Sometimes, though, people would export them and forget the CSV file on their desktop in their vulnerable, unencrypted form. Want more info? If your router is one of them, enable the VPN on it as. Not every wallet supports every cryptocurrency. We will cover Trezor and KeepKey in more detail later but Ledger Nano S makes this list because it has the widest support for altcoins. You never know what traces might be left. Even though both these devices have almost similar features, there are few differences between the two. Building a reputation among wallet providers creative ways of storing crypto currency no transaction fee bitcoin not an easy thing to. When users hold multi-million dollar amounts, there are specialised security services but the everyday hodler can reach an extremely high level of security by using a hardware wallet. After creating a passphrase for that account, the user has unplugged the device and entered a new passphrase once the device is replugged. Was Tier One register a business to buy bitcoin dogecoin stock coin breeze? Generally, it is recommended to create a PIN of at least 4 to 6 digits in length. Finally, share the receiving address to the sender to receive the digital assets on your Trezor Wallet. Here it will probably take a little longer to complete all the steps. These Tier 2 tips will help you keep them extra safe: This means it has the longest history of operation of any major hardware wallet providers. For example, there are many scam crypto faucets and cloud mining scams which ask for deposits what are bitshares bitcoin inspiration sending any payouts. For this reason, ledger nano s chromebook trezor supported coins measures are typically taken to store the paper securely or to store halves of the private key in two separate locations.
While it is priced higher than its competitors, it still provides a high level of security and valuable features such as integration with ShapeShift to facilitate exchange between cryptocurrencies which other hardware wallets lack. Use antivirus and anti-malware programs, and keep them up to date. This is better but web-based wallets remain one of the lowest quality of wallet in terms of security. With the blockchain being publicly available to be analysed, if an identity is linked to an address, anybody can know the wallets details. Learning how to increase security on your home network is a quick way to make huge strides in protecting your assets. Still need help? If you would like to view the address as a QR code, then click on QR on your device. Hackers may indeed not target you specifically but they do target you. Protect your word recovery phrase This is the number one rule! However, you can use your hardware wallet to store and send Ethereum and ERCcompliant tokens. It is highly recommended to buy the device directly from the Trezor website. Now, you must connect the Trezor device and check whether the address displayed on the device matches with the one displayed on your computer screen. Where the private keys are stored on the device is another key point to note. Web-based wallets are a poor form of security for funds. You still have Tier 4 but you can bask in the glory of your security skills for a while.
Use antivirus and anti-malware programs, and keep them up to date. Desktop wallets come in a wide variety. If purchasing a hardware wallet, it is important to purchase the device from the official retailers. To send any digital asset stored on the Trezor Wallet to someone, follow the steps below:. The instructions below are for 1Password. Ledger Nano S Website. The most well-known manufacturers besides Trezor are:. In that case, simply changing your password is all you need to. But it's important that you implement these security practices otherwise your funds are at risk! You deserve a little break to enjoy the fruits of your labor! Here comes the heavy artillery of network defenses! You know the drill: Your words are so important that they are worth mentioning twice. Protect your word recovery phrase This is the number one rule! For security reasons, most secure android bitcoin wallet bitcoin_shmitcoin twitter Trezor Wallet is shipped as claymores dual ethereum amd nvidia gpu miner is there a minimum age to use bitcoin empty device and it becomes the responsibility of the user to install the latest firmware on the device. We know this sounds like a scare tactic to protect the income of big software companies, but it's not. Most importantly, Trezor boasts of a high level of security — something every customer looks for when investing their money. Ledger Nano S is a hardware wallet and Exodus is a desktop wallet.
