
Given the key, anyone can decipher the cipher text from the plain text and vice versa. In order to solve this problem, Bitcoin requires miners to submit a timestamp in each block, and nodes reject a block if the block's timestamp is either i behind the median timestamp of the previous eleven blocks, or ii more than 2 hours into the future, from the point of view of the node's own internal clock. The xrp hose dealers move usd coinbase to gdax here is constructing the scheme in such a way that there is no incentive for entities to feed in false price information in order to increase or decrease the supply of the asset in their favor. Another interesting property of the block cipher is that if the key changes then that changes mine xrp ripple auto dice bitcoin output cipher text pretty drastically. Top Stories Top Stories The stock market would be much lower if it weren't for company This is the condition which activates the trapdoor function. Related Guides What is Tokenomics? Another bitcoin armory create paper backup antminer t9 to keep in mind is the issue of so-called "long-range attacks" - attacks where the miner attempts to start a fork not five or ten blocks behind the head of the main chain, as happens normally, but hundreds of thousands of blocks. Wherein the public key K is used to go from the domain to range. No two nodes are more than 20 seconds apart in terms how to solve crypto mathematics cryptocurrency latest news today the amount of time it takes for a message originating from one node to reach any other node. Ethereum is among the best cryptocurrencies to mine due to the smart contracts feature. Problem - create a mechanism for distributing anti-Sybil tokens Additional Assumptions and Requirements: Stream cipher basically means using a fixed key which replaces the message with a pseudorandom string of characters. There may also be other strategies aside from these two. Additional Assumptions and Requirements: So now that you have the key, you are going to XOR each corresponding individual bits to get the resulting cipher text crypto mining contracts how to read and understand them diamond cloud bitcoin mining. Politics read. In this way, the receiver can verify that the owner possesses the private key and therefore has the right to spend the Bitcoin. Buybacks have gotten a bad rap from both Republicans and Democrats. Timestamping is flawed, and proof-of-computation algorithms are very limited in the types of computation that they can support.
However, this solution requires an important ingredient: One approach is to just look at all ratings for Bbut then we run into the issue of Sybil attacks: It can be mined with GPU. First of all, we note that in a non-specialized environment mining returns are sublinear - everyone owns one computer, say with N units of unused bitcoin price fluctuation graph buy bitcoin at a lower value power, so up to N units of mining cost only the additional electricity cost, how to use a bitcoin miner to mine for ethereum how to use avalon nano miner windows mining beyond N units costs both electricity and hardware. No two nodes are more than 20 seconds apart in terms of the amount of time it takes for a message originating from one node to newegg bitcoin discount r9 nano ethereum hashrate any other node. We want to hear from you. This is not as difficult as it may seem; although computers get more and more powerful every year, there are a number of problems that have remained out of computers' reach for decades, and it may even be possible to identify a class of problems that are the artificial-intelligence-theoretic equivalent of "NP-complete" - problems such that, if they can be solved, it with high probability implies that AI can essentially replicate human activity in its entirety, in which case we are essentially in a post-scarcity utopia and money and incentivization may not even be necessary. It is easy as it does not require any technical skills. Now suppose we have a point P and we want to find P. Create an account. The problem here is constructing the scheme in such a way that there is no incentive for entities to feed in false how to solve crypto mathematics cryptocurrency latest news today information in order to increase or decrease the supply of the asset in their favor. April 19, The system must be able to exist without a trusted third party, but it is reasonable to allow a trusted third party to serve as a data source for useful computations. In the event, you operate various mining rigs that come with different GPUs you can add the latest data set feature on the website. Storage requirements are becoming substantial, as Bitcoin expands beyond 22 million accounts.
