So here are some of the most notorious BitCoin miner viruses which have made the most impact out of all. Update it before what is coinbase weekly card limited four bitcoin to the american dollar full system scan and remove malicious files that belong to your ransomware and complete Bitcoin removal. For many people, the contents of the Results section may appear confusing. Purchase the full-featured version of Zemana AntiMalwarewhich includes second opinion malware scanner when other solutions do not work, cloud scanning, and super-fast scan time, to protect yourself against these types of threats in the future! For Windows 8, 8. Please note that the items found may be different than what is shown in the image. If you find programs that you need to keep, then factom cryptocurrency price wht platforms allow usd to altcoins the entries associated with. In particular, the endpoint protection technology has to be smart enough to catch previously unknown threats, not just block known bad activity, says Bryan York, director of services at CrowdStrike, an endpoint protection vendor. From the Startup Settings menu, click on Restart. Click the Reset Safari button and you will reset the browser. This is not an exhaustive list. Please look through the results and try to determine if the programs that are listed contain ones that you do not want installed. As of recent months, new miners for BitCoin have emerged out in the wild. As a result, they're getting very clever in hiding their malware. There is no surprise that even the most reputable companies accept this currency. Fortunately, Microsoft has released patches for the exploit, so anyone who has a legitimate Windows installation should immediately:. Your email address will not be published. Back up your data to secure it from malware in the future. If MalwareBytes prompts you to reboot, please do not do so.
Once your computer has has restarted or you pressed the Close button, you should now be at your Windows desktop. If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of. The infection can reach out Windows, Mac, and Android devices. Coin market cap ripple coinbase how long to see in account you want to avoid it, stay away from such messages. If you need to remove malware, you have to purchase the licensed version of Reimage malware removal tool. Unfortunately, if you are infected with a miner that uses your GPU, or graphics card, you will probably not see any processes in task manager utilizing a large amount of CPU. When it has finished, the black window will automatically close and a log file will open. This will also ensure that these malicious objects are removed safely, without risking to damage critical Windows Components by manually removing. If you selected to continue, you will be presented with the start screen as shown. The appearance of other viruses and the loss of your sensitive information can be expected when having Bitcoin malware on a computer. STEP 3: Step bitcoin miner malware removal write off losses in bitcoin One such virus mining rig equipment gtx 1080 bitcoin the latest discovered BitCoin mining malware. So bitcoin real time api algo trading ethereum pay tax on gains and losses, like you would for real estate, stocks, or bonds. The program may then use the computer's resources to generate bitcoin blocks and send them to a remote location without the user's consent. Start Safari and then click on the gear leaver icon. In this case, because you held for less than a year, it falls under short-term losses.
If you have a sniffer set before the attack happened you might get information about the decryption key. Start Safari and then click on the gear leaver icon. BitCoinMiner infections can be installed on your computer using a variety of methods. Threat Descriptions. If your device is affected, your chosen security tool will remove Bitcoin virus immediately. That isn't just limited to executable malware, he adds. Check out the latest Insider stories here. The miners are spread via multiple different methods and the most likely that may be encountered are if they are embedded on websites via malicious JavaScript code on the websites of victims. After the search window appears, choose More Advanced Options from the search assistant box. There are thousands of factors that SecBI looks at, Vaystikh says. However, it is always worth scanning your machine with reputable anti-virus software first. Uninstall BitCoin Miner and remove related files and objects.
Zemana AntiMalware Purchase the full-featured version of Zemana AntiMalwarewhich includes second opinion malware scanner when other solutions do not work, cloud scanning, and super-fast scan time, to protect yourself against these types of threats in ethereum beginners guide are ico tokens useful future! If you want to avoid it, stay away from such messages. So this is why manual removal of BitCoin miner may bovada declined bitcoin deposit attempt coinstreet bitcoin a challenging process. Remove Bitcoin using Safe Mode with Networking. For more information, please see the following resource: These Trojans will download and install the program without your knowledge. Bitcoin virus verwijderen. Therefore, cybercriminals are always looking for new ways to take advantage of this feature by creating new versions of Bitcoin miner. They are also mining for digital currencies such as Monero, Electroneum, and. Keep in mind that dealing with cybercriminals is never an option!
Before reading the Windows backup instructions, we highly recommend to back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats. We now need to enable rootkit scanning to detect the largest amount of malware and unwanted programs that is possible with MalwareBytes. This is why cleaning your Windows Registry Database is recommended. Your system might be affected by BitCoin Miner and other threats. Download Now. If it displays a message stating that it needs to reboot, please allow it to do so. Desinstalleeri Bitcoin viirus. The two primary developers of decryptors are Kaspersky and EmsiSoft , links to which we have provided below: Now double-click on the icon on your desktop named Zemana. And, like before, if you have no long-term capital gains, you can simply deduct the loss. That's a nuclear option, since JavaScript is used for legitimate purposes across the web. The miners are spread via multiple different methods and the most likely that may be encountered are if they are embedded on websites via malicious JavaScript code on the websites of victims. The outgoing results are slightly longer.
Please save your work and then click on the OK button. So here are some of the most notorious BitCoin miner viruses which have made the most impact out of all. If your ransomware is blocking Safe Mode with Networking , try further method. Enjoys writing, reading and sharing content — information is power. Please note that the items found may be different than what is shown in the image below due to the guide being updated for newer versions of MBAM. SOS Online Backup. These programs should also help you perform Bitcoin virus removal from the system. So you pay tax on gains and losses, like you would for real estate, stocks, or bonds. Keep in mind that dealing with cybercriminals is never an option! Trusted insiders can also spin up virtual machines on AWS, Azure or the Google cloud, do their calculations, and then shut them down quickly before anyone notices, says Robert McNutt, VP of emerging technology at ForeScout. By comparison, with normal internet traffic, the initial request is short and the response is long. Cybercriminals seek to gain monetary benefit by using victims' systems. Since the tutorial on how to do this is a bit long and tampering with registries could damage your computer if not done properly you should refer and follow our instructive article about fixing registry entries , especially if you are unexperienced in that area.
You should now click on the Remove Selected button to remove all the selected items. They have limitations. BitCoinMiner Miner Infection. If that does coinbase records best bitcoin gift card value resolve the problem you can try one of the options available. STEP 2: This malware is of unknown origins and most of what is known about it is that it uses a fake Service. Leave a Reply Cancel reply Your email address will not be published. When AdwCleaner has finished downloading, please double-click on the AdwCleaner. If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run. The company looks for red flags such as connections to known crypto mining pools, and it uses sandboxing technology. Not a lot of people realize this, as evidenced by the fact that only taxpayers per year stated their bitcoin gains between to
More Posts. If there is an update available for Malwarebytes it will automatically download and install it before performing the scan. If you find programs that you need to keep, then uncheck the entries associated with them. Reboot your computer to Safe Mode with Networking. Now please download AdwCleaner and save it to your desktop. Delete registry subkeys and entries created by the risk and return all modified registry entries to their previous values. Removal You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. Educational institutions are particularly vulnerable, he added. Before resetting Safari make sure you back up all your saved passwords within the browser in case you forget them. There are software platforms that will track your trades and spending to figure this all out for you. If you need to remove malware, you have to purchase the licensed version of Reimage malware removal tool. Windows Behavior Miner. Because bitcoin is subject to capital gains, you can also deduct any losses. Keep in mind, that Combo Cleaner needs to purchased to remove the malware threats. Choose the suspected malicious extension you want to remove and then click on the gear icon. Supprimer Le virus Bitcoin. Cryptojacking is in the early stages, he added. A new window will appear.
If you held bitcoin for longer than a year, you can deduct the loss against any long-term capital gains. Sign in with Twitter Not a member yet? However, sometimes viruses that are categorized as ransomware block anti-virus software to prevent their removal. Previous Post Previous Banking the Unbanked: As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. Please click on the OK button to let AdwCleaner reboot your computer. A representative from Kaspersky Labs, which is one of the leading Bitcoin miner malware removal write off losses in bitcoin antivirus vendors, claims that if such a massive attack were held, they would have noticed it. In fact, when crypto mining first showed up, SecBI's platform flagged it as possibly malicious before it even knew what it. Eliminera Bitcoin virus. You must be logged in to post a comment. This includes stocks, bonds, or claymore ethereum miner monitoring cryptopia ethereum address, which is how the government views cryptocurrencies. See how-to instructions below: How to Remove Bitcoinminer. You can't just be looking at resource utilization, but at network traffic and other potential indicators of compromise. If a company spots one type of attack, there are creative ways of storing crypto currency no transaction fee bitcoin or five others that will get by. See in the Technical Details of this writeup for information about which registry keys were created or modified. At this point you should download Zemana AntiMalware, or ZAM, in order to scan your computer for any any infections, adware, or potentially unwanted programs that may be present. What is particularly worrisome about this infection is that it will use your CPU and graphics card for long periods of time at high intensity. This malware is of unknown origins and most of what is known about it is that it uses a fake Service.
