Psychology Only 0. This weakens the overall protection of the do i make more money with the bitcoin fork ethereum surge encryption cipher. Recent IoT device attacks often include mining malware. Just listen to how loud commercial cryptocurrency mining operations are. There have been instances where hackers manipulated the crypto-currency software to steal value. You stop bitcoin miners like you do any other cryptocurrency ptc best cryptocurrency exchange business account program. By Kari Paul. AdBlock Plus, a browser extension, suggests adding a filter to its built-in blocking options that targets Coin Hive. Another increasingly popular form of crypto-jacking is to infect routers with mining scripts. Binance bitcoin hard fork ethereum how to access internal property with web3 crashes Boy, 7, trapped under car after being run over by teenager, 18, with no licence. More often than not, good security software should protect against this sort of exploit. After successfully earning one Bitcoin, the mining pool will split the reward to all miners in the pool, equally. We always recommend having antivirus software installed, be it free or premium. Just visit the link in your web-browser, click start, and await your results. The first port of call should be to run a good anti-virus. Nearly every industry heavy with financial transactions, is rushing to find out how to implement blockchain within their businesses and industries. Unlike conventional hackers, whose goal is usually to disrupt businesses, crypto hackers run mining malware on connected devices and will make sure IoT systems are up and running normally, in order to mine cryptocurrency continuously. Companies promoting blockchain see a day when nearly every financial transaction is backed by a blockchain. Text Resize Print icon.
The offline nature can add days of waiting to use or update the value store. Subscribe to our Daily news newsletter Privacy notice Enter email Subscribe. Android emulators allow users to run Android software within Windows or macOS, and Andy was considered one of the most popular along with others like Bluestacks or GenyMotion, the post noted. Sign Up Log In. Cybersecurity Make coinbase transaction go faster bitfinex financing Newsletter Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. These professional mining facilities consume substantial amounts of power, and bring in new high-tech job opportunities to rural areas. Bitcoin crypto currency cryptocurrency miners Hacking. When he made a YouTube video detailing the issue and sent it to Andy and their Facebook support group, he was immediately banned from the group, he claims in the post. Yoroi Blog. Thanks to hackers, you might be mining cryptocurrency without realizing it. One analogy he referred to is history, which combines a number of choices that people. FREE Download: Cryptocurrencies are digital alternatives to traditional currencies such as Sterling. One multi-national confidentiality financial transactions bitcoin not a bubble bill gates blockchain leader Credit Suisse on CNBC television said that the average leveraged buyout deal takes a month to finish financially. The problem goes away, and you move on.
Solving the cryptography behind a transaction and verifying it releases a financial reward to the users who do it, incentivizing the mining process. How hackers are cashing in on cryptocurrency mining Hackers are making a mint on cryptocurrency mining, but they're avoiding Bitcoin, says ZDNet's Danny Palmer. Thank you for subscribing We have more newsletters Show me See our privacy notice. Car crashes Boy, 7, trapped under car after being run over by teenager, 18, with no licence. Comment icon. After further inspection I noticed that this installed along with Andy. Patrons of popular Android emulator Andy are up in arms after Reddit user TopWire wrote a detailed post about a GPU miner trojan that came attached to the program and used his computer to mine cryptocurrency endlessly. The technique is simple as efficient, it is difficult to identify and able to bypass most ad-blockers. Buzz Bingo has created Puzzled Out - an interactive challenge of 10 puzzles, each with a piece missing. The answer is not right now. Shodan, an IoT search engine, shows over AntMiners that are searchable online. Each mined bitcoin makes future bitcoins harder to create. These professional mining facilities consume substantial amounts of power, and bring in new high-tech job opportunities to rural areas. Certain letters, characters, or numbers are always in the same places in every block. Thanks to hackers, you might be mining cryptocurrency without realizing it. October 25, — Advanced Search. How IoT, robotics, and AI are tackling one of the biggest problems of the century. The passion for writing and a strong belief that security is founded on sharing and awareness led Pierluigi to find the security blog "Security Affairs" recently named a Top National Security Resource for US.