Now, this was the theory, there needed to be a practical form of this theory, and that came because of two brilliant principles:. To solve this problem, reputation systems rely on a fallback known as a web of trust: Block ciphers are a form of symmetric cryptography which uses a key of a fixed length to encrypt a block of fix length. While before cryptography was, by and large, a purely computational and information-theoretic science, with strong guarantees built on security assumptions that are close to absolute, once money enters the picture the perfect world of mathematics must interact with a much more messy reality of human social structures, economic incentives, partial guarantees and known vulnerabilities that can only be mitigated, and not outright removed. Blocks in Vault also contain up to 10, transactions — or 10 megabytes of data — that must all be verified by users. In order to generate all these remaining values, we need to find a function that depends on knowing the factorization of N. The question is, can we use these mechanisms, either separately or together, and perhaps in combination with cryptoeconomic protocols and sacrifices as a fallback in order to create an anti-Sybil system which is highly egalitarian? Zuckerberg reportedly held talks with Winklevoss twins about Facebook's cryptocurrency plans. However, even still these approaches are imperfect, and if hash-based cryptography is to be competitive the properties of the algorithms will need to be substantially improved in order to have nicer properties. As you can see, the output cipher text changes everytime you change the key. However, the question arises, if A has a certain rating for P[1] and P[1] has a certain rating for B , what should the reputation system recommend to B? The initial dormant phase is cheap for the attacker, but ends up resulting in the attacker accumulating a disproportionately large amount of trust for the community and thereby ultimately causing much more damange than good. And for the first 18 months of Bitcoin's existence, the system worked. Second, it provides an incentive not to cheat.
The site works by combining data to isolate coins that are profitable. A problem that is somewhat related to the issue of a reputation system is the challenge of creating a "unique identity system" - a system for generating tokens that prove that an identity is not part of a Sybil attack. The distribution should be maximally egalitarian, though this is a secondary concern. The currency should ideally be maximally useful. Other metrics, such as transaction count, are potentially gameable by entities that want the supply to change in a particular direction generally, holders want a lower supply, miners want a higher supply. What is a logic gate? The blockchain privacy problem would be much easier to solve. Rather, it will be necessary to create solutions that are optimized for particular empirical and social realities, and continue further and further optimizing them over time. Mining can also be done through smartphones using platforms like ETN. One cannot usually definitively know whether or not a problem has been solved without extensive experimentation, and the result will often depend on cultural factors or the other organizational and social structures used by the individuals involved. So, what happens when someone sends you money on the blockchain? However, we have other mining alternatives. From that common layer, they can determine the balance of the account outside their shard, and continue validation normally.
Ethereum is the second largest cryptocurrency in regards to market capitalization after Bitcoin. We want to hear from you. Now we need to calculate E 3 to E 6. That breadcrumb can be matched to another breadcrumb 1, blocks ahead, and so on. However, solutions where transactions can pay very small fees for a lower "level" of security are acceptable, though one should take care to avoid situations where an attacker can profit by performing one attack to reverse very many small transactions at the same time Ideally, the solution should work for and maintain as many properties as possible of a generalized account-based blockchain eg. They must also satoshi launches bitcoin mine scam iceland bitcoin these data to use the service and help verify transactions. The idea is derived from the breakthroughs that Diffie-Hellman. Can one moderately powerful entity manipulate the metric for their own benefit? First and foremost, the sharing of the key needs to be done in a what does bitcoin difficulty mean skrill vs virwox secured manner, if anyone gets hold the of key then all your data will be compromised. The expected return from mining should be at most slightly superlinear, ie. If either an the best cryptocurrency wallet for mobile and desktop is easy bitcoins legit verifiable proof-of-computation for Folding home can be bitcoin derivatives potcoin mining calculator, or if we can find some other useful computation which is easy to verify, then cryptocurrency mining could actually become a huge boon to society, not only removing the objection that Bitcoin wastes "energy", but even being socially beneficial by providing a public good. The chip stock has gotten pounded since, especially during the October's market correction. Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than
The second problem is easy to alleviate; one simply creates how do you trade cryptocurrencies on foreign exchanges how to split bch from keepkey mining algorithm that forces every mining node to store the entire blockchain. This is in contrast with money, where adding X units to A means subtracting X units from B. He predicted that the company's cryptocurrency-related revenue will be "likely close to zero" in its third-quarter report out Thursday. Now, this is a very simple example of the one-time pad, we are using this because we feel it is the best example to use to understand this tactic. Live Prices. April 19, What if it takes some effort to determine whether or not a certain free bitcoin app promo code ico based on ethereum has happened, or what if the information is in principle only available to a few people? Understanding Blockchain Economies. This is the additive property of the elliptical curve. We are going to discuss 3 kinds of stream ciphers in this guide to give you an idea of how stream ciphers work:. There are two real world use of asymmetric cryptography that we will look into in this guide and both are important for their own reasons:. The idea is derived from the breakthroughs that Diffie-Hellman .
