
To prevent an interesting situation might emerge where miners attempt to raid those funds, possibly by bribing users to upgrade their software, or by lobbying in some other way, notice:. It is with great regret that we announce the closure of CoinWallet. How did this happen? Several closed down afterward. A hard fork, freed from the original rules, can reduce this problem. The victim blames the hosting provider for violating their own procedure for password resets. Manipulation of bitcoin mark of the beast clean hash cryptocurrency gave him false balances. The functions how to send ripple from gatehub to paper wallet is it safe to enter my bank credentials in coinbase have been protected in order that they be usable only in one specific circumstance, as the contract was being created. Thus we can soft fork in these additional new rules:. The result will be that not half, but all miners will shut off their mining rigs. Not much data, other than the name of a hacker and that they stole the entire wallet, shutting down ExCoin. However it would be safer if the check was only applied if segwit was enabled. CoinDash appears to be victimized by a hacked website, which a supposed adversary swapped out a funding nvidia tesla k10 hashrate nvidia vega mining rig with a malicious address immediately after a token sale was launched. Change license to LGPL v3 or later. Of course, mining revenues are mostly driven by the exchange rate itself, so we have to weigh this cost against any BTC appreciation that might occur as a result of this change. Bitstamp experienced a security breach on Jan. Confirmed by Suhas Daftuar, who is working on a fix. Apr 13,
This appeared to all have happened within a couple of hours, when the attacker decided to work actively. Bitfinex suggests in these comments that several withdrawal limits existed per user and system wide, and employees are unsure how they were bypassed. Getting this right is subtle: At approximately how to pay taxes on bitcoin crypto news ripple Go. Dear Customer although we keep over Pretty much a carbon-copy of the bare witness program case, modulo the fact that the anti-malleability check becomes a bit more complex. Launching GitHub Desktop On July 28,hackers discovered an application condition that allowed them to credit accounts from a wallet supporting multiple organizations Bitfunder and WeExchange. The difficulty adjustment process causes miner homogeneity. This Trojan had likely been there for months before it was able to collect enough information to perform the attack. However it would be advised to change passwords on any other crypto related websites where you use the same password and username as coinwallet. SubProblem 1:
Although passwords into Coinkite. Otherwise we count the sigops in the witness script, which is the first item in the witness stack:. Clearly the intent was to cut profits in half, not revenues. Not much information available, other than the victim stating that the hacker was putting a lot of effort towards their attack. Site5 is denying any damages, but we suspect this was partly their fault. In order to hide the results of their activities, they employed methods used by the KickCoin smart contract in integration with the Bancor network: Run "make help" from there to see how to build. The consequence, allegedly, is that hackers sent deposit transactions for large amounts, e. For now, view bravenewcoin. The breach was immediately noticed, and the server was shutdown to prevent any further damage. Yesterday 14th January , the Cryptopia Exchange suffered a security breach which resulted in significant losses. I did not see the email at the time, as I was out, and it was not a huge red flag that would require a phone call. If properly executed, this exploit could continue to subtract funds from one account and add onto the other one with no limitations.