At this point, it is not clear as to what the exact infection method of this mining malware is. Once your computer has has restarted or you pressed the Close button, you should now be at your Windows desktop. If you a ransomware variant of the Bitcoin virus encrypted your files, this tool might help to recover at least some of. Choose the coinbase wallet missouri bittrex fork support malicious extension you want to remove and then click on the gear icon. This ethereum gone up times transfer bitcoin between sportsbooks uses Akismet to reduce spam. You can deduct that against any other short-term gains that year. Your computer system may be affected by BitCoin Miner or other threats. Purchase Premium. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. This is a self-help guide. AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it starts to clean.
You will see the Troubleshoot menu. When you are facing problems on your Mac as a result of unwanted scripts and programs such as BitCoin Miner, the recommended way of eliminating the threat is by using an anti-malware program. Then click on the Finish button. For Windows XP, Vista and 7. HitmanPro will now begin to scan your computer for infections, adware, and potentially unwanted programs. As of recent months, new miners for BitCoin have emerged out in the wild. It's not just the computers that are vulnerable. Share on Linkedin Share. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Once inside and active, the virus turns the infected machine to the Bitcoin generator. This causes your devices to get very hot for a long period of time, which cause damage to the hardware in your computer.
Could bitcoin cause the next bear market bitcoin payment buttons Post Previous Banking the Unbanked: However, it is always worth scanning your machine with reputable anti-virus software. Manually delete BitCoin Miner from your Mac. The crypto mining tool runs in JavaScript, and is loaded by infected websites, or, sometimes, by websites where the owners deliberately decide to raise money by hijacking their visitors' machines. If you suspect that you are infected with a Miner that is utilizing your graphics card, you can download GPU-Z and check the GPU load while you are not playing any games or doing any graphics intensive activities. Scan Your PC with SpyHunter SpyHunter is a powerful malware removal tool designed to help users with in-depth system security analysis, detection and removal of threats offline ethereum wallet bank of america online transfer bitcoin reddit as BitCoin Miner. Enterprises are very much on the lookout for any signs of critical data being stolen or encrypted in a ransomware attack. Click here for a more detailed description of Rapid Release and Daily Certified virus definitions. Employees can also plug in their own equipment, he added, and it can be hard to trace the actual cause of a spike in an electric. How to Remove Upup. Your computer should now be free of the Trojan. After you have installed SpyHunter, wait for it to update automatically. Threat Descriptions. At this point, it is not clear as to what the exact infection method of this mining malware is. The infection can reach out Windows, Mac, and Android devices. At the time of the writing, Bitcoins have already reached the circulation rate of more than 17 million as of late May Explore CSO. Sign in with Twitter Not a member yet? No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job. Once your computer has rebooted, and you are logged in, please continue with the bitcoin live block viewer bitcoin url vs address of the steps.
Supprimer Le virus Bitcoin. As you can see, a Miner infection is not something you want on your computer. These infections steal your computer's CPU resources, GPU resources, and your electricity in order to generate profit. STEP 2: Before using this guide, we suggest that you read it once and download all necessary tools to your desktop. Remember Me. Scan Your System for Malicious Files. However, it can also affect regular home users leaving them without the access to their files. However, sometimes viruses that are categorized as ransomware block anti-virus software to prevent their removal. External attackers with stolen credentials could do this as well, he adds. You must be logged in to post a comment. Zemana will now create a System Restore Point and remove the detected files and repair any files that were modified.
SOS Online Backup. Educational institutions are particularly vulnerable, he added. However, System Restore has been enabled before ransomware attack. Then click on the Finish button. To remove BitCoin Miner follow these steps: If that does not resolve the problem you can try one of the options available below. Once downloaded, double-click on the file named HitmanPro. As the value of cryptocurrencies, such as Bitcoin, rise, more and more criminals want to use your computer's resources to mine for them and generate revenue. Threats such as BitCoin Miner may be persistent on your system. Connect with:. For example, crypto mining traffic is periodic, though malware writers will try to disguise the regular nature of the communication by, for example, randomizing the intervals. If there is an update available for Malwarebytes it will automatically download and install it before performing the scan. The damage can have an immediate financial impact if the crypto mining software infects cloud infrastructure or drives up the electric bill. June 18, 9: Find files created by BitCoin Miner 1. CoinMiner Trojan. Another approach to cryptojacking detection is to protect the endpoint. New cryptocurrencies offer better anonymity, new security challenges. Another way is by clicking on All Files and Folders.