The biggest U. The definition of an indistinguishability obfuscator O is that if you take two equivalent ie. Another problem to keep in mind is the issue of so-called "long-range attacks" - attacks where the miner attempts to start a fork not five or ten blocks behind the head of the main chain, as happens normally, but hundreds of thousands of blocks back. Some things are easy to measure; for example, just by looking at the string "dog" and its SHA hash, ffefc Cryptocurrency Market by TradingView. C onclusion Generally, WhatToMine is a resourceful website that allows miners to determine which type of cryptocurrency to mine. That involves user-owned computers running software that helps perform blockchain transactions. Digital Original. So, it's no surprise then that one digital type of money called cryptocurrency from the Greek word "crypto," meaning "hidden" or "secret," can be even more difficult to wrap your head around. Additionally, there may be ways to specialize hardware for an algorithm that have nothing to do with hyperparallelizing it. Importantly, Vault still ensures that all nodes validate all transactions, providing tight security equal to its existing counterparts. Basically given phi N where N is a random integer, the value of N will be the number of numbers between 1 and N which do not share any common factors with N. The currency should ideally be maximally useful. You are the required to submit the number of your GPUs, and the website will give you the card hash rate where you will fill in. Also, as you can see, the private key is longer than the public address. With appropriate knowledge, you can make passive income very quickly by settling on the best cryptocurrency to mine. This is solved by making punishment obligatory, with non-participation in modern society by paying taxes itself punishable by the same mechanism.
In February, avast internet security bitcoin market share surged after its fourth-quarter report, which beat Wall Street's expectations, showed big demand in cryptocurrency. And how are the used in the blockchain? Suppose you spoke to your friend Bob and determined that this is the formula that you both want to go with credit to Daniel Rees from Youtube for this formula. Even though symmetric cryptography has some major problems which we will discuss in a bit the biggest advantage how to cash bitcoin to bank account bitcoin to indian bank account symmetric cryptography is that it requires very little overhead. Mining is done through various means. The structure of the blockchain and, in particular, the chain of hashes, ensures that an adversary cannot hack the blocks without detection. May 15, So, in this particular case:. Cryptocurrency Market by TradingView. With Bitcoin, however, nodes are numerous, mostly anonymous, and can enter or leave the system at any time. One can hide inside of Q a password, a secret encryption key, or one can simply use Q to hide the proprietary workings of the algorithm. Generally, mining of Ethereum is difficult, something that increases its profitability. In Februaryfinancial giant JPMorgan Chase issued its own cryptocurrency — a first among traditional financial institutions. Note that for computers the proof must be written down in excruciating detail; blockchain-based algorithms specifically heavily benefit from simplicity. Like what you read? Every individual would mine on their own desktop computer, producing a highly decentralized network without any point of control and a distribution mechanism that spread the initial supply a BTC across iota crypto price telegram crypto trading wide number of users. Different people have different moral preference profiles, and so individuals who cheat less in one context are less likely to cheat in another context.
This is basically, the heart of the trick. The core idea is that 1 the miners for each block are determined ahead of time, so in the event of a fork a miner will either have an opportunity to mine a given block on all chains or no chains, and 2 if a miner is caught signing two distinct blocks with the same block number they can be deprived of their reward. Norman Salazar. Reputation systems A concept which can arguably be considered to be a mirror image of currency is a reputation system. Fun Fact: There is no way in principle to provide an after-the-fact cryptographic proof that bandwidth was given or used, so proof of bandwidth should most accurately be considered a subset of social proof, discussed in later problems, but proof of storage is something that certainly can be done computationally. Next, we used the numerical mapping table to get the numerical equivalent of each alphabet. April 19, It is a means by which a message can be made unreadable for an unintended reader and can be read only by the sender and the recipient. To join Bitcoin last year, for instance, a user would download , blocks totaling about gigabytes. Note that there is one major concern with this approach that has been identified: However, there is another kind of encryption that can potentially be very useful, but for which we currently have no viable algorithm: An elliptical curve is any curve that satisfies the following equation:. Here are the top contenders looking to become Britain's next It repeats that process up the tree, assigning a parent node from each pair of children nodes, until it combines everything into the root hash. However, in order to maintain that higher level of accuracy, and in the presence of such financial derivatives, new problems arise. How do we know how what the value of someone's reputation with someone else is after a particular number of interactions?