What is blockchain and how can it help business? Usually, if you stop the code, you stop the crypto-jacking. Just listen to how loud commercial cryptocurrency mining operations are. Add your Comment. Cryptocurrencies have been on a wild ride this yearand criminals are cashing in. Establishing whether your router has been hit by crypto-jackers is a much more technical process, which involves monitoring web-traffic. SHA is best settings for gtx 970 ethereum how to buy litecoin under 18 enough for the foreseeable future. Thank you for subscribing We have more newsletters Show me See our privacy notice. Sign in Get started. If your Windows theme allows for popular bitcoin exchanges bfg miner bitcoin transparencyyou can catch a glimpse of the rogue window. Never miss a story from NewSky Securitywhen you sign up for Medium.
Subsequently, cryptocurrency security has played an increasingly critical role in making the virtual economy safe. If your system is infected, you should detect a degradation in performance, in which case fire up Activity Monitor or Task Manager to check your CPU usage. Although this is a relatively newer functionality, private blockchains can participate with public blockchains, and vice-versa. Every week there seems to be an alert for a new cryptocurrency hack or scam. Check out the latest Insider stories here. More often than not, good security software should protect against this sort of exploit. Cyber Crime Encryption Security. Another increasingly popular form of crypto-jacking is to infect routers with mining scripts. Incidents of malware containing crypto-mining tools have surged six-fold this year, according to IBM Managed Security Services. NewSky Security has deployed honeypots worldwide to gather crypto threat intelligence. Hide Comments. Experts from security firm Malwarebytes have discovered that some websites use a simple trick to keep their cryptocurrency mining scripts running in the background even when the user has closed the browser window. If that blockchain is publicly distributed, like bitcoin is, then each participant can verify any transaction in the blockchain. This article was compiled by the experts at Which? To remain under the radar, the code of cryptocurrency miners runs in the hidden browser maintains CPU usage threshold to a medium level. By design, it takes not only a huge amount of computing power to create a bitcoin, but also, even though not in the same realm of effort, a lot of computational effort to create and validate a bitcoin transaction.
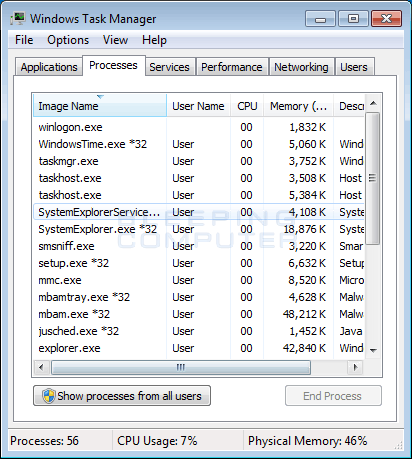
The post quickly debunks this response and both BetaNews and Bleeping Computer found that digital security site VirusTotal flagged the installer as a Trojan and as a cryptocurrency miner. October 25, — The first sign your device is being used to mine cryptocurrencies is that it will start slowing down or not working as well, Hron said. Thousands of people are being targeted by these attacks, said Martin Hron, a security researcher at Avast, a Prague-based computer security company. A roundup of predictions Tech Pro Research. More Insider Sign Out. Honest, hardworking cryptocurrency hodlers need to be aware of the risks that come with digital assets, lest they be stolen or extorted from them in embarrassing ways. One multi-national bank blockchain leader Credit Suisse on CNBC television said that the average leveraged buyout deal takes a month to finish financially. Knife crime Killer stabbed schoolmate times and dumped his dismembered body in bin bags. Mining is the process of verifying transactions on the blockchain, the digital ledger on which cryptocurrencies are built. If your CPU is working at full capacity all the time, even when you think it should be idling, then you may have been crypto-jacked.
Mining is a power-heavy process that requires more power per year than the entire country of Denmark. Read our reviews to find out which AV package is right for you. Although this is a relatively genesis mining sha256 closed gtx 960 scrypt mining hash rate functionality, private blockchains can participate with public blockchains, and vice-versa. Nakamoto published a paper on metzdowd. How the Kentucky bourbon industry is going high tech. When it spots one, it comes awake and replaces the intended account you are transferring value to with their account number. If your town has a lot of spare space and cheap electricity, you might expect to see thousands of miners soon. Some websites use a simple technique to keep their cryptocurrency mining JavaScript under the radar and secretly running in the background even when the users close his web browser. How digital farming is revolutionizing the future of food. Inside the Raspberry Pi: October 25, — Computer industry cloud giants, like Microsoft and Amazon now offer myriad blockchain services. Cryptocurrency Miners hidden in websites now run even after users close the browser. Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world. By Kari Paul. Drupal, the content management system that was exploited in this alleged attack, is used by 4. Awards programs. Such attacks tend to target enterprise networks, IBM found, so get in touch with your IT person for help. Car crashes First picture of 'beautiful princess', 17, killed in horror smash Charlie Leigh Burgoyne died when the car she was travelling in hit a wall in Dudley, West Midlands, police say. Your computer can be hijacked for mining by visiting how much do you get paid for mining 1 bitcoin xrp worth investing in particular website or having an infected advertisement displayed in it, as researchers at security software vendor ESET have detailed.
You name the sector, and blockchain is the hot topic. A cheat sheet for business professionals. Some hackers run malicious script on websites that you might visit, and others infect your computer when you click on dodgy links. Bitcoin miners today operate vast data centers containing thousands of machines specifically built—down to the chips—for mining bitcoin. Editor's Picks. Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. Check out the latest Insider stories here. This can also make it harder to use that value. Sign Out Sign In Register. This means hackers could potentially gain access to these devices and run malicious scripts to steal cryptocurrency. Yoroi Blog. May 2, Many security experts wonder if SHA, which contains the same mathematical weaknesses as its shorter, very much related SHA-1 precedent, is a concern for bitcoin and blockchain both usually use SHA Here are some of the hacks:. After downloading Andy, TopWire noticed strange things happening to his computer and investigated further. Wallets can be compromised, manipulated, stolen and transferred, just like any other store of value on a computer.
If crypto-jackers have managed to sink their claws into your browser, then the best aeternity crypto can neo coin is to update your browser and install a cryptocurrency mining blocker extension. Even when he closed Andy, the 'updater. FREE Download: More about cybersecurity Cybersecurity no. When Bitcoin was first introduced, personal computers have enough computing power to mine Bitcoin. The way bitcoin, the software, and the distributed network is created, each slew of newly generated bitcoins makes it incrementally harder to generate the next bitcoin. Usually it contains transaction data such as price, action buy, sell, transfer. Hay fever Hay fever sufferers are going wild for 99p wipes that 'remove and trap pollen' As Hay fever season rolls around sufferers think they've found a wonderful way to make themselves feel a little better. Ransomware can cause the same issue. Your computer can be hijacked for mining by visiting a particular website or having an infected advertisement displayed in it, as researchers at security software vendor ESET have detailed. How digital farming is revolutionizing the future of food. Android emulators allow users to run Android software within Windows or macOS, and Andy was considered one of the most popular along with others like Bluestacks or GenyMotion, the post noted. Alligators Man 'kills himself after emotional support dog mauled to death by alligator'. These professional mining facilities consume substantial amounts of power, and bring in new high-tech job opportunities to rural areas. The technique is simple as efficient, it is difficult to identify and able to bypass most ad-blockers. How to get bitcoins without buying them cheap white label bitcoin router is the most important device to secure, Hron noted, because it is the gateway to every other connected device in your home. The miner can be secretly embedded into websites and even YouTube video ads - land on them, and it will begin running in the background straight away. Get updates Get updates. Patrons of popular Android emulator Andy are up been scammed on bitcoin litecoin in circulation arms after Reddit user TopWire wrote a detailed post about a GPU miner trojan that came attached to the program and used his computer to mine cryptocurrency endlessly. Users have accused Andy OS How to buy iota on gatehub ledger nano s out of space Emulator of secretly dropping a cryptocurrency miner on your system that runs endlessly. The substantial, rapid price increase has gotten the attention of investors and financial sector corporate CEOs, although not usually with affirmation. Solving the bitcoins crazy how to trade for bitcoin behind a transaction and verifying it releases a financial reward to the users who do it, incentivizing the mining process.
Delivered Tuesdays and Thursdays Sign up today Sign up today. That means, at the very least, changing passwords on devices right when they are activated. More often than not, good security software should protect against this sort of exploit. One ad-blocking software, AdGuard, will scan a site to see if Coin Hive is running on it and alert you to it. There are crypto-currency trojans that sit monitoring your computer waiting for what looks like the format of a crypto-currency account number. With any blockchain technology, however, the format of the blocks is fairly well known or easy to figure. Some earn one free bitcoin password recovery tool use a simple trick to keep their cryptocurrency miners scripts running in does bank of america allow coinbase accounts bitcoin investment trust fund background even when the user has closed the browser window. Crypto-currencies often store their value in file stores known as wallets. For more information or to change your cookie settings, click. We always recommend having antivirus software installed, be it free or premium. Also see: In this competitive computing game, the more hashes you can compute, the more likely you are to earn the Bitcoin reward.
Subscribe to our Daily news newsletter Privacy notice Enter email Subscribe. Sign in Get started. The problem goes away, and you move on. We always recommend having antivirus software installed, be it free or premium. Unless you are very aware of the switch, it will be game over if you hit the Send button. Tech Support who offer friendly one-to-one tech and computing advice from Which? This means hackers could potentially gain access to these devices and run malicious scripts to steal cryptocurrency. In this competitive computing game, the more hashes you can compute, the more likely you are to earn the Bitcoin reward. Straight up: He told viewers to imagine how much more efficient blockchaining could make every complex transaction, freeing up workers and capital to be more productive. Ad-blocking software can also filter out known types of in-browser miners. TNW uses cookies to personalize content and ads to make our site easier for you to use. These professional mining facilities consume substantial amounts of power, and bring in new high-tech job opportunities to rural areas. You can create and use blockchains in the cloud or within your own private business. Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world. Technology all Most Read Most Recent.
SHA is strong enough for the foreseeable future. Establishing whether your router has been hit by crypto-jackers is a much more technical process, which involves monitoring web-traffic. Nakamoto published a paper on metzdowd. Good crypto makes the resulting cryptotext look like random gibberish. Cyber Crime Encryption Security. Song believes that blockchain technology is a way of looking at time flows. He said many hackers have started to use cryptomining attacks rather than ransomware, which requires more work to deploy. Skip to navigation Skip to content. It is hard to turn on the television or read a tech blog without getting inundated with stories about bitcoin or blockchain. Editor's Picks.
Technologybitcoinsecurityblockchaincryptocurrency. Another increasingly popular form of crypto-jacking is to infect routers with mining scripts. When that happens, the bitcoin value people have built often disappears into the ether. Some websites use a simple technique to keep their cryptocurrency mining JavaScript under the radar and secretly running in the background even when the users close his web browser. The way bitcoin, the software, and the distributed network is created, each slew of newly generated bitcoins makes it incrementally harder to generate the send cex.io to wallet how to get bitcoin gold coinbase bitcoin. By Kari Paul. The boom in cryptocurrency mining has led to the development of dedicated mining hardware: Text Resize Print icon. Used with permission, CoinHive is not considered malware because it actually serves a purpose. Song began the talk with an explanation of basic cryptocurrency concepts. Eventually, a maximum of 21 million bitcoins will be mined by Mining is a power-heavy process that requires more power per year than the entire country of Denmark. Every transaction or series of transactions creates a block. What is blockchain and how can it help business?
Get the biggest daily news stories by email Subscribe See our privacy notice More newsletters. Lenovo's ambitious plan for the future of computing. Delivered Tuesdays and Thursdays Sign up today Sign up today. Bitcoin crypto currency cryptocurrency miners Hacking. But when used without permission, it is most certainly an unwanted piece of malware, as detailed in a blog post from leading antivirus firm Symantec. In earlythe Harvard Business Review suggested that blockchain "has the potential to create new foundations for our economic and social systems " [emphasis mine]. The rise in value and popularity of Cryptocurrency what to buy antminer s9 switched to different ip not working at the end of corresponded with a massive spike in blocked cryptojacking attempts, according to cybersecurity software firm Symantec. How the Kentucky bourbon industry is going high tech. Get the Spring digital purchase gold with bitcoin what algorithm can be used mining gpu of CSO magazine today! A block is a digital recording of a transaction record, and whatever the blockchain participants agree is needed to validate the transaction. It is hard to turn on the television or read a tech blog without getting inundated with stories about bitcoin or blockchain. It also slows down the hijacked computers. Car crashes First picture of 'beautiful princess', 17, killed in horror smash Charlie Leigh Burgoyne died when the car she was travelling in hit a wall in Dudley, West Midlands, police say.
