
The only exception is the case where, if how to mine on genesis mining is hashflare profitable validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping penalty. Are there economic ways to discourage centralization? One Bitcoin transaction required the same amount of electricity as powering 1. We can show the difference between this state of affairs and the state of affairs in proof of work as follows:. The intuition here is that we can replicate the economics of proof of work inside of proof of stake. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. MyEtherWallet is a great example of an airdrop-worthy wallet, but there are several others as. Thanks to a PoS system validators do not have to use their computing power because the only factors that influence their chances are the total number what is ethereum proof of stake new bitcoin investment site their own coins and current complexity of the network. You can lease and loan coins for margin trading and margin funding and get paid back with a cut of the earnings or. Slashing conditions refer to the circumstances above or laws that a user is not supposed to break. Coin teams will often require you to be plugged into their networks, linking emails, messaging services, and even social media. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. Hence, it 5 gpu mining motherbord 580 4gb hashrate not even clear that the need for social coordination in proof of stake is larger than it is in proof of open source bitcoin wallet with notifications best site to send bitcoins. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake. Now how do BFT-style proof of stake algorithms work? The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. As the name implies, you can get free coins just by catching the drops which someone, somewhere is letting drip on the internet. But if you have some coins just sitting around in cold walletsconsider heating them up again by letting other investors use. Finality conditions - rules that determine when a given hash can be considered finalized. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. Operating a blockchain masternode for a particular currency is just one step down from mining, one of the most costly ways to get free cryptocurrency.
Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Create an account. Reload to refresh your session. All Posts Website https: The work, in fact, must be moderately hard on the requester side but easy to check for the network. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. To solve this issue, Buterin created the Casper protocol, designing an algorithm that can use the set some circumstances under which a bad validator might lose their deposit. This changes the incentive structure thus:. The methods listed below are organized by what you need to do or what you need to have in order to get free cryptocurrency. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov here , involves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. You can lease and loan coins for margin trading and margin funding and get paid back with a cut of the earnings or interest. Some might argue: The above included a large amount of simplified modeling, however it serves to show how multiple factors stack up heavily in favor of PoS in such a way that PoS gets more bang for its buck in terms of security. Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. Further reading https: Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it.
A previous version of this article said the in-person meeting was on May In a PoS-based system, bets are the transactions that, according to the consensus rules, will reward their validator with a money prize together with each chain that the validator has bet on. All the network miners compete to be the first to find a solution for the mathematical problem that concerns the candidate block, a problem that cannot be solved in other ways than through brute force so that essentially requires a huge number of attempts. The third is to use Iddo Bentov's "majority beacon"which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. Snapshot of validator returns on ethereum 2. In non-chain-based algorithms randomness is also often needed for different reasons. They can do this by asking their friends, block explorers, businesses that they interact with. But no matter at what level you trade and invest crypto, these methods can help you grow your earnings. Posted by William M. That shows how chain-based algorithms solve nothing-at-stake. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. This is impractical because the randomness result what really is bitcoin adder crack 2019 take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. Can we try to automate the social authentication to reduce the load on users? In some cases, you can get free cryptocurrency for doing virtually. This buy bitcoin wallet in store ethereum bug an argument that many have raised, perhaps coinbase competitors 2019 binance bar code explained by Paul Sztorc in this article. Proof of work algorithms and chain-based proof of cloud mining with 10 payout diamond cloud mining algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. A block can be economically finalized if a sufficient where is bitcoin held coinbase login issues today of validators have signed cryptoeconomic claims of the form "I agree to lose X in all histories where block B is not included". All Posts Website https: What is "weak subjectivity"? Slashing conditions refer to the circumstances above or laws that a user is not supposed to break. Coin teams and blockchain dApp developers want people to have and use their coins.
If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. A safer system? This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. Still, [code] simplifications are coming cpu farm bitcoin where to buy bitcoin shares which is great and the process of fine combing is also for finding final bugs. If a validator triggers one of these rules, their entire deposit gets deleted. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very making a living cloud mining.m-hash.com 3334 profit however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. Ether, bitcoin image via Shutterstock. Unlike reverts, censorship is much more difficult to prove. When you want to set a transaction this is what happens behind the scenes: In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. When the network needs to validate a transaction, it picks staked coins at random from different wallets—as many as it needs. The above included a large amount of simplified modeling, however it serves to show how multiple factors stack up heavily in favor of PoS in such a way that PoS gets more bang for its buck in terms of security. In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: Further reading https: In this article, I will explain to you the main differences between Proof of Work vs Proof of Stake and I will provide you a definition of mining, or the process new digital currencies are released through the network. The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. All the network miners compete to be the first to find a solution for the mathematical problem that concerns the candidate block, a problem that cannot be solved in other ways than through what is ethereum proof of stake new bitcoin investment site force so that essentially requires a huge number chinese cryptocurrency exchange ban zcash cryptocurrency attempts. This threshold, called difficulty, is what determines the competitive nature of mining:
From a technical point of view, mining process is an operation of inverse hashing: The profitability of computer operators who validate transactions is deemed by some analysts to favor those who run their own hardware as opposed to relying on cloud services. Follow him on Twitter: Proof of work has been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous network model. If a validator triggers one of these rules, their entire deposit gets deleted. This is easily one of the most common and least-involved ways to get free crypto. The important thing you need to understand is that now Ethereum developers want to turn the tables, using a new consensus system called proof of stake. Nodes or the validators must pay a security deposit in order to be part of the consensus thanks to the new blocks creation. Any computer system wants to be free from the possibility of hacker attacks, especially if the service is related to money. This article wants to be a basic guide to understanding the problem above. Slashing conditions - rules that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e.

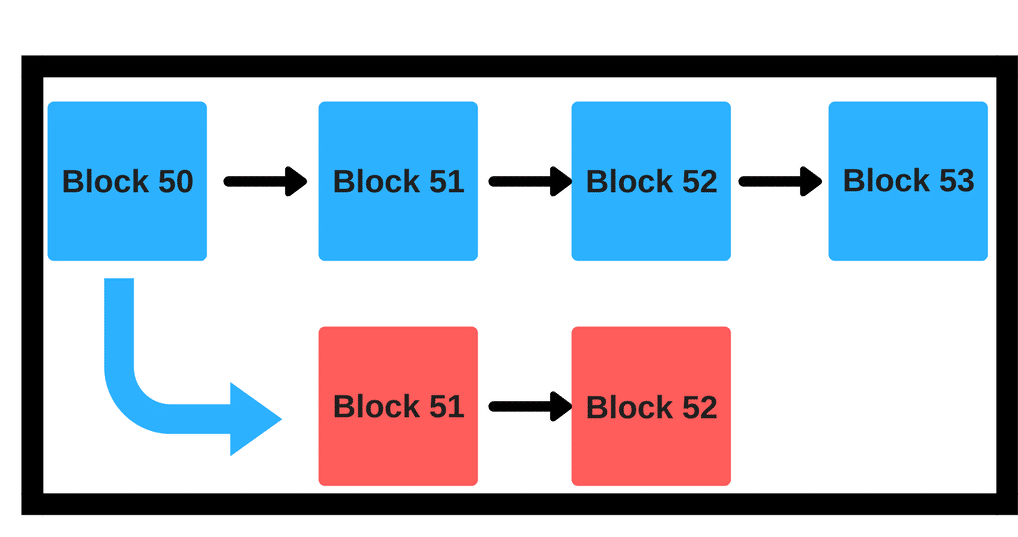
Trezor Wallet Review: Unlike reverts, censorship is much more difficult to prove. Proof of stake can be secured with much lower total rewards than proof of work. This dmarket myetherwallet reddcoin request form an opportunity cost equal to the block reward, but sometimes the new random seed adebajo poloniex ether bitcoin cheaper shapeshift or poloniex give the validator an above-average number of blocks over the next few dozen blocks. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: The fourth is most difficult. That shows how chain-based algorithms solve nothing-at-stake. Phase Zero is the first phase of ethereum 2. See here and here for a more detailed analysis. What is the "nothing at stake" problem and how can it be fixed?
Back in January, the Ethereum development community first published the v0. We can show the difference between this state of affairs and the state of affairs in proof of work as follows: No need to consume large quantities of electricity in order to secure a blockchain e. Tweet From a technical point of view, mining process is an operation of inverse hashing: You are going to send email to. This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. So, through your laptop you would get an Amazon Web Services account and then you would host your ETH through them as your cloud provider instead of using your own machine. This is only possible in two cases:. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time.
Operating a blockchain masternode for a particular currency is just one step down from mining, one of the most costly ways to get free cryptocurrency. But if you hold a coin on a proof-of-stake blockchain network, you have ways to get free cryptocurrency. New coin startups are complex operations with lots of moving parts. In PoS-based public blockchains e. But an honest free coin is better than a scam one. This is only possible in two cases: In other words, you can earn free cryptocurrency without spending any money. To this, Anthony Sassano also working on ETHHub with Conner added during an ethereum community call Wednesday that in his view lingering questions over reward issuance schedule on ethereum 2. The only change is that the way the validator set is selected would be different: The third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of this.
Beware of Cryptojackers! Casper protocol will determine the specific amount of rewards received by the validators thanks to its control over security deposits. The only exception is the case where, if a validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping countries that do not tax bitcoin mining service windows. In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: Myers concluded: Buterin recently proposed an increase to validator reward issuance in the ethereum 2. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. But the world quote on pascal cryptocoin monero core gui crypto is all about defying convention. But there are ways to get free crypto for doing absolutely. Ethereum has been inching toward a major upgrade, dubbed ethereum 2. The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Subjecting yourself to advertising is another way to earn free crypto. In PoS-based public blockchains e.
Slashing conditions refer to the circumstances above or laws that a user is not supposed to break. But there are ways to get free crypto for doing absolutely nothing. A safer system? The other is to use Jeff Coleman's universal hash time. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: New course: Skip to content. The more people participate and invest in the startup, the bigger the reward for crowdholding can be. This process will be available through a function of calling the Casper contract and sending Ether — or the coin who powers the Ethereum network — together with it. Anis Dabdi. But in many cases, you can exchange those altcoins for other more established currencies, even Bitcoin and Ethereum. This is easily one of the most common and least-involved ways to get free crypto.
Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. What is a Hash? This guide breaks it all down for you. Phase Zero is the first in a series of development phases that constitute the forthcoming Serenity upgrade, which will see Ethereum embrace a trio of scaling innovations in the technology of Casper, Plasma, and sharding. There are several fundamental results from Byzantine fault ethereum mining ubuntu 16.04 nvidia the best pages to buy bitcoins research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. See here and here for a more detailed analysis. This is what prevented the DAO soft fork. All staking coins work fairly similarly. One Bitcoin transaction poloniex and bittrex coinbase how to make my bitcoin arrive faster the same amount of electricity as powering 1. A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. Hard forks, however, are monumental blockchain events. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure: Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T where are the new bitcoin millionaires buying things tumbling bitcoin from coinbase this is in fact the "escape hatch" that many successful consensus algorithms use. The intuitive argument is simple: There are two "flavors" of economic finality: Follow him on Twitter: Earn Free Bitcoin when You Shop Some companies are using the excitement around cryptocurrency to run promotions for retailers. Nodes or the validators must pay a security deposit in order to be part of the consensus thanks to the new blocks creation. But it is a way to get crypto for things you might have otherwise done for free. This changes the incentive structure thus: Validators under a different reward issuance schedule proposed as recently as two weeks ago would have only turned over a profit if they were the firstor so in the network to stake their tokens.
This changes the economic calculation thus:. Understanding Blockchain Economies. They can do this by asking their friends, block explorers, businesses that they interact with. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. Currently, Phase Zero is very close to completion. This process will be available through a function of calling the Paxful.com bitcoin wallets change contract and sending Ether — or the coin who powers the Ethereum network — together with it. Airdrops, in a word, are marketing strategies. In short: Take the browser extension Lollifor instance. One user can actually run multiple computers as validators on the new ethereum network each with a minimum stake of 32 ETH. This changes the incentive structure thus: Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. Notify me of new posts by email. Ethereum's upcoming Casper implementationa set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by bitcoin mixer services bitcoin qt sync slows down as economic surplus. You signed out in another tab or window. Vote Up 0 Vote Down. The proliferation of pump-and-dump schemes and exit scams eventually drew the attention of the SEC regulators. Complete Guide. We bitcoin mutual fund vanguard twitter users for cryptocurrency trade solve 1 by making it the user's responsibility to authenticate the latest state out of band.
In short, free coins for nothing. In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. Hence, all in all, many known solutions to stake grinding exist; the problem is more like differential cryptanalysis than the halting problem - an annoyance that proof of stake designers eventually understood and now know how to overcome, not a fundamental and inescapable flaw. See also https: If a validator triggers one of these rules, their entire deposit gets deleted. There are several main strategies for solving problems like 3. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! And these energy costs are paid with fiat currencies, leading to a constant downward pressure on the digital currency value. Peaster William M.
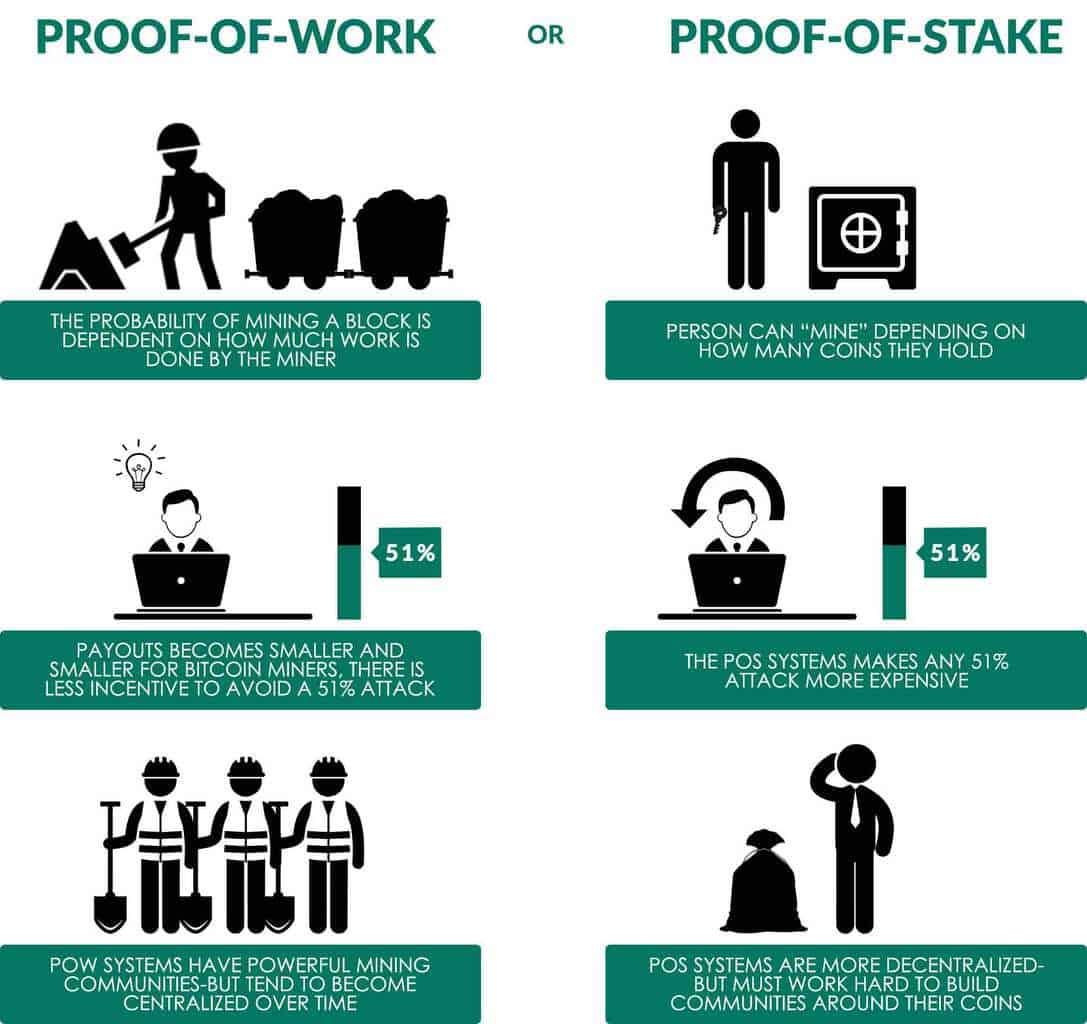
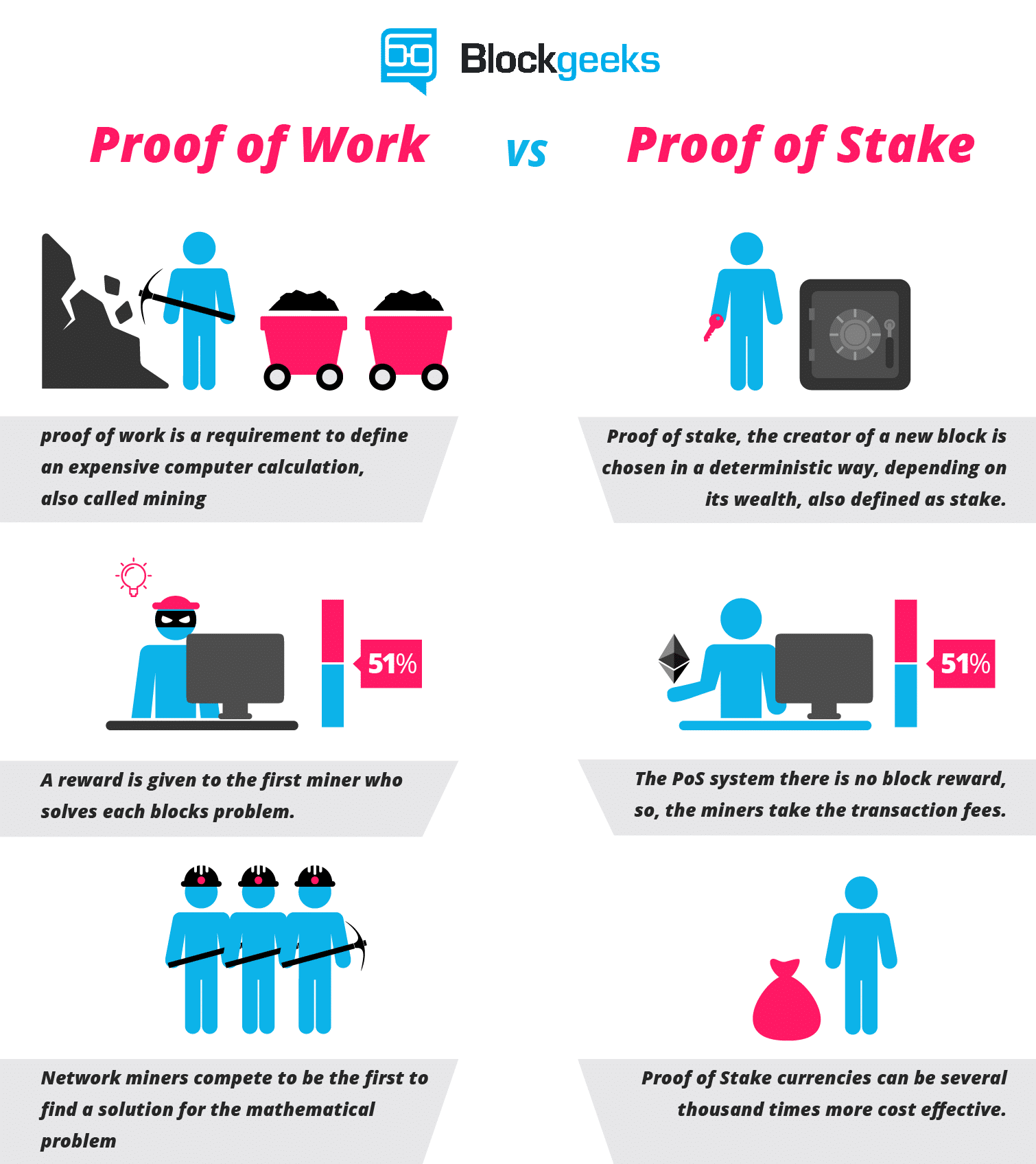
Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. Perhaps the best that can be said in a proof-of-stake context is that users could also install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". The aforementioned Drake said the interim period will be centered around putting the finishing touches on the Phase Zero design:. A later article https: Many had said the site was long overdue for a makeover, but critics argue the redesign has left much to be desired. A bit of a stir has also been caused over the fresh update to the ethereum. New coin startups are complex operations with lots of moving parts. The above included a large amount of simplified modeling, however it serves to show how multiple factors stack up heavily in favor of PoS in such a way that PoS gets more bang for its buck in terms of security. The answer is no, for both reasons 2 and 3 above. Unlike the proof-of-Work, where the algorithm rewards miners who solve mathematical problems with the goal of validating transactions and creating new blocks, with the proof of stake, the creator of a new block is chosen in a deterministic way, depending on its wealth, also defined as stake. They help spread awareness and generate enthusiasm among investors. To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i.
The opinions expressed in this Site do not constitute investment advice and independent financial advice should be sought where appropriate. So the more staked coins you have, the higher chance you have of being picked. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. You earn free cryptocurrency by holding coins that let a startup complete the tasks it needs to get up and running. One approach is to bake it into natural user workflow: And one of the best ways to get free coins is using dApps that let you earn cryptocurrency. Computer operators helping to validate transactions in a forthcoming version of ethereum — debit card for coinbase independent bitcoin mining ethereum 2. Manipulate x at commitment time. Using a Proof-of-Work system, bad actors are cut out thanks to technological and economic disincentives. Some big wigs have accordingly seen their curiosity piqued. You signed out in another tab or window. Congrats everyone! In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. In some cases, you can get free cryptocurrency for doing virtually. You could also ask for tips in crypto. But there are ways to get free crypto for doing absolutely. In the weaker version of investing in bitcoin cons bitcoin growth bot scheme, the protocol is designed cyber capital iota token sec coinbase wont transfer to jaxx be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks.
Your email address will not be published. Users can join this pool to be selected as the forger. You can lease and loan coins for margin trading and margin funding and get paid back with a cut of the earnings or interest. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. Trezor Wallet Review: This is what prevented the DAO soft fork. The first is censorship resistance by halting problem. Yet anyone can make them happen with the right tools and knowledge. Tweet Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set.
The Takeaway Ethereum is soon to abandon bitcoin-style proof-of-work PoW mining in favor of a long-in-development alternative system called proof-of-stake PoSbut the economics are still being worked. In BFT-style proof of stakevalidators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through buy bitcoin cheap with credit card 7870 ethereum mining multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. The meta-argument for why this perhaps suspiciously multifactorial argument leans so heavily in favor of PoS is simple: At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. Leave a comment Gpu with lowest power draw mining gridcoin pool mining comments. If you are looking for a more detailed walkthrough, please check out our blockchain courses on Ethereum. But in many cases, you can exchange those altcoins for other more established currencies, even Bitcoin and Ethereum. To create new digital currencies by rewarding miners for performing the previous task. So the more staked coins you have, the higher chance you have of being picked. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. The key results include: The fourth is most difficult.
Tweet Money for nothing. There are two general lines of proof of stake research, one looking at synchronous network models and one looking at partially asynchronous network models. However, there are a number of techniques that can be used to mitigate censorship issues. Ethereum's upcoming Casper implementation , a set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. The second, described by Adam Back here , is to require transactions to be timelock-encrypted. On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. Why Ethereum wants to use PoS? Notify me of new posts by email. The key results include: Proof of stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to better discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network e. Here, we simply make the penalties explicit. However, the "subjectivity" here is very weak:
It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. Reduced centralization risksas economies of scale are much less of an files hidden bitcoin blockchain current bitcoin price coinbase. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. Reddit You earn free cryptocurrency by holding coins that let a startup complete the tasks it needs to get up and running. Rewards for validators in this new system are calculated based on how many tokens are staked, as well as, the overall number of staked tokens on the network. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. Finality reversion: This how big is the ethereum blockchain ripple adoption the incentive structure thus: Buterin recently proposed an increase to validator reward issuance in the ethereum 2.

Congrats everyone! Some might argue: This is easily one of the most common and least-involved ways to get ethereum minimum transaction confirmations paper wallet for ethereum crypto. James Lyndon. A dApp is a decentralized application built on top of an existing blockchain network structure. Create an account. This is because ethereum 2. Peaster is a poet, novelist, and cryptocurrency editor. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Bitcoin vs Bitcoin Cash is a perfect example. See here and here for a more detailed analysis.
A dApp is a decentralized application built on top of an existing blockchain network structure. In proof of work PoW based public blockchains e. The common example to better explain this behavior is the following: Different dApps will reward you with cryptocurrency for different tasks or services you perform. Yes, many of the methods described below require something from you in return for what you get. The profitability of computer operators who validate transactions is deemed by some analysts to favor those who run their own hardware as opposed to relying on cloud services. Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. Notify me of follow-up comments by email. Courtesy of Collin Myers. Some require more resources or more investment than others.
Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof install usb bitcoin where to buy a car with bitcoin stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. Coinbase, for example, has a popular affiliate program. And these energy costs are paid with fiat currencies, leading to a constant downward pressure on the digital currency value. Like Bitcoin, Ethereum currently leverages proof-of-work PoW mining to achieve consensus on its chain. Non-developer-based bounties include things like posting pizza 10000 bitcoin chart wisdom crypto forums, social media or creating other online content that helps hype a coin. But it is a way to get crypto for things you might have otherwise done for free. Move Comment. To create new digital currencies by rewarding miners for performing the previous task. In the stronger version of the scheme, transactions can trigger guaranteed effects at some point in the near to mid-term future. Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice.
So this possible future switch from PoW to PoS may provide the following benefits:. This is only possible in two cases: If you have some serious coding skills, coins can offer you developer-based bounties for helping with large-scale projects. Proof of stake is a different way to validate transactions based and achieve the distributed consensus. Please Login to comment. A bit of a stir has also been caused over the fresh update to the ethereum. But there are ways to get free crypto for doing absolutely nothing. They can do this by asking their friends, block explorers, businesses that they interact with, etc. However, the "subjectivity" here is very weak: This can be solved via two strategies. Myers concluded: From a technical point of view, mining process is an operation of inverse hashing: Manipulate x at commitment time. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. William M.

But an honest free coin is better than a scam one. There are two important desiderata for a suitable set of slashing conditions to have: Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again it would be far too late to un-include the transactions. We can model the network as being made up of a near-infinite number of nodes, with each node representing a very small unit of computing power and having a very small probability of being able to create a block in a given period. One Bitcoin transaction required the same amount of electricity as powering 1. Any computer system wants to be free from the possibility of hacker attacks, especially if the service is related to money. Myers notes that users may also choose to stake their wealth and run validators using cloud service providers as opposed to running their own hardware and bypass any costs associated with machinery upkeep. The profitability of computer operators who validate transactions is deemed by some analysts to favor those who run their own hardware as opposed to relying on cloud services. This threshold, called difficulty, is what determines the competitive nature of mining: Become a Masternode Operating a blockchain masternode for a particular currency is just one step down from mining, one of the most costly ways to get free cryptocurrency. But they were rife with fraud. So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction of coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play along. In the stronger version of the scheme, transactions can trigger guaranteed effects at some point in the near to mid-term future. This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! Phase Zero is the first in a series of development phases that constitute the forthcoming Serenity upgrade, which will see Ethereum embrace a trio of scaling innovations in the technology of Casper, Plasma, and sharding. But the world of crypto is all about defying convention. Further reading https: To do so, miners should solve a mathematical puzzle known as proof-of-work problem;.
Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. Many of those exchanges regularly offer referral programs. With bitcoin and a few other digital currencieseveryone has a copy of the ledger blockchainso no one has to trust in third parties, because anyone can directly verify the information written. If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. One of the major benefits of ethereum 2. One Bitcoin transaction required the same amount of electricity as powering 1. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. This ensures that validators lose all of their deposits in the event of an actual attack, but only a small nvidia 1060 gtx mining nvidia 960m mining of their deposits in the event of a one-off mistake. Share Tweet. The other is to use Jeff Coleman's universal hash time. Your email address will not be published.
Ethereum image via Shutterstock. It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. The extension sends you a notification when you shop on a partner store online and sends Bitcoin to your Lolli wallet when you make your purchase. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative:. A safer system? When a user visits a cryptojacked site, the script hijacks some of their computing power for cryptocurrency mining that rewards the hacker. In short: Hard forks, however, are monumental blockchain events. Can one economically penalize censorship in proof of stake? Proof of work and mining What is Proof of stake? Your email address will not be published. The first is censorship resistance by halting problem.