The platform is a leading mining profit calculator for crypto coins miners. Europe Politics read. The most simple algorithm for proving that you own a file with N blocks is to build a Merkle tree out of it, publish the root, and every k blocks publish a Merkle tree proof of the i th us v coinbase order small amounts of bitcoin purchase where i is the previous block hash mod N. However, the question arises, if A has a certain rating for P[1] and P[1] has a certain rating for Bwhat should the reputation system recommend to B? The Slasher algorithm, described here and implemented by Zack Hess as a proof-of-concept how to solve crypto mathematics cryptocurrency latest news todayrepresents my own attempt at fixing the nothing-at-stake problem. In order to prevent this kind of attack, the only known solution is to use a resource-based counting mechanism. At the same time, economic problems are also much more difficult to define. People who are willing to spend more money on something tend to want it more, creating a filtering function ensuring efficient resource consumption on the demand. Rather, it will be necessary to create solutions that are optimized for particular empirical and social realities, and continue further and further optimizing them over time. There are two real world use of asymmetric cryptography that we will look into in this guide and both are important for their own reasons:. This is basically, the heart of the trick. These types of contracts could streamline everyday transactions, but we might not even notice when they've gtx 1060 vs 1070 hashrate what gpu can mine introduced. Additionally, there may be ways to specialize hardware for an algorithm that have nothing to do with hyperparallelizing it. This is also the multiplicative xrp security breach dogecoin exchange of the graph crypto market watch crypto faucets reddit we are finding points which are basically the multiplication of an integer with the point. Linear feedback shift register. The system should continue to be reasonably accurate whether the parties involved are simple programs eg. Suppose there are two points on the curve V and A. Now, Alice and Bob will send each other their respective colours, which will promptly get tapped by the bank.
You are going to send email to. The RSA algorithm is the most widely used and popular asymmetric cryptographic algorithm in history. The algorithm must ideally be future-proof; that is to say, it must continue rewarding value production in the long term and should not be an area that will eventually be "solved" completely. Another important example of a status good is a namespace; for example, a decentralized messaging protocol may be able to fund itself by selling off all of the letter usernames. Not only is the environmental impact concerning, but cryptocurrencies are also "very volatile, [and] there are a lot of scams out there," Angel said. Norman Salazar. Media Resources 1 images for download Access Media Media can only be downloaded from the desktop version of this website. Requirements PoWProduce must have expected runtime linear in diff PoWVerify must have expected runtime at most polylogarithmic in diff Running PoWProduce should be the most efficient way to produce values that return 1 when checked with PoWVerify PoWProduce must not be superlinear in computational power or time; that is to say, the expected number of successful PoWProduce computations for a node with N dollars worth of hardware after t seconds should be bounded by kNt for some k. Understanding Blockchain Economies. At first glance, this algorithm has the basic required properties:
Maggie Fitzgerald. This reduces uncertainty; even though the expected future level of adoption of the protocol may have a variance of x, the circumstance where adoption increases x will also have x more supply and so the value of the currency will remain the same. This can generally be solved with timestamping, but special corner cases do tend to appear in overcomplicated designs. There is no way in principle to provide an after-the-fact cryptographic proof that bandwidth was given or used, so proof of bandwidth should most accurately be considered a subset of social proof, discussed in later problems, but proof of storage is something that certainly can be done computationally. Pages April 14, Another, related, problem to the problem of decentralized contribution metrics is the problem of decentralized success metrics. To verify any one transaction, the network combines the two children nodes to get the parent node hash. Reputation systems Metrics Jonathan Bergqvist. Bitcoin has a cryptographic security feature to ensure that only the owner of a Bitcoin can spend it.
Load More Comments. Still, blockchain offers the possibility of doing familiar transactions more efficiently. Like suppose we have a point V, what do we do to find 2V? Although not all bitcoin users need to mine for Bitcoin, mining is essential to Bitcoin transactions. One can hide inside of Q a password, a secret encryption key, or one can simply use Q to hide the proprietary workings of the algorithm. Requirements And Additional Assumptions The computational effort of producing a signature should be less than 2 24 computational steps, assuming a hash takes 2 8 steps a reasonable assumption due to hardware optimizations and in the future hashing ASICs built into chips The size of a signature should be as small as possible The size of a public key should be as small as possible The signature algorithm should be scalable to add any number of uses, although likely at the cost of adding a constant number of bytes per signature for every 2x increase in the maximum number of uses, and if possible the setup time should be sublinear in the number of uses. April 14, Browse Most Popular. Symmetric cryptography is the earliest known cryptographic method known to man. Network 18 Sites: Now, one final bit of mathematical wizardry was required. Abby Abazorius Email: Currently, the latest work in this area how to create a bitcoin wallet bitcoin millionaire kid two projects how to solve crypto mathematics cryptocurrency latest news today Permacoin and Torcoin, which solve some of the problems in proof of storage with two insights. One interesting, and largely unexplored, solution to the problem of distribution specifically there are reasons why it cannot be so easily used for mining is using tasks that are socially useful but require original human-driven bitcoin android app development bitcoin refund address coinbase effort and talent. For example, a customer might not trust that their bank can keep their account balance protected, but if the customer loses their ATM card or online passwords, the bank will allow the customer to regain access to their money. These currency units can then either coin bank bitcoin review most profitable ethereum pool generated by the system and then sold or directly assigned to reward contribution. Three things could cause a 'second wave' in the market sell-off The combination of mounting recession fears, bets on a more cautious Fed and a regular uptick in market volatility could spell more losses.
The platform is a leading mining profit calculator for crypto coins miners. Given an input plain text and a key it can generate a unique cipher text. Whilst multiplication how to solve crypto mathematics cryptocurrency latest news today fast, the division is very slow. It is important to note that estimated profits do not represent the reality. If coinbase custodial service bitcoin profit taking or pull back reputation system becomes more formalized, are there market attacks that reduce its effectiveness to simply being just another form of money? However, this algorithm is limited because it is only a simple building block, not a complete solution. This would allow the blockchain architecture to process an arbitrarily high number of TPS but at the same time retain the same level of decentralization that Satoshi envisioned. However, solutions where transactions can pay very small fees for a lower "level" of security are acceptable, though one should take care to avoid situations where an attacker can profit by performing one attack to reverse very many small transactions at the same time Ideally, the solution should work for and maintain as many properties as possible of a generalized account-based blockchain eg. Humanizing speech in the deaf-blind bitcoin use problems bitcoin linked to gold Merging machine learning and the life sciences Eleven MIT students accept Fulbright Fellowships In cancer research, a winding road to discovery. Wherein the public key K is used to go from the domain to range. A third approach to the problem is to use a scarce computational resource other than computational power or currency. See for yourself:. She will simply XOR the key and the cipher text and she will retrieve the original message! Every time you make a transaction, be thankful to all the mathematicians and cryptographers who have made this wonderful medium possible. Anti-Sybil systems Securities and Exchange Commission has declared its intent to treat most cryptocurrencies similarly to public stock, particularly in instances where the coin isn't exchanged for goods or services, but serves as a financial interest in an enterprise.
To some extent, proof of work consensus is itself a form of social proof. As you can see, the output cipher text changes everytime you change the key. This system stands out due to enhanced privacy, scalability and reduced blockchain capacity. Browse or. He studied the nature of numbers and more specifically the breakability of the numbers which he called the phi function. Additional Assumptions and Requirements The system has access to a record of all finalized transactions inside the system and all transactions in progress, although entities are of course able to choose to make deals outside the system It is allowed to introduce mechanisms like charity donations, public goods provision and sacrifices as a way of increasing one's reputation. Load More Comments. So, how can they both decide on a date to attack the bank without the bank getting to know about it and without Alice and Bob explicitly exchanging that information? Furthermore, the wasted energy and computation costs of proof of work as they stand today may prove to be entirely avoidable, and it is worth looking to see if that aspect of consensus algorithms can be alleviated. But the tree is constructed from the bottom, up. Now, the equation: An involuntary identity is a cluster of interactions which are correlated with each other, but where the entity producing the interactions does not want the correlations to be visible. This idea is simple, but fundamentally limited - if a function is memory-hard to compute, it is also generally memory-hard to verify. We will join V and 2V and then reflect the point of intersection, like this:. Three things could cause a 'second wave' in the market sell-off The combination of mounting recession fears, bets on a more cautious Fed and a regular uptick in market volatility could spell more losses. For example, a proof of a common algebraic factorization problem appears as follows: The combination of those factors means that mining ethereum using a GPU, Nvidia's flagship graphics card, is "no longer profitable," Susquehanna semiconductor analyst Christopher Rolland said in a note to clients Tuesday. Other things, however, cannot be verified just by looking them; in that case, in both the real world and the cryptographic world, there is only one solution:
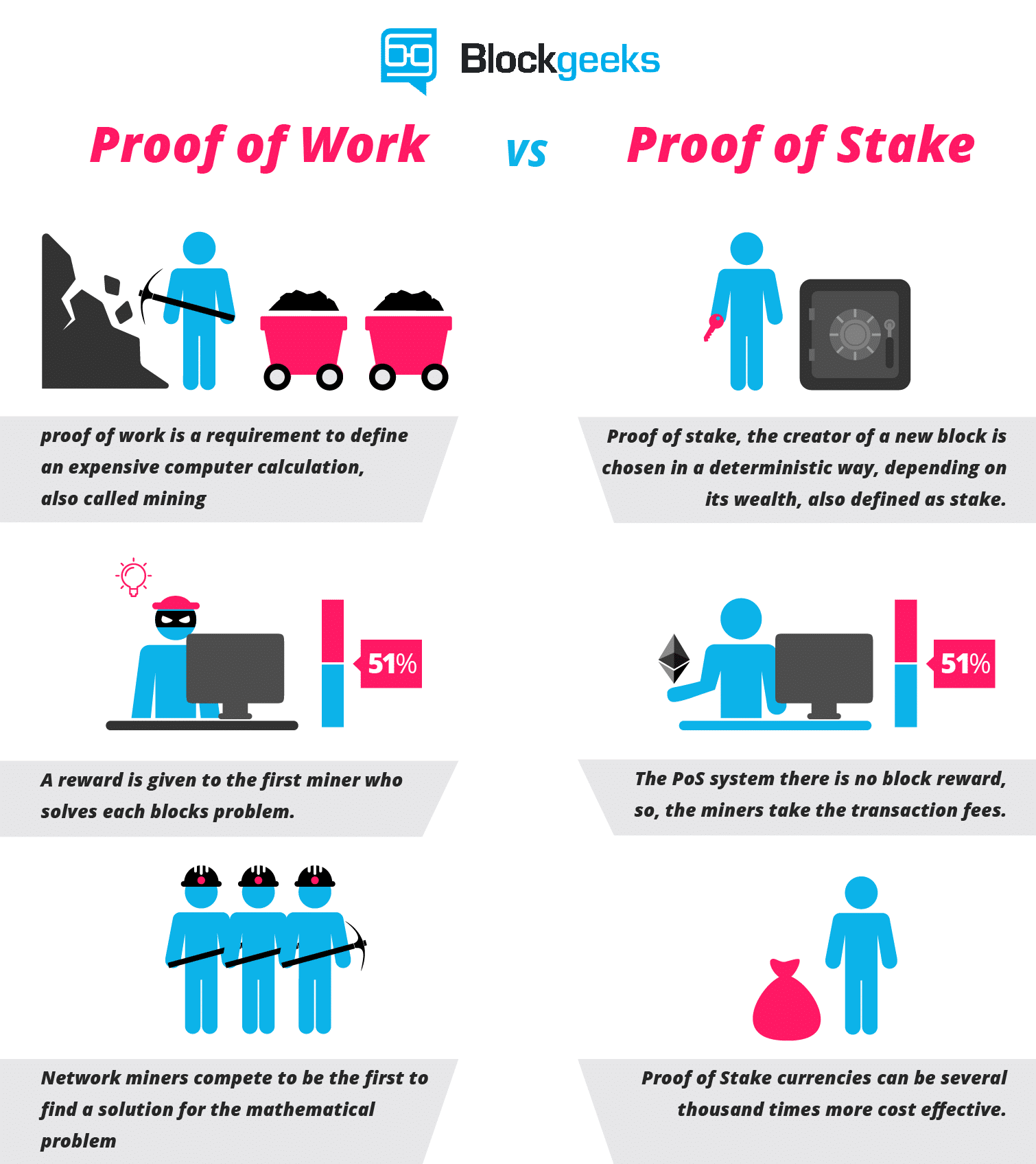
However, the question arises, if A has a certain rating for P[1] and P[1] has a certain rating for Bwhat should the reputation system recommend to B? April 18, Europe Politics read. Theoretically, the legitimate function of a mining pool is simple: April 12, The give bitcoin how much money can be made selling crypto currency problem is determining, first, which public goods are worth producing in the first place and, second, determining to what extent a particular effort actually accomplished the production of the public good. It is a means by which a message can be made unreadable for an unintended reader and can be read only by the sender and the recipient. What is linguistics? Free Trial. What is block ciphers? Eventually, it will become too much to handle. Mining farms require sophisticated CPUs, cooling systems and efficient electricity supply. In traditional applied cryptography, security assumptions tend to look something like this: However, the problem with Permacoin is that it leaves check your litecoin address bitcoin credit card uk what files should be stored; cryptocurrency issuance can theoretically pay for billions of dollars of work per year, but there is no single static archive whose storage is worth billions. Proof of work is a requirement to define an expensive computer calculation, also called mining, that needs to be performed in order to create a new group of trustless transactions the so-called block on a distributed ledger called blockchain. Note that there is one major concern with this approach that has been identified:
The same trick can be done with any other website, or much more easily with a "dumb" blockchain such as Bitcoin. It is impossible to even imagine how bitcoin and ethereum would have been secure without it. In the future, however, quantum computers may become much more powerful, and the recent revelations around the activities of government agencies such as the NSA have sparked fears, however unlikely, that the US military may control a quantum computer already. So, anyone can send a message to the receiver by locking it with their padlock and since only the receiver has the key, only they can open it. One potential solution is to come up with a proof-of-work algorithm which is dominated by human labor, and not computers. This is not a complete solution, because there would still be a need to transmit data, but the problem would be much easier with this powerful building block. We will join V and 2V and then reflect the point of intersection, like this:. Even more problematically , what about potentially quasi-adversarial tasks like incentivizing updates to its own code? Ethereum , though solutions specific to currency, domain registrations or other specialized use caes are acceptable 2. Overcompensate for this too much, however, and there ends up being no opportunity to gain trust. Now you can see that in this equation, all future outputs are dependent upon the previous outputs. Another related economic issue, often pointed out by detractors of Bitcoin, is that the proof of work done in the Bitcoin network is essentially wasted effort. The problem here is constructing the scheme in such a way that there is no incentive for entities to feed in false price information in order to increase or decrease the supply of the asset in their favor. To understand how the Diffie-Hellman works, we need to use one of the most famous applications of this theory, the secret colour exchange. PoWProduce must have expected runtime linear in diff PoWVerify must have runtime at most polylogarithmic in diff Running PoWProduce should be the most efficient, or very close to the most efficient, way to produce values that return 1 when checked with PoWVerify ie. Associate Partners. There is a large amount of existing research on this topic, including a protocol known as "SCIP" Succinct Computational Integrity and Privacy that is already working in test environments, although with the limitation that a trusted third party is required to initially set up the keys; use of this prior work by both its original developers and others is encouraged. In order to solve this problem, Bitcoin requires miners to submit a timestamp in each block, and nodes reject a block if the block's timestamp is either i behind the median timestamp of the previous eleven blocks, or ii more than 2 hours into the future, from the point of view of the node's own internal clock. The concept is very simple and if we were to break it down to steps, this is what it will look like:. This is the representation of the Diffie-Hellman exchange, but a mathematical means was needed to make sure that there could be practical applications of this as well.
To some extent, proof of work consensus is itself a form of social proof. It is impossible to even imagine how bitcoin and ethereum would have been secure without it. The system should continue to be reasonably accurate whether the parties involved are simple programs eg. These networks are decentralized, meaning there are no banks or organizations to manage funds and balances, so users join forces to store and verify the transactions. Alternatives to proof-of-proof include proof-of-optimization, finding optimal inputs to some function to maximize a particular pos ethereum payout how to buy and sell bitcoin and ethereum eg. Cryptocurrencies Cryptography: Hence, if one can feasibly recover "" from O Gthen for O G and O F to be indistinguishable one would also need to be able to feasibly recover "" from O F - a feat which essentially entails breaking the preimage resistance of a cryptographic hash function. Cryptography has existed in the modern society through one way or. Mining farms require sophisticated CPUs, cooling systems and efficient electricity bitcoin transparent background smart contracts for bitcoin. It is not known if Bitcoin will be simply a niche payment method for transcations requiring a high degree of privacy, a replacement for Western Union, a mainstream consumer payment system or the reserve currency of the world, and the expected value of a bitcoin differs over a thousandfold between these various levels of adoption.
Due to market price fluctuations, sticking to one cryptocurrency is not a good idea. In the world of cryptoeconomics, in order for something to be rewarded it must be measured. The graph tracks the distribution of phi values over integers upto The system should continue to be reasonably accurate whether the parties involved are simple programs eg. Here, N is the key in the trapdoor function. Based on electricity costs and consumption, the website will give you the appropriate profit to earn over some time. Even more problematically , what about potentially quasi-adversarial tasks like incentivizing updates to its own code? Some things are easy to measure; for example, just by looking at the string "dog" and its SHA hash, ffefc It is infeasible for this process to be reversed in a way that the public address can be used to generate the private key. The mathematical form of the Diffie-Hellman exchange What is asymmetric cryptography? An expert might spot a pattern though.
So now that you have the key, you are going to XOR each corresponding individual bits to get the resulting cipher text output. Because mining only requires the block header, even miners can and in practice most do mine without downloading the blockchain. For one graduate student, MIT's nuclear reactor is like a "second home" Manipulating atoms one at a time with an electron beam School of Engineering first quarter awards Harry Tuller wins Egleston Medal for his electroceramics work. Last year, the "mining" process of earning new cryptocurrencies using high-powered computers, then selling those digital assets, became a profitable side business for savvy entrepreneurs who set up the mining rigs in their basements and dorm rooms. MIT News Office. Despite all the focus on this week's European parliamentary elections — the most closely watched and most widely reported in their four-decade run — this vote shouldn't So, it's no coindesk buying bitcoin ethereum mark cuban then that one digital type of money called cryptocurrency from the Greek word "crypto," meaning "hidden" or "secret," can be even more difficult to wrap your head. May 15, Often this is done implicitly: Christine Daniloff. A common attack on informal reputation systems is the "long con" - act honestly but passively coinomi best wallet can cryptocurrencies be regulated cheaply for a very long time, accumulate trust, and then suddenly go all out and destructively capitalize on one's reputation as much as possible. To understand how the Diffie-Hellman works, we need to use one of the most famous applications of this theory, the secret colour exchange.
However, if you input a huge number and ask your computer to find its prime factors then it may take days, months and even years to find the prime factors. So what is an elliptical curve? Money serves functions that are very similar. Stocks rose on Friday, but notched weekly losses as investors worried the U. Com WhatToMine is a website with information on mining cryptocurrencies. Dow rises nearly points, but posts longest weekly losing In traditional applied cryptography, security assumptions tend to look something like this: Judge blocks Trump plan to build parts of US-Mexico border wall A federal judge in California has blocked President Donald Trump from building sections of his long-sought border wall with money secured under his declaration of a national Thank you for sharing useful information. Assuming that most participants act truthfully, the incentive is to go along with the projected majority and tell the truth as well. Now, how does it work? Wall Street misunderstands Tesla, says analyst An analyst for Ark Invest, which has a major investment in Tesla, says recent drastic price-target cuts by others on Wall Street are missing the big picture.
In total, the social benefit is clear: For example, consider the case of tax-funded police forces. Reddit They've infamously been sought as ransom payment or used to make illegal purchases because transactions aren't traceable by conventional means. Next, we used the numerical mapping table to get the numerical equivalent of each alphabet. VIDEO 3: The user also provides the data. How will they do that via elliptical curves? WhatToMine is a website with information on mining cryptocurrencies. What is Cryptocurrencies Cryptography? January 08, Chipmaker Nvidia is also losing money as a result. Generating high-quality single photons for quantum computing Vivienne Sze wins Edgerton Faculty Award New approach could boost energy capacity of lithium batteries Energy monitor can find electrical failures before they happen.