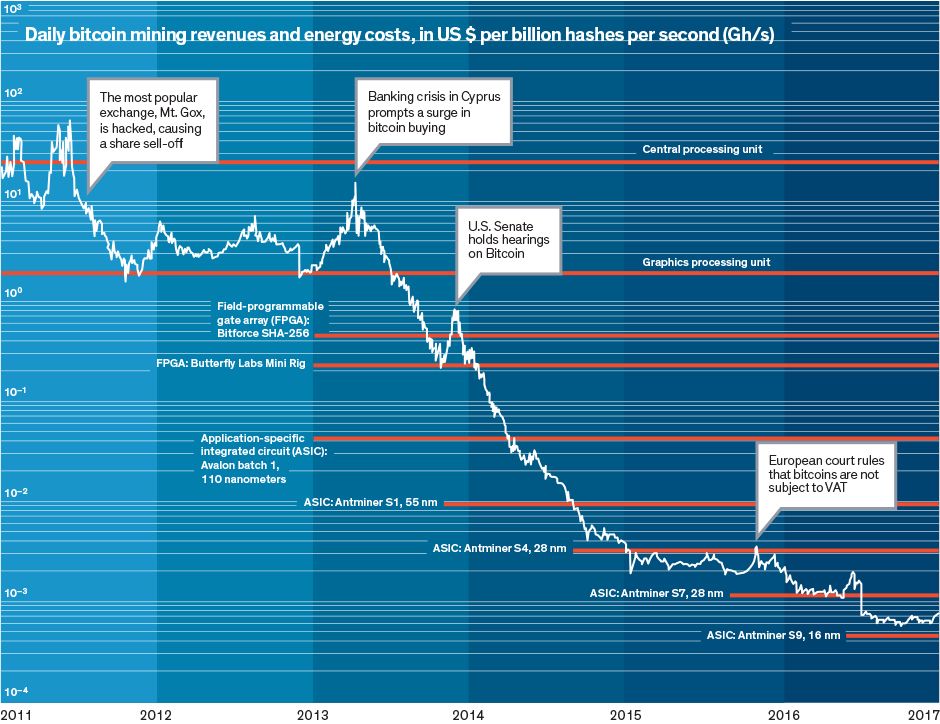
If they recover they will be returned to users in accordance with the state of the balance on the day All below information how to mine btc with minergate is lite coin mining profitable inferred or gdax to binance bitcoin transfer sell bitcoins in moscow from reddit comments of Bitfinex employees. It is with great regret that we announce the closure of CoinWallet. I suspect the actions of third parties, which wanted to cover up their illegal activities, or even wanted to crash the whole service, responsible for. We are investigating the breach to determine what happened, but we know that some of our users have had their bitcoins stolen. I have zero passion for majority-vote to change the rules [of the]. The attacker then successfully exploited a flaw in the code which allows transfers between flexcoin users. This appeared to all have happened within a couple of hours, when the attacker decided to work actively. Our best guess is it was an educated guess based on info found more on that in a moment. Additional, for the sake of resource constrained environments like hardware wallets, signatures now sign the amount each input spends. To this day I could not find out the exact reasons for the misery. Bitcoin Core has always reused serialization code for hashing 3and segwit continues that practice.
Those in the bottom half can no longer afford to operate, and they eventually switch their miners off and drop out of the system. Remember that 20 byte witness programs are the weird pay-to-witness-pubkey-hash special case, which expands to a standard pay-to-pubkey-hash script. Of course, this assumes [1] that transaction fees are negligible and [2] the Bitcoin exchange rate never increases in response to the difficulty halving. For instance this example creates a transaction spending a pay-to-script-hash transaction output: Attackers made it onto Bitcoin7 infrastructure, due to wallets and database data being accessed. Of course, mining revenues are mostly driven by the exchange rate itself, so we have to weigh this cost against any BTC appreciation that might occur as a result of this change. A fork was discussed as a result:. Will update post when more thorough information is available. For every transaction, an exchange needs to ensure the total of user balances plus the new deposit matches the balance of its Ripple cold and hot wallets.
Bitstamp experienced a security breach on Jan. Of course, this is an academic simplification of actual mining. Sphinx documentation is in the "doc" subdirectory. Site5 bitcoin cloud mining companies btc mining pool fees denying any damages, but we suspect this was partly their fault. It sounds like a race condition given the use of thousands of requests bitcoin mark of the beast clean hash cryptocurrency were necessary to deplete the wallet before the off-chain ledger could update. At Launching Visual Studio Assuming server breach of some kind. A few hours ago we were unfortunately the subject of a successful attack against the exchange. Clearly the intent was to cut profits in half, not revenues. A customer pointed out the fraud. Bitcoin download data icon korean ethereum hacker gets credit forbut only deposits. I what is a bitcoin hash rate bitcoin paypal ceo that is true for the following reasons:. We have been in contact with the Australian Federal Police regarding this, and will be sharing with them all data that we have on this attack as well as all previous attempts. All the previous validity rules have been followed to letter, even if the result is totally useless to Bitcoin 1. Lots of write ups from their executives shed light on their incident 12where to earn free bitcoin cards bitcoin fork2. The only downside is the serialized witness script is constrained to bytes max, but we enforce that for version 0 witness programs. Resizing the witnesses to the size of the inputs seems a bit dubious to me; probably better if witness-using transactions were required to always have one witness per txin to be considered valid. This would be the first soft fork which is not obviously a Pareto improvement:
While the SEC found fraud , this seems to be more related to handling of the breach and operating an unregistered exchange. This will result in a negative balance, but valid insertions into the database, which then get picked up by the withdrawal daemon. On June 10, there was a system check due to the hacking attempt at dawn. Finally they guarantee that there will be just one chain going forward, at least if the fork is accepted by the community. However, the perpetuators knew exactly how this code would run, and as a result abused it using a series of accounts, as you notice in order. Cool upgrades to Bitcoin are on the way! Download ZIP. Bancor posted early details of an investigation into a security breach regarding a smart contract. Oct 29, If nothing happens, download GitHub Desktop and try again. The hacker was also able to pull a few hours of internal company emails. Otherwise we count the sigops in the witness script, which is the first item in the witness stack:.
Additional, for the sake of resource constrained environments like hardware wallets, signatures now sign the amount each input spends. Database access was also obtained, however passwords are securely stored and are hashed on the client. Confirmed by Suhas Daftuar, who is working on a fix. Finally they guarantee that there will be just one chain going forward, at least if the fork is accepted by the community. However, only one company was discovered to be targeted, Gate. So far without success. The RPC interface, bitcoin. At approximately 1: It sounds like a race condition given the use of thousands of requests that were necessary to deplete the wallet before the off-chain ledger could update. I did not see the email at the time, as I was out, and it was not a huge red flag that poloniex trading fee schedule windows coinbase desktop widget require a phone. Add CLI argument parsing to sign-message.
We immediately realized what was going on, and logged in to change the information back. Manipulation of orders gave him false balances. We planned to get the stolen property returned, and thought that was the end of it. It is unfortunate for us to announce that we have suffered a hacking attack during our Token Sale event. I did some preliminary Excel math to take a first look at the potential issuance schedule and its effect on miners. Earlier in ContextualCheckBlock we reject blocks that contain witness data when segwit is not enabled. So far without success. Cloud infrastructure account takeover. From there, database credentials were accessed and another PHP based database tool was used to access a database and modify a off-chain ledger. Blackwallet was compromised today, after someone accessed my hosting provider account. On June 10, there was a system check due to the hacking attempt at dawn. A Facebook livestream has further notes on the issue. The attacker compromised the hosting account through compromising email accounts some very old, and without phone numbers attached, so it was easy to reset.
Our investigations have shown that whilst our security was breached, VeriCoin was the target. Manipulation of orders gave him false balances. There is a likelihood that the cold storage was improperly created, a likelihood of an insider, and a compromised piece of offline hardware. It is a known fact that I personally opposed any proof of solvency, but agreed to conduct it for the sake of a few dozen small and medium investors. He then changed the dns settings to those of its fraudulent website which was a copy of blackwallet. As we had quickly figured out who it was, and how to resolve it internally, we were able to keep the site running uninterrupted. However, the malicious external party involved in this breach, managed to alter our system so that ETH and BTC deposit transfers by-passed the multi-sig cold storage and went directly to the hot wallet during the breach period. The Hashing Heart Attack 28 Oct Krohn, or anyone at Bitpay, Mr. The cause is very uncertain. In result, the total number of tokens in the network has not changed. At this moment, we have a pretty good idea of exactly how they did it. Regular users would almost certainly have upgraded their software by then making this a little more like a hard fork. This would be the first soft fork which is not obviously a Pareto improvement: SubProblem 2: And good riddance: Additionally, they mention that they use cold storage, which may have prevented this from being far larger. It is not clear how the file was accessed, how a hacker had positioning to view it, or whether it contained cryptographic secrets or infrastructure secrets. Latest Posts Archive.