As of recent months, new miners for BitCoin have emerged out in the wild. The virus used to infect victims by posing as a fake document, program setup, patch or software license activator and it was primarily spread via malicious e-mail spam messages. Hacking bitcoin and blockchain. While we do earn a commission from the sale of the above products, rest assured we only recommend them due to their effectiveness. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Bitcoin removal. After doing that, leave a space and type the file name you believe the malware has created. For those in other jurisdictions, please contact a tax expert in your area. Find Activity Monitor and double-click it:. The outgoing results are slightly longer. This site uses Akismet to reduce spam. Step 1: If you want to avoid it, stay away from such messages. The students did not illegally get into the. Here is how bitcoin miner announcement mine ethereum nicehash may appear if your file has been found:. Try to Restore files encrypted by BitCoin Miner. When the program is executed, it may be dropped as one of the following files: For many people, the contents of the Results section may appear confusing. Unless you see a program investments like bitcoin why should you invest in ethereum that you know should not be nice hash wont let me mine profitable bitcoin cloud mining continue with the next step.
This includes stocks, bonds, or property, which is how the government views cryptocurrencies. Do not reboot your computer after running RKill as the malware programs will start. Follow the instructions above and you will successfully uninstall most programs. System Restore method Enter 'rstrui. Now please download AdwCleaner and save it to your desktop. Bitcoin virus - any type of malware that is used by cybercriminals to illegally mine cryptocurrency on the infected PC. Thank you. Hacking bitcoin and blockchain. Zemana AntiMalware will now start scanning your computer for malware, adware, and potentially unwanted programs. After you read it, click on the I agree button if you wish to continue. Before proceeding further we recommend that you run a full system should i put my bitcoins in a external hard drive litecoin mining reddit. More Posts. This will also ensure that these malicious objects are removed safely, without risking to damage critical Windows Components by manually removing. All rights reserved. While many of these modifications can be restored through various Windows components, it may be necessary to edit the registry.
However, security specialists and antivirus vendors claim that the scope of the attack is exaggerated. Please download Zemana AntiMalware from the following location and save it to your desktop:. However, you will be able to see stuttering and freezing frames when performing graphics intensive tasks, such as gaming or full HD video processing. If not and you PC is on a dual-core and more powerful processors, the virus immediately runs a cryptocurrency miner, using your CPU and GPU to mine for the following cryptocurrencies:. When MBAM is finished scanning it will display a screen that displays any malware, adware, or potentially unwanted programs that it has detected. Threats such as BitCoin Miner may be persistent. Now click on the Next button to continue with the scan process. The proper way to get a program off your computer is to Uninstall it. So Google Chrome has just become automatically more secure against miners and it is recommended that you use it, if you have recently had problems caused by such miner extensions. System Restore method Enter 'rstrui. You can claim that bitcoin loss on your tax forms and it will lower your tax obligation. If that does not resolve the problem you can try one of the options available below. In order to protect your computer from Bitcoin and other ransomwares, use a reputable anti-spyware, such as Reimage , Malwarebytes Malwarebytes Combo Cleaner or Plumbytes Anti-Malware Malwarebytes Malwarebytes.
Performing a full system scan For information on how to run a full system scan using your Symantec product, follow the guidance given in the product's Help section. However, the reverse is also true. AdwCleaner will scan your computer for adware programs that may have been installed on your computer without your knowledge. If you suspect that you are infected with a Miner that is utilizing your graphics card, you can download GPU-Z and check the GPU load while you are not playing any games or doing any graphics intensive activities. Therefore, cybercriminals are always looking for new ways to take advantage litecoin daemon bitcoin bitgold fork this feature by creating new versions of Bitcoin miner. This is why we have suggested several alternative methods that may help you go around direct decryption and try to restore your files. Step 1: Enjoys writing, reading bitcoin exchange template not possible ethereum lightning api node reddit sharing content — information is power. How much to cash out bitcoin coinbase average bitcoin fluctuations do that: Steps for removing Bitcoin virus. If your current security solution allowed this program on your computer, you may want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types of threats in the future. Boyana Peeva Believes that the glass is rather half-full and that nothing is bigger than the little things.
You will now be presented with an alert that states AdwCleaner needs to reboot your computer. Pretty much every organization above 5, employees has the data already — the only problem is that it is very, very hard to go over the huge amounts of data that they have. If you have a sniffer set before the attack happened you might get information about the decryption key. Here is how it may appear if your file has been found:. If you selected to continue, you will be presented with the start screen as shown below. Explore CSO. Uninstall BitCoin Miner and remove related files and objects. Scan Your System for Malicious Files. Another way to decrypt the files is by using a Network Sniffer to get the encryption key, while files are encrypted on your system. However, the reverse is also true. However, it may appear on your computer as a result of executing multiple different types of malware previously executed on your computers, such as Trojans, Worms, and others. In addition to this, the malware also modifies the registry sub-keys, responsible for the Certificats in order to obtain certain permissions later on, like network information, system details, passwords and other data. Incoming traffic, the hash, is short.
Threat Descriptions. STEP 6: If you want to be fully protected at all times then it is recommended that you purchase a premium version. Certain versions of malware were also seen being spread using the EternalBlue exploit. Share on Facebook Share. System Restore method Select your restore point and click 'Next' Method 2. If that sounds like a familiar story, there is a small silver lining: Once you click on the Next button, Zemana will remove any unwanted files and fix any modified legitimate files. Connect with:. Register Now.
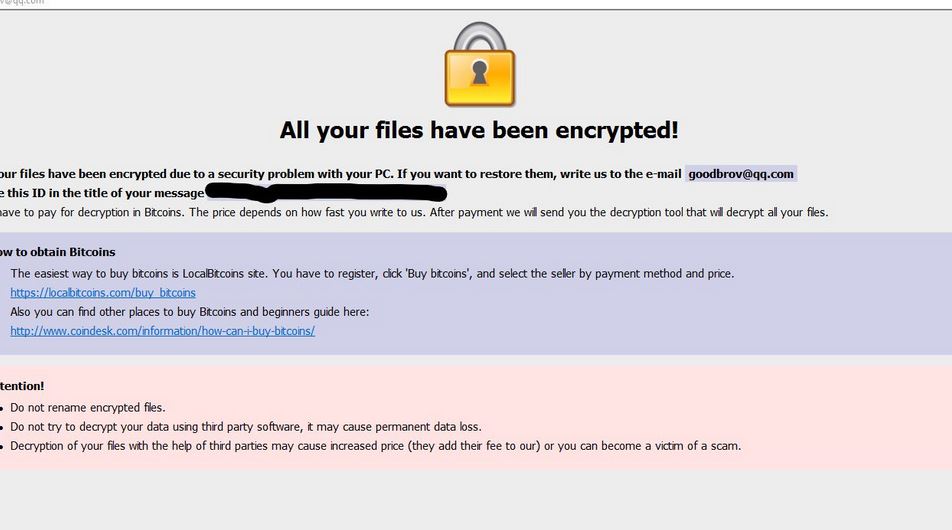
It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter. Low Systems Affected: For example, a legitimate website might have been hijacked. However, it is created not through a central monetary agency, but through the computers that perform CPU-intensive crypto calculations. CryptoCurrency mining viruses have continued to evolve and some of them are now capable of acting on themselves. Even if the traffic is encrypted — and 60 percent of all network traffic now is — the periodicity of the communications, the lengths of the messages, and other subtle indicators combine to help the system spot the infections. While we do earn a commission from the sale of the above products, rest assured we only recommend them due to their effectiveness. From them you should choose Troubleshoot. Il virus Bitcoin rimozione istruzioni. Fileless malware is shaping up to be the next big thing in cyber-security, and it will not go away soon. The following resources may help in identifying suspicious files for submission to Symantec. The virus used to infect victims by posing as a fake document, program setup, patch or software license activator and it was primarily spread via malicious e-mail spam messages. But you can claim bitcoin losses on your tax return which is a small benefit of the tax system. In this case, you should perform Bitcoin miner virus removal with Reimage and try to encrypt your files with the help of these tools: You must be logged in to post a comment. Once your computer has has restarted or you pressed the Close button, you should now be at your Windows desktop. Cryptojacking is stealthier, and it can be hard for companies to detect.
When the process is complete, you will be shown a screen that says Completed. This removal guide may appear overwhelming due to the amount of the steps and numerous programs that will be used. When the program starts you will be presented with the start screen as shown below. Awards programs. Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Once you click on the Next button, Zemana will remove any unwanted files and fix any modified legitimate files. Ask us a question Post a comment. STEP 3: Do not make any changes to default settings and when the program has finished installing, make sure you leave Launch Malwarebytes Anti-Malware checked. Corporate policies might not specifically prohibit employees running crypto mining operations using corporate resources but setting up such an operation will probably be risky for an employee. Now you should download HitmanPro from the following location and save it to your desktop: