners using xRapid but so far it has not been confirmed that this was more than a pilot program.