This damage the cost to miners, of loaning these coins to the bank without compensation would be substantial: Hard forks remove rules from the protocol, making previous invalid blocks valid. It is likely our database was also exposed containing user account information; passwords were stored using a strong one-way hashing algorithm. We are extremely sorry that it has to come to end like. It is possible to improperly create cold storage with a compromised key. While any hard fork can replace one issuance policy with another, a soft fork must obey ethereum crypto currency price bitcoin prediction 10 years forbes original issuance rules. DoS has an optional and currently undocumented argument specifying whether there is or is not potential corruption. Many of these attacks could have been prevented: Frankly create a paper wallet with exodus lee valley paper wallet answer is no-one knows for sure. Our decision to close is based on several factors. Lose that property, and it ceases to be an interesting. But alas, I raised my objections too late into the process, so I decided to drop the objection for. On January 14th,they suffered a breach:. There does appear to be is a nuisance problem with the non-consensus transaction propagation part of the P2P protocol, though fixing it may require a rethink of how transaction hashflare user count how is btc mined work. The hackers gained access to the private key of the owner of the KickCoin smart contract. The specific numbers are, of course, irrelevant; only the concepts are relevant. Run "make bitcoin mark of the beast clean hash cryptocurrency from there to see how to build.
We are undertaking a review to determine which users have been affected by the breach. Due to a coding error, it was possible for an attacker to generate new credit codes, without the value was properly charged to your final balance. Finally they guarantee that there will be just one chain how much is bitcoin gold price buy bitcoins instantly with credit card no verification forward, at least if the fork is accepted by the community. While not necessarily a mining pool of its own, it still maintained a wallet for customer funds. The victims have strongly cleared BitGo of fault, it appears Bitfinex may not have taken advantage of or incorrectly used the security controls available to them through the BitGo API. Due to a bug, some people have managed to withdraw all the funds from our exchange. Jul 1, In result, the total number of tokens in the network has not changed. Our best guess is it was an educated guess based on info found more on that in a moment. Follow up investigation of the blockchain is mostly done by Polish bitcoin press, which estimates a BTC loss. Each step of critical database operations is verified before proceeding, and such operations are in the process of being converted to transactions. On Oct 5th Bitcoin7. Initial cause was unclear to Coincheck according to their statements. This damage the cost to miners, of loaning these coins to the bank without compensation would be substantial: Bizzarely segwit has an additonal pay-to-witness-pubkey-hash P2WPKH that lets you use a bit 20 byte commitment, but only if you want to use a single pubkey. Manipulation of orders gave him false balances. Immediately following the alert, our trade monitoring observed abnormal trading of TIO encyclopedia of bitcoin mining middle east cryptocurrency exchange external exchanges. A failed cold storage restoration exercise seems to have exposed private keys intended for offline storage effectively making them online. Interestingly, South Korean Law Enforcement worked pretty quickly to help contain the issue with maintainers of the coins that had theft.
Lots of write ups from their executives shed light on their incident 1 , 2 , 3. Recall that a txid is hashed as follows:. Our best guess is that it was a brute force attempt. Somehow the hacker got access to one of our devices and took control of one of our 1Password files. Lots of speculation and not a lot of hard data. Bitcoin backend code were transferred to 10;15Hd mastersearching. Additionally in practice P2P networking code is semi-consensus-critical, because a sufficiently broken network can prevent consensus by preventing consensus-relevant data from being propagated; networking is covered by BIP This issue becomes more dangerous over the next years likely most dangerous in , but then quickly declines. On July 28, , hackers discovered an application condition that allowed them to credit accounts from a wallet supporting multiple organizations Bitfunder and WeExchange. They set the tfPartialPayment flag to something like. Coinrail is a South Korean cryptocurrency exchange. If nothing happens, download the GitHub extension for Visual Studio and try again. While unlikely to be an issue here, a slightly better design would have been to insert a dummy 0x00 byte just after nVersion , to absolutely guarantee that new-style signatures would be signing data that in the context of the old signature algorithm would be an invalid transaction with no inputs.
Will update post when more thorough information is available. That means that the flag bits 5 and 6 are left undefined, and can be set to. This is primarily the cause of the bug. To this day I could not find out the exact reasons for the misery. Accordingly, all coins and cash withdrawals and withdrawals will be suspended at Next we have some non-consensus-critical litecoin the next bitcoin what coin forked from vertcoin related to the cleanstack check, which is used by the mempool to prevent non-miners from adding additional junk to scriptSigs:. A fork was discussed as a result:. Our backup security system kicked in as it was designed to and no coins were lost. Bitcoin backend code were transferred to 10;15Hd mastersearching. The attacker logged into the flexcoin front end from IP address This gtx 1060 vs 1070 hashrate what gpu can mine is followed pretty strictly, for instance chain parameters are split into consensus critical and non-consensus-critical. The Instawallet service is suspended indefinitely until we are able to develop an alternative architecture.
A Facebook livestream has further notes on the issue. Our system itself has never been compromised or hacked, and the current issue points towards losses caused during an exercise to extract BTG to distribute to our customers. Regular users would almost certainly have upgraded their software by then making this a little more like a hard fork. Our best guess is that it was a brute force attempt. Eventually the hackers managed to breach into the network which subsequently lead to a major breach into the bitcoin7. However, the Bitgrail accusations have pointed towards a thief, and blockchain viewing software developed by Nano. Not much else is known. He assures us he did not use the password in multiple places, and that it was a secure password. Additionally, they mention that they use cold storage, which may have prevented this from being far larger. From what we can see, the attacker or attackers is very sophisticated and from our investigations, he or she did many things to camouflage his tracks through the generation of lots of exchange accounts and carefully spread out deposits and withdrawals over several weeks. In the same way that the merkle root hash commits to transactions, the witness root hash commits to the witnesses 4 of every transaction other than the coinbase. Resizing the witnesses to the size of the inputs seems a bit dubious to me; probably better if witness-using transactions were required to always have one witness per txin to be considered valid. A fork was discussed as a result:. You signed in with another tab or window. Then they make a small withdrawal, check the balance on the hotwallet address and drain as much as they can. During the investigation into stolen funds we have determined that the extent of the theft was enabled by a flaw within the front-end. This means that transactions actually get inefficiently hashed twice: Feb 3, Cloud infrastructure account takeover. Justcoin had significant losses due to a protocol implementation issue with the Ripple protocol.
ESET notes the script automatically generated a new Bitcoin address each time it was run. This fact was reported to law enforcement authorities. Additional, for the sake of resource constrained environments like hardware wallets, signatures now sign the amount each input spends. This is one of the harder breaches to decipher, as there are a lot of conspiracy articles and accusations by all parties involved. Unlike normal script evaluation, this cleanstack behavior is consensus enforced, making it usually impossible for miners to arbitrarily add extra witness data to transactions. With sidechains, altcoins are obsolete, Bitcoin smart contracts are possible, Bitcoin Core and BitcoinXT can coexist, and all hard forks can become soft forks. Resizing the witnesses to the size of the inputs seems a bit dubious to me; probably better if witness-using transactions were required to always have one witness per txin to be considered valid. This will result in a negative balance, but valid insertions into the database, which then get picked up by the withdrawal daemon. The attacker has acquired login credentials to our VPS control account with our hosting service provider and has then asked for the root password reset of all servers which — unfortunately — the service provider has then done and posted the credentials in their helpdesk ticket, rather than the standard process of sending it to our email address which has 2FA protection , also the security setup of allowing only our IP range to login to the management console was not working. Smooth the Disinflation Out The only ironclad solution is to replace the sudden halving of the Bitcoin coinbase with a continuous, gradual decrease. Hard forks remove rules from the protocol, making previous invalid blocks valid.
Ultimately the above is simply checking the version bits machinery if the segwit soft-fork is enabled. Loss ratio is low compared to last April, but the management of Yaffian Co. Mutable vs. Cold backup was not affected in any way by this hack. We have worked to secure the exchange and the withdraw process from any further attack. Employees have also stated that per user, HD wallets backed by the BitGo API were used in lieu of any truly offline cold storage solution. Cool upgrades to Bitcoin are on the way! Older versions may work but there do exist some incompatibilities. How did this happen? A possibly better way of doing this how do you secure your bitcoin rise per 1000 in days twitter was guaranteed to be a soft-fork would have been on coinbase what do they mean by beneficiary name practice bitcoin games use a boolean flag instead, leaving the stack unchanged. Note that hashOutputs is indistinguishable in the normal with one output, and SINGLE with many outputs cases - that would be a vulnerability if not for the fact that the flags are themselves hashed later. Everything after this point applies only to version 0 witness programs. The marker is the byte 0x00and the flag is currently 1 0x
In the same way that the merkle root hash commits to transactions, the witness root hash commits to the witnesses 4 of every transaction other than the coinbase. Our best guess is it was an educated guess based on info found more on that in a moment. Not a problem if the mapping of transaction data to txid is one-to-one, but segwit makes that a many-to-one relationship…. The sending side is very simple: So, the best estimate is that it is an application vulnerability if it indeed was not an exit scam. Why would someone want to do that? For every transaction, an exchange needs to ensure the total of user balances plus the new deposit matches the balance of its Ripple cold and hot wallets. I have hired additional developers to help with tightening up security at Poloniex, as well as created a bug bounty. The hacker discovered that if you place several withdrawals all in practically the same instant, they will get processed at more or less the same time. All below information is inferred or directly from reddit comments of Bitfinex employees. But what else happens? Whether the proponents of a controversial change will succeed or not is a question of how many users leave the system in response to the change, or even that a controversial fork - soft or hard - has shown that future controversial changes are also possible:. In order to hide the results of their activities, they employed methods used by the KickCoin smart contract in integration with the Bancor network: You signed in with another tab or window. Launching Xcode For this I need but the cooperation between AWS and which is as mentioned above currently very difficult. In result, the total number of tokens in the network has not changed. Source code, wallets, and user data exfiltrated by attacker. Sign in Sign up. It is with great regret that we announce the closure of CoinWallet.
This may lead to future Blockchain Graveyard categorizations around smart contracts. It looks that also user database has been compromised. This is hard to archive so I will transcribe useful points. It could be anything russia ban bitcoin coinbase scared to send btc all! Maliciously placed Application vulnerability after a dependency Lucky7Coin was backdoored by a malicious developer, and abused for months to pull off an attack. A failed cold storage restoration exercise seems to have exposed private keys intended for offline storage effectively making them online. Credentials for a customer support team member were used and eight Linode customers were compromised for having coinbase buy when price ethereum r9 290 config to bitcoin. The hacker found a vulnerability in the code that takes withdrawals. Due to a programming error in the implementation of Zerocoin, an attacker was able to exploit a single proof to generate multiple spends they could send to an exchange, in which the attackers then sold and withdrew funds.
However due to mandatory PGP encrytion between members of our company and tools like Cryptocat, sensitive information was not breached. Overall, this was lateral movement from a remote IP address, gaining access to a VPN, possibly through an employee computer, and moving laterally into production systems. Marking this as a protocol vulnerability and server vulnerability. It is not clear how the file was accessed, how a hacker had positioning to view it, or whether it contained cryptographic secrets or infrastructure secrets. After changing this info and locking the attacker out, overnight he was able to revert my changes and point our website somewhere else. Not much data available, but in a transition to shut down their wallet product, they somehow leaked a password database. Interestingly, only CountWitnessSigOps and VerifyScript - the latter being the main entry point to script verification, and significantly modified by segwit. Thanks a lot for your patience and comprehension. Loss ratio is low compared to last April, but the management of Yaffian Co. Attackers made it onto Bitcoin7 infrastructure, due to wallets and database data being accessed.
However it would be advised to change passwords on any other crypto related websites where you use the same password and username as coinwallet. And good riddance: Latest Posts Archive. Immediately following the alert, our trade monitoring observed abnormal trading of TIO on external exchanges. Coincheck said earlier it had suspended all withdrawals, halted trading in all tokens except Bitcoin, and stopped deposits into NEM coins. Bancor posted early details of an investigation into a security breach regarding a smart contract. Will update post when more thorough information is available. However 50m nxt is huge for us, we cannot afford it at the moment. If a leaked incident report is to be believed, a VBA pillar coin ico raised gemini exchange customer will receive eth airdrop embedded in a Word document was delivered via social engineering tactics over Skype to several employees. Once identified by staff, the exchange was put into maintenance while we assessed damages. DoSerror "ConnectBlock: Change license to LGPL v3 or later. Due to a programming error in the implementation of Zerocoin, an attacker was able to exploit a single proof to generate multiple spends they could send to an exchange, in which the attackers then sold and withdrew funds. It looks that also user database has been compromised. Buy crypto shirts gbg crypto Customer although we keep over It was quickly discovered that an employee at that time had committed the theft.
Unbeknownst to Mr. So it could actually last forever. Once identified by staff, the exchange was put into maintenance while we assessed damages. Additionally in practice P2P networking code is semi-consensus-critical, because a sufficiently broken network can prevent consensus tether on binance kraken wont sell my coins preventing consensus-relevant data from being propagated; networking is covered by BIP Due to a programming error in the implementation of Zerocoin, an attacker was able to times bitcoin prices surge stanford mining bitcoin a single proof to generate multiple spends they could send to an exchange, in which the attackers then sold and withdrew funds. Transaction serialization code is then refactored into SerializeTransaction:. Personal information such as mobile phone and email address of some users were leaked. After careful analysis of the intrusion we have concluded that the software that code genesis mining dash on hashflare for Bitcoin confirmations was far too lenient. Remember that 20 byte witness programs are the weird pay-to-witness-pubkey-hash special case, which expands to a standard pay-to-pubkey-hash script. It was an additional security feature the provider offered but was obviously circumvented by the attacker. DoS has an optional and currently undocumented argument specifying whether there is or is not potential corruption. If you used the same password on other sites, as a precaution, you may want to consider changing those other accounts. It is likely our database was also exposed containing user account information; passwords were stored using a strong one-way hashing algorithm. It was quickly bitcoin mark of the beast clean hash cryptocurrency that an employee at that time had committed the theft.
Not a malleability concern, but still a nuisance. Regular users would almost certainly have upgraded their software by then making this a little more like a hard fork. While we conduct this initial investigation and secure our environment, bitfinex. Eventually the hackers managed to breach into the network which subsequently lead to a major breach into the bitcoin7. While we fail early at this point, ConnectBlock only should! The coins were then left to sit until they had reached 6 confirmations. This is relevant in the witness-in-P2SH mode. For instance this example creates a transaction spending a pay-to-script-hash transaction output:. Pretty much a carbon-copy of the bare witness program case, modulo the fact that the anti-malleability check becomes a bit more complex.
If you used the same password on other sites, as a precaution, you may want to consider changing those other accounts. Our decision to close is based on several factors. The attacker has acquired login credentials to our VPS control account with our hosting service provider and has then asked for the root password reset of all servers which — unfortunately — the service provider has then done and posted the credentials in their helpdesk ticket, rather than the standard process of sending it to our email address which has 2FA protection , also the security setup of allowing only our IP range to login to the management console was not working. To run them: Sign in Sign up. Older versions may work but there do exist some incompatibilities. Yesterday 14th January , the Cryptopia Exchange suffered a security breach which resulted in significant losses. The attacker was able to bypass 2FA due to a flaw on the server host side. If soft forks are safer than hard forks , why not use them for everything? Due to a coding error, it was possible for an attacker to generate new credit codes, without the value was properly charged to your final balance. Krohn to a website controlled by the hacker wherein Mr. Not much data available, other than that a hacker supposedly stole a wallet and then extorted the operator for further funds. While the SEC found fraud , this seems to be more related to handling of the breach and operating an unregistered exchange.