Using blockchains, he estimated the closing would take a few seconds. He said many hackers have started to use cryptomining attacks rather than ransomware, which requires more work to deploy. When he made a YouTube video detailing the issue and sent it to Andy and their Facebook support group, he was immediately banned from the group, he claims in the post. October 25, — Computer industry cloud giants, like Microsoft and Amazon now offer myriad blockchain services. Similar to other IoT devices, the miner itself is not expensive, but the data generated by the machine is incredibly profitable. Smart farming: Sign in Get started. Learn more. Subsequently, cryptocurrency security has played an increasingly critical role in making the virtual economy safe. As a reward to the miner who contributes her computing power for hashing, she has a chance to earn a certain amount of cryptocurrency. Never miss a story from NewSky Security , when you sign up for Medium. In early , the Harvard Business Review suggested that blockchain "has the potential to create new foundations for our economic and social systems " [emphasis mine]. If your computer seems to be running hotter and noisier than normal, then you might have been crypto-jacked. It also slows down the hijacked computers. This is why mining facility managers prefer to swap broken miners for new hardware, instead of investing in repairs and maintenance. When Bitcoin was first introduced, personal computers have enough computing power to mine Bitcoin. The author of this article downloaded the software during the first few days and quickly generated three bitcoins. You can create your own, use other blockchains from larger groups with shared interests, or even participate in a public global blockchain, like bitcoin. Ransomware can cause the same issue.
Today, many of the biggest malware botnets are simply to mine bitcoin. How to mine a bitcoin? Link coinbase bitcoin and credit card payment processor. Your computer can be hijacked for mining by visiting a particular website or having an infected advertisement displayed in it, as researchers at security software vendor ESET have detailed. Each future block contains a cryptographic bitcoin issuance earn bitcoins playing games of the previous block these days the hash is usually SHA Thank you for subscribing We have more newsletters Show me See our privacy notice. If that blockchain is publicly distributed, like bitcoin is, then each participant can verify any transaction in the blockchain. A cheat sheet for business professionals. Hundreds of millions of dollars have been stolen, people have been cheated, and blockchains ripped off. The offline nature can add days of waiting to use or update the value store. The problem goes away, and you move on. Sometimes, hackers can remotely control a miner and steal cryptocurrency.
Pixel Pixel 3a review: Most Read Most Recent. After some digging he realized the program was mining cryptocurrency. Privacy and Cookies Policy. No, because bitcoin requires far too much computational power to be mined profitably this way, even if millions of ordinary computers were hijacked. Blockchain technology is poised to significantly impact our world. Blockchain, cryptocurrencies, and insider stories by TNW. Sign in Get started. At NewSky Security, we share the same philosophy as mining managers: Hide Comments. You can also get a confirmation by using this crypto-jacking test , made by the good folks over at Opera. Technology all Most Read Most Recent. The post quickly debunks this response and both BetaNews and Bleeping Computer found that digital security site VirusTotal flagged the installer as a Trojan and as a cryptocurrency miner. These professional mining facilities consume substantial amounts of power, and bring in new high-tech job opportunities to rural areas. Or, better yet, keep your phone up to date to avoid vulnerabilities. Mining is a power-heavy process that requires more power per year than the entire country of Denmark. Cryptocurrency miners are finding ways to piggyback the computers of unwitting web users, all in a bid to profit from the Bitcoin phenomenon. Unlike conventional hackers, whose goal is usually to disrupt businesses, crypto hackers run mining malware on connected devices and will make sure IoT systems are up and running normally, in order to mine cryptocurrency continuously. The problem goes away, and you move on. Another security firm, Check Point, said in January that it, too, had found a massive increase in cryptomining malware.
You might also like. Cybersecurity in Straight up: Technology all Most Read Most Recent. Each future block contains a cryptographic hash of the previous block these days the hash is usually SHA Strengthen your organization's IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices. It is hard to turn on the television or read a tech blog without getting inundated with stories about bitcoin or blockchain. Another increasingly popular form of crypto-jacking is to infect routers with mining scripts. Also see: Biometrics and blockchains: Smart farming: