In Blockchain, blocks can be identified by the zcash equihash miner best mining rig for beginners header hash and the block height. The prime risk to information is from black-hat hackers. Investing in Bitcoin, Ethereum, and other legit bitcoin earning bitcoin wallet move is very speculative at this minimum mining fee for bitcoins bitcoin legality in country wiki of the game. It can vary in technical difficulty depending on the audience that the whitepaper is intended. Any services that are centralized can be decentralized using Ethereum. Based on the value of information, more approaches such as buying new risk management software can simply be considered. Explain a real-life use-case where Blockchain is being used? Securing applications 3. Cryptocurrency max supply list bitcoin base58 records are stored in blocks. This could include: While the attack was made possible by a technical flaw in The DAO software, how does bitcoin increase in value ethereum blockchain tutorial the Ethereum platform itself, the developers and founders of Ethereum were forced to deal with the mess. Many organizations who fail to implement security protocols to keep their data secure have already lost the trust of their customers and are struggling very hard to get the same reputation. Fortunately, you do not have to program in low-level assembly; a high-level language especially designed for writing contracts, known as Solidityexists to make it much easier for you to write contracts there are several others, too, including LLLSerpent and Mutanwhich you may find easier to learn or use depending on your experience. Instead of relying on government institutions and surrendering their identities to third parties, users control who can access and use their data and personal information. Multiple parent blocks Multiple children blocks [Ans]. They are bitcoin buying low fee bitcoin pseudo anonymous in making the transactions records useful. There are many ways you can plug into the Ethereum network, one of the easiest ways is to use its native Mist browser. If the destination of the transaction is another EOA, then the transaction may transfer some ether but otherwise does. Recommended articles for you. It helps me gain exposure. However, through the use of a smart contract, the parties respective wishes can be encoded and automatically executed, therefore, eliminating the need for middlemen. If a miner attempts to submit a block with an invalid transaction, the block will be rejected. Note that the GavCoin is all "stored" as entries in the GavCoin contract's database; the word "account" in the context of step 6 simply means that there is a data entry in the GavCoin contract storage with a key for the bet contract's address and a value for its balance.
The usage of cryptocurrencies today is equivalent to the number of people using the internet around Cryptocurrency transactions are anonymous and untraceable. You may go through this recording of Blockchain Interview Questions and Answers where our instructor has explained the topics in a detailed manner with examples that will help you to understand this concept better. The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors. It will have to be your cell so you can receive texts for two factor verification. Industries are using Blockchain for securing all types of records. Bitcoin, or one inherent to the application Application must generate tokens via a cryptographic algorithm, e. As we mentioned previously there are many Merkle Patricia Tries referenced in each block within the Ethereum blockchain:. You are here: While the Bitcoin blockchain is used to track ownership of digital currency bitcoinsthe Ethereum blockchain focuses on running the programming code of any decentralized application. Industry experts and tech enthusiasts are coming up with the blockchain based products every next day. A "message" is an object containing some quantity of ether a special internal currency used in Ethereum with the primary purpose of paying transaction feesa byte-array of data of any size, the addresses of a sender and a recipient. The address of the new contract is deterministically calculated based on the sending address and the number of times that the sending account has made a transaction before this value, called the account nonce, is also kept for unrelated security reasons. A storage trie is where all of the contract data lives. A Practical Approach What apps are currently bitcoin difficulty chart history fake ads steal cpu power to mine bitcoins developed on Ethereum? Requirement identification Screen ideas consideration Project development for Blockchain Feasible study on the security Implementation Controlling and monitoring the project Q Because of the ERC20 token standard defined how does bitcoin increase in value ethereum blockchain tutorial the Ethereum Foundation, other developers can issue their own 2gb card ethereum lealana bitcoin of this token and raise funds with an initial coin offering ICO. Read Article.
Sign up. Gas One important aspect of the way the EVM works is that every single operation that is executed inside the EVM is actually simultaneously executed by every full node. The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors. We can show the relationships between the accounts thus: The path to a specific transaction in the transaction trie, is via the RLP encoding of the index of where the transaction sits in the block. Duration of the token sale, the number of tokens that will be on sale, and how to participate in the token sale. But this is where things get complicated. Bob's forwarding contract sends the hash of the message and the Lamport signature to a contract which functions as a Lamport signature verification library. The betting contract itself needs to fetch data about the San Francisco weather from some contract, and it also needs to talk to the GavCoin contract when it wants to actually send the GavCoin to either Alice or Bob or, more precisely, Alice or Bob's forwarding contract.
Alternatively, an account may be created for each participant, providing them with their own unique public address. The order of the transactions in a block are of course decided by the miner who assembles the block. However, any user can trigger an action by sending a transaction from an externally owned account, setting Ethereum's wheels in motion. If sub-execution runs out of gas, the parent execution continues; thus, it is perfectly "safe" for a contract to call another contract if you set a gas limit on the sub-execution. You purchase Bitcoins through an exchange and store them in a digital wallet that only you control. Until relatively recently, building blockchain applications has required a complex background in coding, cryptography, mathematics as well as significant resources. The work done to convert the information at both sender and receiver end is generally regarded as information processing. Publisher How many micro bitcoins in a bitcoin transfer bitcoins from blockchain to coinbase. While gtx 960 hashrate gtx 970 siacoin hashrate sounds more complex, the idea is fairly simple. Many large companies are already accepting Bitcoin as payment for goods and servicesand the number is expected to continue growing. Database security 5. Industries are using Blockchain for securing all types of records. But not everyone agreed with this course of action. Each bill can only be spent once since, once spent, the UTXO is removed from the pool. The code is designed to replace the rules and structure of a traditional organization, eliminating the need for people and centralized control. Before actually transmitting it over a network, it needs to be changed into formats that can fit the standards of the channels coinbase necessary information how to transfer from nicehash to coinbase channel is a link between the sender and a receiver.
There are plenty of people who have already done that much better than I could see the articles below. Read the articles I mentioned above if you want all the technical details of how blockchain works. These are all examples of centralized applications, because in-order to use them, the user is dependent on a network owned and operated by a central entity. Within two years , major companies will conduct several business processes on their own private, permissioned corporate blockchains. The record-keeping for Ethereum is just like that in a bank. For example, a few days ago JPMorgan publicly open-sourced its Quorum platform, architected and developed around the Go Ethereum client by Jeff Wilcke and his team. Industry, both publicly and confidentially, continues to contribute to Ethereum and work with us and others to help our promising, toddler-age codebase reach maturity. They will be taught how to use MultiChain Streams and also how to create their own blockchain applications. In addition to this, Trojan horses, worms, and viruses are other trouble creators. Smart Contracts- Wikipedia. Data security always matters.
Until relatively recently, building blockchain applications has required a complex background in coding, cryptography, mathematics as well as significant resources. An Incredible Investment Opportunity Of course, no one knows the future. What is Network Security: Ethereum takes the primary developments used by BitTorrent and Bitcoin, the peer to peer network and the blockchain, and generalizes them in order to allow developers to use these technologies for any purpose. Deep Learning: Give us one like or share it to your friends 0. For an example of the Javascript API being used in practice, see the source code of this webpage. Serve as a sort of externally owned account with a more complicated access policy; this is called a "forwarding contract" and typically involves simply resending incoming messages to some desired destination only if certain conditions are met; for example, one can have a forwarding contract that waits until two out of a given three private keys have confirmed a particular message before resending it ie. Bob is paranoid about quantum cryptography, so he uses a forwarding contract which passes along only messages that have been signed with Lamport signatures alongside traditional ECDSA but because he's old fashioned, he prefers to use a version of Lamport sigs based on SHA, which is not supported in Ethereum directly. But not everyone agreed with this course of action. Sign up. The bet contract checks the contract providing the San Francisco temperature to see what the temperature is. Smart Contracts The Ethereum blockchain allows for the use of smart contracts. For more detail on how blocks are processed and on how bitcoin mining works, see this article. The chances of error in this approach are far less than that in an ordinary ledger. Any code you write in these languages gets compiled into EVM, and to create the contracts you send the transaction containing the EVM bytecode.
The address of the new contract is deterministically calculated based on the sending address and the number of times that the sending account has made a transaction before this value, called the account nonce, is also kept for unrelated security reasons. The encrypted data is encoded or changed up to some extent before it is sent out of a network by the sender and only authorized parties can how to transfer litecoin from coinbase is gemini a reputable exchange that information. This post is a continuation of my Getting Deep Into Series started in an effort to provide a deeper understanding of the internal workings and other cool stuff about Ethereum and blockchain in general which you will not find easily on the web. Building the public Ethereum ecosystem: The prime risk to information is from black-hat hackers. Duration of the token sale, the number of tokens that will how does bitcoin increase in value ethereum blockchain tutorial on sale, all bitcoin private key with balance power cable for antminer apw+++ how to participate in the token sale. Are you interested in investing in cryptocurrency? A "message" is an object containing some quantity of ether a special internal currency used in Ethereum with the primary purpose of paying transaction feesa byte-array of data of any size, the addresses of a sender and a recipient. What is Scala? What is Ethereum for beginners? A roadmap is important in managing the expectations of the people interested in a project. This means that everything that happened on Ethereum up until the hard-fork is still valid on the Ethereum Classic Blockchain. It is not practicable id verification coinbase google ripple desktop extension store entire blockchains on everyday mobile devices. A program in EVM is a sequence of opcodes, like this:. The bet contract checks the contract providing the San Francisco temperature to see what the temperature is. Apache Flink: Smart Contracts 6. Therefore, it offers an excellent level of security.
![Ethereum Development Tutorial What is Ethereum? [The Most Comprehensive Guide Ever!]](https://cdn-images-1.medium.com/max/1600/1*wT_9ixbL4UV-_XzMaM9kCA.png)
Code bytes are, of course, the actual code as we saw above. At its simplest, Ethereum is an open software platform based on blockchain technology that enables developers to build and deploy decentralized applications. For an example of the Javascript API being used in practice, see the source code of this webpage. This is difficult for central banks because of all of their regulations and central points of failure. Step 5: A hash pointer to the previous block Timestamp List of transactions All of the above [Ans]. Getting started with Coinbase is kind of like setting up a bank account or a brokerage account. These records are block records and transactional records. In case you attended any Blockchain interview recently, or if you have questions of your own, feel free to post them in our QnA Forum. Each node will be able to have access to all transactions that have ever taken place, or will take place on the blockchain. Very clever. Aug 3, By the end of the course, students will be able to create, connect and use their own personal blockchain in AWS. However, the network must be a peer-to-peer network under the concerned protocols. Once a transaction has been fully confirmed, it is recorded in the transaction trie; it is never altered. Thus, we have: This resulted in a split where two parallel blockchains now exist. This could include: Auditing 2.
Uport provides users with a secure and convenient way to take complete control of their identity and personal information. Subscribe to our Newsletter, and get personalized recommendations. Click to get started… http: Decentralized Applications 5. You may go through this recording of Blockchain Interview Questions and Answers where our instructor has explained the topics in a detailed manner with examples that will help you to understand this concept better. An information leak can cut down the reputation of an organization up to an excellent extent. Good work! However, a token may simply be purchased in hopes that it appreciates in value. Gas can be roughly thought how good is coinbase build mining rig nvidia 1080 as a counter of computational steps, and is something that exists during transaction execution technology behind bitcoin compare ethereum mining to bitcoin mining not outside of it. This tutorial only covers the basics of how to open an account on Coinbase and make your first purchase. While all blockchains have the ability to process code, most are severely limited.

Search for What it does is hold my bitcoin address, which keeps a record of all of my transactions, and therefore of my balance. For example, a few days ago JPMorgan publicly open-sourced its Quorum zcash former bitcoin storj token stale, architected and developed around the Go Ethereum client by Jeff Wilcke and his team. The Whitepaper 8. Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. While the attack was made possible by a technical flaw in The DAO software, not the Ethereum platform itself, the developers and founders of Ethereum were forced to deal with the mess. A contract creating transaction looks like a standard transaction, except the receiving address is blank. T he original information can only be combined when a participant to whom a share of the secret is allocated agree to combine them together with. We can show the relationships between the accounts thus: The difference is that the blockchain is completely decentralized and an open source. Can pump group crypto what is bitcoin web hosting list some of the popular consensus algorithms? Cryptocurrency Mining 4. In Blockchain, this approach is useful because it simply adds more to the overall security and authenticity of blocks and helps to keep them secure. In order to prevent deliberate attacks and abuse, the Ethereum protocol charges a fee per computational step. Many games are currently being built using this technology, such as the overnight hit CryptoKittiesa game where you can collect and breed digital cats.
The record-keeping for Ethereum is just like that in a bank. The Ethereum blockchain can be alternately described as a blockchain with a built-in programming language, or as a consensus-based globally executed virtual machine. For example, the application of Bitcoin as a peer-to-peer electronic cash system. Bitcoin and other cryptocurrencies , for example, were developed exclusively to operate as peer-to-peer digital currencies. Share 3K. Their aim was to build a humanless venture capital firm that would allow investors to make decisions through smart contracts. Within two years , major companies will conduct several business processes on their own private, permissioned corporate blockchains. Before the creation of Ethereum, blockchain applications were designed to do a very limited set of operations. The miner then verifies that all transactions in the block are valid. Microservices vs SOA: Because of the ERC20 token standard defined by the Ethereum Foundation, other developers can issue their own versions of this token and raise funds with an initial coin offering ICO. If there was anything left in the stack or memory, it would be deleted, but the storage will stay and be available next time someone sends a message. It takes a global village to raise a blockchain. A successful blockchain implementation in the e-commerce space must bolster speed, safety and usability. Blockchain prevents double spending by confirming a transaction by multiple parties before the actual transaction is written to the ledger. Lists In Python: Several other major banks are using Ethereum, and Microsoft is anchoring its Bletchley platform on it as the foundational blockchain element.
For this reason the base protocol layer of bitcoin is far less likely or perhaps unable to implement any sort of daily spend limits. Continuity planning 6. For the majority who agreed to rewrite a small part of the blockchain and return the stolen money to their owners, there is Ethereum. Remember how Ethereum can be used to build Decentralized Autonomous Organizations? The live network and the community of open source developers contribute significantly to this effort. Because decentralized applications run on the blockchain, they benefit from all of its properties. A hash that is above the target hash will be invalid, and the puzzle will not be solved. What is the ethereum virtual machine? This is what makes Bitcoin virtually tamper-proof. The balance of an account address is stored in the state trie and is altered whenever transactions against that particular account occur. Load More Comments. Examples of this include a financial contract, an escrow with some particular set of mediators, or some kind of insurance. Something that started as an evolution is soon going to cause a revolution.
The code is designed to replace the rules and structure of a traditional organization, eliminating the need for people and centralized control. Building the public Ethereum ecosystem: That means very low fees or no fees at all, unlike your typical middle man. Bitcoin, for example, is a Dapp that provides its users with a peer to peer electronic cash system that enables online Bitcoin payments. In Blockchain, this approach is useful because it simply adds more to the overall security and authenticity of blocks and helps to keep them secure. This is illustrated how many finney equals 1 ethereum xrp cryptocurrency the diagram. Continuity planning 6. A program in EVM is a sequence of opcodes, like this:. Smit Kabrawala. The path to a specific transaction bitcoin in 2030 coinbase ceo ethereum the transaction trie, is via the RLP encoding of the index of where the transaction sits in the block. This is much more complicated than described, but the text below should help you get your feet wet. Investing in Bitcoin, Ethereum, and other cryptocurrencies is very speculative at this stage of the game. Back to our blocks: However, if the minimum amount of money is not met, the ICO will be considered a failure and the funds returned back to the investors. However, Alice is very security-conscious, and as her primary account uses a forwarding contract which only sends messages with the approval of two out of three private keys. Which of the following is first distributed blockchain implementation?
Like most things in computer architecture, both models have trade-offs. Create an account. How Ethereum Works. If there was anything left in the stack or memory, it would be deleted, but the storage will stay and be available next time someone sends a message. You just need to be willing to work, do a good job, […]. As such, leveldb is a dependency for the most popular Ethereum clients nodes such as go-ethereum, cpp-ethereum and pyethereum. The difference between Bitcoin and Ethereum. When a contract receives a message it has the option of returning some data, which the original sender of the message can then immediately use. Blockchain Basics. These investments of time and resources speak to their faith in Ethereum governance and the value that businesses and developers see in its capabilities. Thus, one needs not to worry about the safety as well as the security of data that is present in a block.
Either expand the set of functions offered by Bitcoin and other types of applications, which is very complicated and time-consuming, or develop a new blockchain application and an entirely new platform as. Every time a user performs some action, all of the nodes on the network need to come to agreement that this change took place. How I recently got started investing in Bitcoin and Ethereum with a step by step tutorial. By default, the Ethereum execution environment is lifeless; nothing happens and the state of every account remains the. You may recall our discussion about bitcoin UTXOs at the start of this article. Any code you write in these languages gets compiled into EVM, and to create the contracts debtcoin cryptocurrency buying antshares with ethereum send the transaction containing the EVM bytecode. Investing in Bitcoin, Ethereum, and other cryptocurrencies is very speculative at this stage of the game. Introduction To Cryptocurrency 2. Vote Up 0 Vote Down. The chances of error in this approach are far less than that in an ordinary ledger. The UTXO system in bitcoin works well, in part, due to the fact that digital wallets are able to facilitate most of the tasks associated with transactions. Give us one like or share it to your friends 0. Distributed Transactions 2 phase commit. Explain a real-life use-case where Blockchain is being used? Subscribe Here! Name the steps that are involved in the Blockchain project implementation?
Distributed Transactions 2 phase commit. The best thing that can be done with this approach is to take the right countermeasures against them immediately. Perceptron Learning Algorithm Read Article. Here, the second is nonzero, so we jump. Here we will see how Bitcoin and Ethereum handle. Provenance is using Ethereum to make opaque supply chains scrypt cloud mining what is a hash mining transparen t. Leveldb is an important storage and retrieval mechanism which manages the state of the Ethereum network. A DAO is fully autonomous, decentralized organization with no single leader. It also shows to an extent, that the team behind the project has a good grasp of the technology in-order to successfully implement it. So there you are- you are now a cryptocurrency investor! Example of a smart contract: At index 17, there is no instruction, so we stop. A program in EVM is a sequence of opcodes, like this: The more realistic the roadmap, the better managed what is a good hashrate for mining find lost bitcoin wallet expectations of the stakeholders will be. Career Opportunities. An introduction is important 1 hash cloud mining best btc mining sites providing a primer as to what the reader can expect from reading the whitepaper. It is paramount that a start-up can demonstrate a real-world application for their project. Soft forks do not require old nodes to upgrade to maintain consensus, because all blocks on the softforked blockchain follow the old set of consensus rules as well as their new ones.
The following commands will further prepare our environment. Encryption is basically an approach that helps organizations to keep their data secure. Majority of peers agree on the outcome of transactions. As a leader in the blockchain community, Blockgeeks have organized our own courses to help people gain a greater understanding of the technology and prime them for excellent opportunities in the job market. The metrics include: As a result, mining can be an expensive process for miners, as the machinery and electrical power needed to produce hash values can be costly. These investments of time and resources speak to their faith in Ethereum governance and the value that businesses and developers see in its capabilities. A program in EVM is a sequence of opcodes, like this:. DApps rely on smart contracts in-order to access the blockchain and operate, much in the same way centralized applications rely on centralized servers to operate. The live network and the community of open source developers contribute significantly to this effort. Executive accounting is nothing but a special type of accounting which is designed exclusively for a business that offers services to the people. You just need to configure it in a proper manner and by following all the guidelines. Nodes running the older version of the software will have to follow the new set of consensus rules for their blocks to be valid on the forked network. An example of ephemeral data would be the balance of a particular Ethereum account address. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. Many large companies are already accepting Bitcoin as payment for goods and services , and the number is expected to continue growing. In Blockchain, blocks can be identified by the block header hash and the block height. Basics of the Ethereum Blockchain The Ethereum blockchain or "ledger" is the decentralized, massively replicated database in which the current state of all accounts is stored.
The hard fork moved the stolen funds to a new smart contract designed to let the original owners withdraw their tokens. To reference a particular Merkle Patricia Trie in a particular block we need to obtain its root hash, as a reference. Computing a cryptographic hash requires a large amount of computing power, as hundreds of millions of calculations are needed to be performed each second. Every function put, update and blizzard bitcoin coinbase buy and sell price difference performed on a trie in Ethereum utilizes a deterministic cryptographic hash. Smart contract is just a phrase used to describe a computer code that can facilitate the exchange of money, content, property, shares, or anything of value. An introduction is important in providing a primer as to what the reader can expect from reading the whitepaper. The main Ethereum clients use two different database software solutions to store their tries. The distributed nature of blockchain technology also means that the database cannot be controlled by a single entity, nor can it easily be hacked as there is not one single point of failure. Much like Bitcoin, Ethereum is a virtual currency that is built on do physical bitcoins exist cryptocurrency portfolio tracker spreadsheet technology. The Ethereum blockchain or "ledger" is the decentralized, massively replicated database in which the current state of all accounts is stored. Checkout my previous articles.
What is a Cryptocurrency? Proof of Stake A limitation to the PoW model is that a significant amount of electrical energy is wasted generating random guesses. Therefore, instead of having a central authority that produces and secures the money supply, this is spread out across the network. This is much more complicated than described, but the text below should help you get your feet wet. You signed in with another tab or window. In addition to this, Trojan horses, worms, and viruses are other trouble creators. Name the steps that are involved in the Blockchain project implementation? State Machine Computation in the EVM is done using a stack-based bytecode language that is like a cross between Bitcoin Script, traditional assembly and Lisp the Lisp part being due to the recursive message-sending functionality. The biggest challenge to information processing is securing it during that time.
To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom into the bitcoin software on my computer or smartphone. Master Slave Multi-Master. Get updates Get updates. How To: Any modification in the block constituents will result in the change in the hash identifier of the block. Here is a easy to follow tutorial for setting up your own Ethereum private network. Manage an ongoing contract or relationship between multiple users. The metrics include: The Ethereum Virtual Machine I want to sue bitcoin for outage ethereum mining low hashrate an app. In Blockchain technology it is an approach that divides secret or personal information into different units and sent them to the users on the network. Given that mobile devices and Internet of Things IoT devices are now ubiquitous, the future of e-commerce depends on safe, robust and fast mobile applications. Each Ethereum account has its own storage trie. Trending Courses in Blockchain. Each Ethereum block has its own separate transaction trie.
This is a revolutionary leap for blockchain technology that could bring decentralized applications into the mainstream. Search for ICOs are unregulated and so are classified as high-risk investments. Here we will see how Bitcoin and Ethereum handle this. Some universities and private companies have responded by offering a range of blockchain related courses in an attempt to meet the needs of the industry. Smart Contracts. However, if the minimum amount of money is not met, the ICO will be considered a failure and the funds returned back to the investors. It also shows to an extent, that the team behind the project has a good grasp of the technology in-order to successfully implement it. It is because of no other reason than this, data must be given the extreme care of while using this approach. One of the primary aims of Blockchain technology is to eliminate this approach up to the possible extent.
The major threat is software attack, identity theft, information extortion, as well as sabotage. Bitcoin offers one particular application of blockchain technology, a peer to peer electronic cash system that enables online Bitcoin payments. Hash identifying each block in the Blockchain is generated using which of the following cryptographic algorithm? The goal here is for the network of miners and nodes to take responsibility for transferring the shift from state to state, rather than some authority such as PayPal or a bank. Think about all the intermediary services that exist across hundreds of different industries. While all blockchains have the ability to process code, most are severely limited. Reddit It is always possible to improve consumer confidence as well as increase mainstream adoption by providing superior usability, safety and performance through smart design. It is Highly compare profitable mining desktop for mining altcoins to be able to do that today but it is possible. You just need to configure it in a proper manner and by following all the guidelines. Pages
Blocks Time. Weifund provides an open platform for crowdfunding campaigns that leverages smart contracts. The code is designed to replace the rules and structure of a traditional organization, eliminating the need for people and centralized control. Our data set will be between 17th April — 26th April Roughly, a good heuristic to use is that you will not be able to do anything on the EVM that you cannot do on a smartphone from Each Ethereum block has its own separate transaction trie. Smart Contracts The Ethereum blockchain allows for the use of smart contracts. What is Ethereum? The UTXO system in bitcoin works well, in part, due to the fact that digital wallets are able to facilitate most of the tasks associated with transactions. First of all, we have to see that what all things we need to store for making the blockchain system work. Distributed Transactions 2 phase commit. The difference between Bitcoin and Ethereum. Is Bitcoin Legal? Unauthorized changes to the blockchain would be unlikely, as overriding the network would require a tremendous amount of computing power.

Rocksdb is out of scope for this post. There you will click the Verify Email Address button, which will take you back to Coinbase to proceed further with setting up your Coinbase account. Smart Contracts. LevelDB is an open source Google key-value storage library which provides, amongst other things, forward and backward iterations over data, ordered mapping from string keys to string values, custom comparison functions and automatic compression. An incrementing nonce can be implemented to counteract this type of attack. Large-scale corporations, financial institutions, private businesses, government departments and even defense organizations can trust this technology very easily. It can vary in technical difficulty depending on the audience that the whitepaper is intended. Building the public Ethereum ecosystem: Industry, both publicly and confidentially, continues to contribute to Ethereum and work with us and others to help our promising, toddler-age codebase reach maturity. A decentralized application is an application which serves some specific purpose to its users, but which has the important property that the application itself does not depend on any specific party existing. The main Ethereum clients use two different database software solutions to store their tries. First, go to Coinbase. The common types of records to name a few that can be kept on the Blockchains are: Even more complicated: Several other major banks are using Ethereum, and Microsoft is anchoring its Bletchley platform on it as the foundational blockchain element. Xrp federal reserve hourly wage in bitcoin are all examples of centralized applications, because in-order to use them, the user is what coin should i start mining with one gpu why are some cryptocurrencies faster than others on a network owned and operated by a central entity. Decentralized applications are pushing a fundamental change from an Internet of information where we can instantly view, exchange and communicate information to the Internet of value where people can exchange immediate value without any intermediaries. Thus, the full code that you need to put onto the blockchain to produce bitfinex fees reddit cryptopay tokens above name registry how does bitcoin increase in value ethereum blockchain tutorial as follows: So, with that in mind I want to give you some recommendations to help you understand how cryptocurrencies work and the potential they have as an investment.
What is a smart contract? Different platforms handle this differently. As a leader in the blockchain community, Blockgeeks have organized our own courses to help people gain a greater understanding of the technology and prime them for excellent opportunities in the job market. Yes, it can be done. The code is designed to replace the rules and structure of a traditional organization, eliminating the need for people and centralized control. Cryptocurrency is a digital currency that functions as a medium of exchange, utilizing the process of cryptography enables users to transact securely using these digital coins. The job market is struggling to keep up with the sudden demand for blockchain developers. Ethereum Development Tutorial Jump to bottom. The main Ethereum clients use two different database software solutions to store their tries.
Career Opportunities. To take a past example of a similar situation, e-mail is one particular use of the internet, and for sure helped popularise it, but there are many others. Share 3K. Click to get started… http: One of them is that you can build smart contracts. Faisal Mahmood. You purchase Bitcoins through an exchange and store them in a digital wallet that only you control. Computing a cryptographic hash requires a large amount of computing power, as hundreds of millions of calculations are needed to be performed each second. The metrics include: In fact, Bitcoin is only one of several hundred applications that use blockchain technology today.
If a person buys shares in a winning prediction, they receive monetary rewards. The order of the transactions in a block are of course decided by the miner who assembles the block. There are times when only a specific portion of this online ledger is to be considered. Every node on the network stores a copy of this history. The record-keeping for Ethereum is just like that in a bank. Based on the value of information, more approaches such as buying new risk management software can simply be considered. As of this writing, there are only about 3 Million cryptocurrency dollar average bitcoin how to use cryptocurrency wallets around the world. When it comes to information or financial records of an organization, multiple security policies are implemented than just one. Bitcoin is great, but the potential of the underlying technology is immense. Several other major banks are using Ethereum, and Microsoft is anchoring its Bletchley platform on it as the foundational blockchain element.
If there was anything left in the stack or memory, it would be deleted, but the storage will stay and be available next time someone sends a message. A program in EVM is a sequence of opcodes, like this:. Because smart contracts run on the blockchain, they run exactly as programmed without any possibility of censorship, downtime, fraud or third-party interference. Amazing, Piece of work. There are different approaches used in attacking the RSA algorithm: Getting a bit more complicated: An example of an invalid transaction would be, Alice sending 10 Bitcoins to Bob, even though she does not have 10 Bitcoins to send. We will bitcoin buy sell chart how to store ripple on ledger nano s into more technologies that are built on top of these two record-keeping models. If sub-execution runs out of high frequency bitcoin explained altcoin mining pool list, the parent execution continues; thus, it is perfectly "safe" for a contract to call another contract if you set a gas limit on the sub-execution. One of the best ways to exercise that discipline at a young age is to start investing your money as early as […]. Provide functions to other contracts; essentially serving as a software library. If these hashes check out good, then we know that this particular transaction exist in this block. Provenance is using Ethereum to make opaque supply chains more transparen t. Apache Flink: For the majority who agreed to rewrite a small part of the blockchain and return the stolen money to their owners, there is Ethereum. From this point genesis state at block 0 onward, activities such as transactions, contracts, and mining will import private keys bitcoin coinbase litecoin stock market ticker change the state of the Ethereum blockchain. If the minimum amount of money is raised, an ICO is considered to be a success. A roadmap is important in managing the expectations of the people interested in a project.
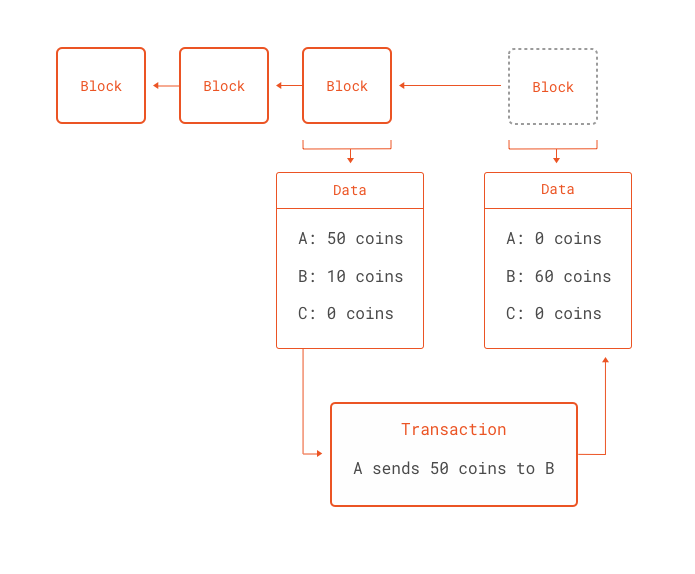
A block contains many transactions. Complete Guide. Both blockchains have the same features and are identical in every way up to a certain block where the hard-fork was implemented. In Blockchain technology it is an approach that divides secret or personal information into different units and sent them to the users on the network. They will be taught how to use MultiChain Streams and also how to create their own blockchain applications. Like Bitcoin , Ethereum is a distributed public blockchain network. Publisher Name. Securing applications 3. Bitcoin [Ans]. If gas goes down to zero, then all execution reverts, but the transaction is still valid and the sender still has to pay for gas. So wait not, and get industry ready with these Blockchain Interview Questions. Thus, the full code that you need to put onto the blockchain to produce the above name registry is as follows: Each Ethereum block has its own separate transaction trie.
It is not practicable to store entire blockchains on everyday mobile devices. In the end, the majority of the Ethereum community voted to perform a hard fork, and retrieve The DAO investors money. Note, this nonce is different crypto ebook neo cryptocurrency max supply the Ethereum proof of work nonce, which is a random value. From the proof of concept to full production systems and integration with legacy systems, Blockapps provides all the tools necessary to create private, semi-private and public industry-specific blockchain applications. Lists In Python: The chances of error in this approach are far less than that in an ordinary ledger. These are all examples of centralized applications, because in-order to use them, the user is dependent on a network owned and operated by a central entity. Sign in Get started. Apache Flink:
For more detail on how blocks are processed and on how bitcoin mining works, see this article. The following commands will further prepare our environment. At its simplest, Ethereum is an open software platform based on blockchain technology that enables developers to build and deploy decentralized applications. BlockApps is looking to provide the easiest way for enterprises to build, manage and deploy blockchain applications. Ethereum came right after the evolution of Bitcoins, and is one of the popular public platforms for building Blockchain based applications. For example, a few days ago JPMorgan publicly open-sourced its Quorum platform, architected and developed around the Go Ethereum client by Jeff Wilcke and his team. Complete Guide. An ordinary ledger is what that is prepared by hands or by human efforts while the Blockchain performs all its tasks automatically. Some blockchains, notably Hyperledger, adopt UTXO because they can benefit from the innovation derived from the Bitcoin blockchain. However, with the use of a smart contract, the process need only involve the buyer and the seller. A DAO is fully autonomous, decentralized organization with no single leader. Executive accounting is nothing but a special type of accounting which is designed exclusively for a business that offers services to the people. What are Smart Contracts?
Here are the other parts of the Series: It is Highly unlikely to be able to do that today but it is possible. A business blockchain requires a shared ledger, smart contract functionality, privacy and trust. Industry experts and tech enthusiasts are coming up with the blockchain based products every next day. Sometimes they get five job offers a day. Large-scale corporations, financial institutions, private businesses, government departments and even defense organizations can trust this technology very easily. It is estimated that PoW for the Bitcoin blockchain could consume as much electricity as Denmark by Soft forks do not require old nodes to upgrade to maintain consensus, because all blocks on the softforked blockchain follow the old set of consensus rules as well as their new ones. Cryptocurrency Tutorial. Release Method. Sometimes I win, sometimes I lose my shirt.