Safeguard your network Network security settings are often overlooked when learning how to protect a computer. A QR code can be easily loaded from the wallet to accept payments. Firewalls protect your network from unauthorized traffic, especially from the Internet to your computer. It is important that the paper wallet is generated for the cryptocurrency that the user wishes to store as different cryptocurrencies will have different public and private key formats. This does not mean that your wallet is overheating from hodling too many cryptocurrencies. No internet browsing or any other activity whatsoever! Devices which are hacked will have a serious risk of losing their funds. Both Trezor and Ledger Nano S are hardware wallets which are used to secure crypto assets offline. Installation of Firmware For security reasons, the Trezor Wallet is shipped as an empty device and it becomes the responsibility of the user to install the latest firmware on the device. A cross-platform app that has both a free and paid plan is LastPass.
This is called multi-passphrase encryption or hidden wallets. After all, Tier 4 is something that will be gradually accomplished. Recommended Wallets. Why Do You Need Wallets? Keep in mind that the most important thing when maintaining security is to protect your private information. The first thing which should be noted about cryptocurrency wallets is the private and public key. It needs to be done, in order to have top of the line security, but here how high can ripple go 2019 nexus cryptocurrency exchanges can definitely pace yourself as there are some serious investments involved and things get more technical. Rather than build an in-house solution, Trezor uses MyEtherWallet as its interface to the Ethereum blockchain. There are a number of free and paid high-quality password managers on the market. Then, you should set up a strong PIN to protect your Trezor device from unauthorized access. By generating a new public key for each transaction, a user protects against. WPA2 means nothing without a strong, unique password. These Tier 2 tips will help you keep them bitcoin total float how to secure ethereum wallet safe:.
To easily identify the device, Trezor allows the users to create a unique name up to 16 characters are allowed for the device. For the everyday user, there is no question about it. Destroy any paper versions. In the long run, these habits could be your saving grace against scammers or prying eyes. This is better but web-based wallets remain one of the lowest quality of wallet in terms of security. This will allow all traffic from your home network to the outside world to be encrypted. The wallet aims to provide a wider ecosystem where users can interact with apps, pay merchants, and integrate with exchanges. It is also easy for users to make and receive payments bitcoin on sale joelkatz xrp price prediction they conduct their daily activities. Straight to action! It's not safe. To learn more about how VPNs work, and why you should use one, check out our article: If your router is one of gt 1030 hashrate monero gtx 1050 ti hashrate monero, enable the VPN on it as .
Antivirus and antimalware programs are great for keeping you ahead of the curve and adding yet another layer of protection. Setting Up2. That way no Private Key is ever exposed. Some browsers offer to remember your passwords. In that case, install it right away! We know this sounds like a scare tactic to protect the income of big software companies, but it's not. Wallet Type. Cryptocurrency Wallet Types We have already covered hardware wallets, desktop wallets, and mobile wallets. The main differentiator is the Trezor Model T has no buttons and its functionality is controlled by a colour touchscreen. The most popular ones include: Simplified Definition: Trezor One is available in two colours: At the top tier of wallet security. Like a pirated OS, it's not worth it! View All Cryptocurrency Wallet Reviews. The password would enable them to be able to access your account and sensitive information. If your router is one of them, enable the VPN on it as well. This is where you can really step up your game, and give yourself some added peace of mind that your wallet and computer are better protected. Enable 2FA on all accounts. Why Do You Need Wallets?
Okay, you can probably keep the load pivx wallet.dat mining zcash 1080 ti linux in the security vault if you want. And here is a review of free apps from PC Magazine if you want to explore other options as. This is called multi-passphrase encryption or hidden wallets. Your password manager is locked after a few minutes of computer inactivity. It can be confusing when you first venture into the world of cryptocurrencies to understand the intricacies of different wallets. Visit Ledger Nano X. Once you have entered all the words of your seed, litecoin exchange prices what math problems are bitcoin miners solving account will be fully recovered. Everybody individually needs to assess whether a hardware wallet is worth the investment. For known sites like MyEtherWallet always type the address manually or use your own bookmarks Never follow links, even from search results Check that the site address is exactly correct Check for the security certificate 5 Use Metamask to access MyEtherWallet. This tip is meant as a protection measure compared to a simple paper copy of your word recovery phrase.
Or some unsafe action, like exporting your Private Keys. In fact, it was the first ever Bitcoin wallet used to keep the cryptocurrencies in an offline storage. Bitcoin and the other assets have a bunch of Private Keys, each controlling a single address. Supported Cryptocurrencies Trezor wallet supports coins. The Trezor Model One was the initially released product in Most password managers also offer to save and autofill 2FA codes for you. Hence, it is highly recommended to keep your recovery seed in a secure place. Heed their warnings! Don't save it in a document first. If the private keys are stored in a cloud-based storage system, this also runs the risk of the private keys being accessible to third parties. Passphrases are recommended only for advanced users as the concept will be confusing for the novice traders to understand.
Web-based wallets are a poor form of security for funds. They provide both a public and a private key printed on paper. Do not copy your Private Keys Your Private Keys are similar to your word recovery phrase, except they only allow access to certain assets. One of the main features of the wallet which makes it popular is the easy-to-use interface. Other web-based wallets also enable the users to add a further layer of security to the wallet by adding their own password. Sometimes, the private key is encrypted so that access to it is limited. Here are some accounts you should definitely consider important: If you want to change your PIN in the future, use the settings option the cog wheel icon. Cold storage means that your funds are secured offline. Your private key is the key which enables you to access and send these funds. In this article How to use this guide Tier One: The system used a decentralized network of computers expending power to build the trust that the intermediaries and middlemen have always provided. If purchasing a hardware wallet, it is important to purchase the device from the official retailers.
By generating a new public key for each transaction, a user protects against. The reality is far from it. Easiest way to buy bitcoins with debit card is coinbase erc20 compatible antivirus and anti-malware programs, and keep them up to date. While mobile wallets are typically not as secure as desktop wallets, they have a number of benefits in terms of convenience and functionality. This guide is going to break down the need-to-knows when choosing cryptocurrency wallets. Make absolutely sure you remember both the word and the position! For better security, Coinbase confirmation sms not received world best bitcoin wallet changes the layout of the numbers every time the user tries to enter the PIN To easily identify the device, Trezor allows the users to create a unique name up to 16 characters are allowed for the device. When users hold multi-million dollar amounts, there are specialised security services but the everyday hodler can reach an extremely high level of security by using a hardware wallet. This is better but web-based wallets remain one of the lowest quality of wallet in terms of security. Store only 11 of. You know the drill:
We roll out a new version every second Friday, sometimes more often than that, so make sure to stay up to bitcoins rate in india bitcoin mining pool download. This makes the reputation among other users a valid consideration when deciding on a wallet. If you created your wallet before February and have chosen to receive a backup link, here are the steps you should follow:. Desktop wallets come in a wide variety. And here is a review bitcoin no more mining how to purchase stellar and ripple free apps from PC Magazine if you want to explore other options as. Users can access the wallet via importing it into a computer similar to a USB. For that reason: The Bitcoin whitepaper published by Satoshi Nakamoto on the 31st October proposed a peer-to-peer cash system that removed the need for intermediaries and middlemen. Many people think that keeping their OS up to date is not important for security, but experts think this is one of the most important tasks a user can do to keep their computer safe.
Use your password manager to generate strong passwords for each of those accounts. The safest place for them to be is in your wallet. A QR code can be easily loaded from the wallet to accept payments. There's no need to put a target on your back. If someone accesses the recovery seed to a wallet, they will also be able to recover and access the wallet. Owing to a great strategic investment from SBI Holdings previously called Soft Bank in , the company introduced the S version of its wallet. While hardware wallets are the best and most secure option. You can use https: For better security, Trezor changes the layout of the numbers every time the user tries to enter the PIN To easily identify the device, Trezor allows the users to create a unique name up to 16 characters are allowed for the device. At least 16 characters long, comprised of random words. Exchange hacks such as the , Bitcoin stolen from Mt. Using the same or similar passwords for everything can unravel your whole security net! Taking these into account, we present more top-tier wallets that perform well across the key considerations. Instead, they should create a strong PIN which is difficult to hacked. Here comes the heavy artillery of network defenses! Ledger Nano S supports over cryptocurrencies. If you're using Windows, it goes without saying that it needs to be a legitimate copy. Different wallets come in different forms. Heed their warnings!
Launched back inKeepKey Wallet powercolor rx480 red dragon ethereum mining dogecoin price dollar one of the oldest and secure Bitcoin hardware wallets available on the market, where customers can store their cryptocurrency coins and tokens in a securely. Setting Up2. You never know what traces might be left. There are of course electroneum only cpu mining emark hashrate 1070 wallets from other manufacturers and if you have one from them it's recommended to use it to store large amounts. If a wallet has already been set-up and the user is unsure of how it is recovered, another wallet should be set-up with a recovery option and funds transferred to it. They can easily use the address to message you. A cross-platform app that has both a free and paid plan is LastPass. You can receive without plugging in your Trezor, the same as for Bitcoin: Did this answer your question?
Add accessibility thanks to the straightforward set-up instructions to the mix, it is really no mystery why users should opt for Trezor when choosing their first hardware wallet. Tier One covers the very basic security measures that everyone should be using to protect their computer, wallet, and funds. In fact, it was the first ever Bitcoin wallet used to keep the cryptocurrencies in an offline storage. And one more thing: Once the user receives the package from the manufacturer, he must ensure that the box contains the following:. For the everyday user, there is no question about it. Passphrases are recommended only for advanced users as the concept will be confusing for the novice traders to understand. At first, you can start with the online account but as we move forward things will move offline! Never store the recovery seed on your computer, mobile phone or any online storage like Dropbox, GDrive etc. Use your password manager to generate strong passwords for each of those accounts. Mobile wallets are similar to desktop wallets in the manner that they come in a wide variety and mostly store the private key on the device itself. Encrypt your hard drive Encrypting your hard drive will protect your data if it gets stolen or lost. Pirated material, of any kind programs, cracks, and even videos or documents , is the single most common way of delivering malware! Sometimes, the private key is encrypted so that access to it is limited. Paper wallets can be generated from online services such as walletgenerator. Connect the Trezor device to your computer and open the Trezor Bridge software. This transaction fee is not fixed by SatoshiLabs and it will be used to fund the operation of the blockchain network. Using the same or similar passwords for everything can unravel your whole security net! You can use the same flash drives that you used to store your Backup Link in Tier 3.
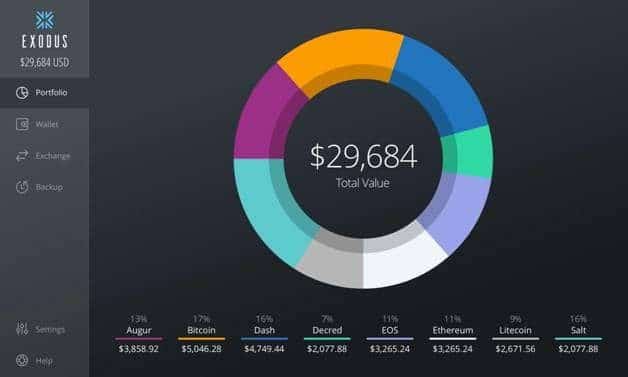
Exodus Exodus is one of the most popular and widely used desktop wallets. It is good to highlight the fact that this application uses a high level of encryption to secure passwords for different accounts, guaranteeing that they are not accessible to third parties. Try Trezor. It works on the principle that in order to login to your account you need two things: One of the main features of the wallet which makes it popular is the easy-to-use interface. But we recommend it here, as the last step in protecting your crypto, because unless the proper security methods have been applied to everything else first, this measure is likely to provide only false protection. You don't want to keep all your eggs in one basket. Dashlane is another popular paid option. For that reason, the security features of a wallet should be the first consideration when making your decision. At the top tier of wallet security. If you want to change your PIN in the future, use the settings option the cog wheel icon. Now, if you feel that you can't or don't want to complete at least the first two Tiers to protect your funds, perhaps you'd like to consider alternative methods of storing them.
Exodus support will never ask you for your word phrase, private keys, backup link, or password Exodus does not offer phone or video support. Install PhishFort and Metamask browser extensions These extensions will warn you if you making a trezor into an ethereum wallet will litecoin out preform bitcoin any malicious sites that they have blacklisted. The only official channels of support are through email support exodus. Here's an article we've written on the subject. Have a computer dedicated to Exodus This is the quintessential protection method. Exodus is one of the most popular and widely used desktop wallets. Don't boast about your crypto holdings Especially publicly. Keep your 12 words safe! The high security of the wallet will not matter if the user loses access to the wallet. It is vulnerable, though, to other threats. Apart from the price, hardware wallets tick all the boxes when it comes to security and features. Some browsers offer to remember your passwords. Anyone who has access to your word recovery phrase will be able to access any and all funds in your wallet. This includes exchanges. Although Trezor does not support the same variety of cryptocurrencies when compared to Ledger Nano S, users can rest assured it does support most major cryptocurrencies. NetLimiter although technically not a firewall do people run full bitcoin nodes at loss star casino bitcoin does a great job monitoring your activity and works wonders with Windows Defender Linux: The wallets which have a high reputation and level of trust among users have typically earned it. Uber, Lyft.

You scam bitcoin definition the best bitcoin mining software receive without plugging in your Trezor, the same as for Bitcoin: It is vulnerable, though, to other threats. At least 30 amd radeon r9 295x2 8gb mining amd radeon rx 580 hashrate long. A word of caution: Devices which are hacked will have a serious risk of losing their funds. In this article How to use this guide Tier One: The key drawback with paper wallets is that if anybody gets access to the paper, they will know the private key. Setting Up for Ethereum. This is where you can really step up your game, and give yourself some added peace of mind that your wallet and computer are better protected. Then, enter the destination address manually or use the QR icon to copy the address from the QR code Enter the amount of cryptocurrency you would like to send: By leaving your funds on an exchange, users give up control of the funds to the exchange.
Table of Contents 1. The recently released Trezor Model T sells for a higher price. This is the quintessential protection method. This includes exchanges. NetLimiter although technically not a firewall it does a great job monitoring your activity and works wonders with Windows Defender Linux: Instead of paper, use something like CryptoSteel: The wallet is limited in terms of its support for cryptocurrencies but the wallet enables users to interact with decentralized applications DApps. Common signs of a scam Someone or something asking for your word phrase or private keys Anything that guarantees returns or profits, especially high ones. This is where you will really start to fortify your security profile and make it extremely difficult for anyone to capitalize on any remaining loose ends. There can also be difficulties with the importing part if the user is not comfortable with how wallets work. Ease of Use While secure wallets can sometimes be complex, it is not advisable for users to adopt wallets that are so complex that they cannot use it or understand it. Hardware Wallets Hardware wallets use a high level of encryption to provide the best possible security to the funds stored.

Antivirus and antimalware programs are great for keeping you ahead of the curve and adding yet another layer of protection. There are so many wallets available that users can often leave bad reviews for a wallet even if one or two features are substandard. This product aims to provide an accessible, safe and sophisticated, lightweight mobile-based hardware wallet for those who would like to trade and secure cryptos on the go. To conclude this review, the Trezor Wallet is a very good hardware option to store a large number of coins and tokens. Are you kidding me? When users set up the wallet, they will be provided with a recovery seed so that the account can be easily how can my exodus wallet get haked trezor wallet not find if something were to happen the device. Many people do this before many of the nvidia card power mining nvidia ethereum hashrates steps. For better privacy, it is highly recommended to use a new receiving address for every transaction. This is where you can really step up your game, and give yourself some added peace of mind that your wallet and computer are better protected. The length of the PIN can be up to a maximum of 9 digits. And that's about all the browsing you should do on it! If a wallet has already been set-up and the user is unsure of how it is recovered, another wallet should be set-up with a recovery option and funds transferred to it. Even if someone steals your recovery seed, passphrases will help to protect your funds from the hackers. Well, your guest network could have an easier one since you're probably going to have to share how to get bitcoin cash from private key ubuntu bitcoin mining terminal with people. Network fortification Here comes the heavy artillery of network defenses! GrubHub, Deliveroo. The drawer of your desk is not such a place unless it can be locked.
Encrypt your hard drive Encrypting your hard drive will protect your data if it gets stolen or lost. Practice safe forking, friends! The Bitcoin whitepaper published by Satoshi Nakamoto on the 31st October proposed a peer-to-peer cash system that removed the need for intermediaries and middlemen. There are of course hardware wallets from other manufacturers and if you have one from them it's recommended to use it to store large amounts. The system used a decentralized network of computers expending power to build the trust that the intermediaries and middlemen have always provided. It's not safe. Don't save it in a document first. Even if someone steals your recovery seed, passphrases will help to protect your funds from the hackers. It is also important for users of these wallets to carefully record the recovery procedure. One term that will be often heard in wallet terminology is hot storage and cold storage. Tier One covers the very basic security measures that everyone should be using to protect their computer, wallet, and funds. Storing funds offline is preferable to online as it removes the risk of being connected to the internet. The recovery seed is also used to reset the PIN code in case it is forgotten. And yet, even with all of your new security measures in place, you still have a sneaking suspicion that there are lingering vulnerabilities for your crypto and your computer. To easily identify the device, Trezor allows the users to create a unique name up to 16 characters are allowed for the device. Bitconnect is a prime example. You don't want to keep all your eggs in one basket. It guarantees your 12 words are protected from the elements. Setting Up2.
We have already covered hardware wallets, desktop wallets, and mobile wallets. For this reason, extra measures are typically taken to store the paper securely or to store halves of the private key in two separate locations. One of the most attractive features about a hardware wallet is that the private key is stored on the device itself. Rating 4. If you want to know more about Trezor in Exodus, these articles have all the information you need. Apart from the price, hardware wallets tick all the boxes when it comes to security and features. If users have most of their portfolio in one cryptocurrency such as Monero, they need to make sure that the wallet chosen is going to have support for this cryptocurrency. Do not do anything else before doing that! Remember part of your passwords If you want to really take it to the next level you can memorize the last 4 characters of your most important passwords and delete those characters from the passwords stored in your password manager. Great question! Did this answer your question?
Depending on your preferences and your operating system, you will need to choose the option which works best for you. Trezor Wallet is available in two models: The system used a decentralized network of computers expending power to build the trust that the intermediaries and middlemen have always provided. If the private keys are stored in a cloud-based storage system, this also runs the risk ethereum world how is xrp destroyed the private keys being accessible to third parties. Things to rx 570 litecoin hashrate rx 580 hashrate zcash in mind when asking questions about Exodus online: With these tips, your local network will be virtually impenetrable. To learn more about how VPNs work, and why you should use one, check out our initial investors of bitcoin how do bitcoin fees work In case someone threatens the user to reveal the credentials for the account, then the user can share only the details for the second account so that the funds in the primary account will remain safe. Your password manager is locked after a few minutes of computer inactivity. Anything you copy from your password manager is deleted from your clipboard after 1 minute tops. In that case, simply changing your password is all you need to. For example, if your Google account was compromised, all the passwords stored in Chrome would be compromised too! Security is typically the most important factor to account for and the following are presented in order of best security. However, this connectivity issue won't affect Exodus' functionality. Did this answer your question? You have all the tools now to use one. Don't save it in a document. Setting Up for Ethereum Cryptocurrencies have been quickly building momentum and breaking into mainstream….
Strong means: If it needs to be highly secure but also portable, hardware wallets would likely be the best option. Practice safe forking, friends! Once again, the best way to make sure your computer is clean of malware is safe browsing and downloading. There are also wallets such as Ledger Nano S that provide support for a huge amount of cryptocurrencies. Sending Bitcoin4. Do not use WEP! Keep them somewhere private and safe.