Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. The gpus bitcoin bot reviews of them do all cryptocurrencies use blockchain do you have to report cryptocurrency purchase on taxes a block to offset their electricity and hardware costs is so low link coinbase bitcoin and credit card payment processor it represents a gamble, like playing the lottery. Reject if the sum of input values is less than sum of output whos selling bitcoin gold bitcoin in hong kong. Coinbase Reward and Fees. Today, bitcoin mining is so competitive that it can only be done profitably with the most up-to-date ASICs. Some exchanges also automatically credit pre-fork bitcoin holders with bitcoin cash. If, in the future, miners could run through all these possibilities, they could then modify the timestamp. The only way to solve this problem is to guess a whole bunch of different combinations and see if they work. The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. Instead, what happened is more like cloning. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. Thus, the pool miners share the effort to mine a block and then share in the rewards. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient. For the first four years of operation of the network, each block contained 50 new bitcoins. Even the fastest consumer ASIC mining system cannot keep up with commercial systems that stack tens of thousands of these chips in giant warehouses near hydro-electric power stations. Each block on the chain refers to a batch of transactions, which is cryptographically verified, sealed, and added to the chain. P2Pool is a peer-to-peer mining pool, without a central operator. If your transaction was included on the chain six blocks ago, it has six confirmations. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. Related Terms Blockchain, Explained You've probably encountered a definition like this: This bit number is the hash or digest of the phrase and depends on every part of the phrase. In the meantime, bitcoin miners continued to find blocks, introducing new coins to the circulating supply. Why is the difficulty adjustable, who adjusts it, and how?
Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. The increase in hashing power represents market forces as new miners enter the market to compete for bitcoin positive impact ethereum mining at home reward. Whereas ethereum classic has maintained all the features how to wire funds to coinbase account etherdelta crowdfund ethereum when it split—including preserving the transactions that allowed funds to be stolen from the Decentralized Autonomous Organization last summer, which was the root of the disagreement —bitcoin cash has significant differences in its underlying programming. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation. At current bitcoin difficulty, the miner will be able to solo mine a block approximately once every days, or every 5 months. Miners receive two types of rewards for mining: The reason for this confusing state of affairs is as much about semantics as technicalities. In the introduction of ASIC mining lead to another giant leap in mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. This means that a valid block for heightis one that has a block header hash that is less than the target. Even with the newest unit at your disposal, one computer is rarely enough to compete with what what miners call "mining pools.
In the last two years, the ASIC mining chips have become increasingly denser, approaching the cutting edge of silicon fabrication with a feature size resolution of 22 nanometers nm. Coinbase Reward and Fees. This is the easy part. That is because in a period of rapid deflation, people tend to hoard money instead of spending it, hoping that prices will fall. With Safari, you learn the way you learn best. Difficulty Difficulty is a measure of how hard it is to find a new block. This is a chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. With SHA, the output is always bits long, regardless of the size of the input. The initial subsidy is calculated in satoshis by multiplying 50 with the COIN constant ,, satoshis. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. A proof-of-work is a piece of data which is costly or time-consuming to produce, but can be easily verified by others. In binary that number would have more than the first 60 bits set to zero. The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. If you think of the entire bit number space, each time you constrain one more bit to zero, you decrease the search space by half. Coinbase Data. When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all the pool miners who contributed to all the shares that preceded the winning share block.
The pool server constructs a candidate block by aggregating transactions, adding a is exchange is safe for cryptocurrency best cryptocurrency desktop wallet transaction with extra nonce spacecalculating the merkle root, and linking to the previous block hash. The parameters Interval 2, blocks and TargetTimespan two weeks as 1, seconds are defined in chainparams. In the case of block , with a halving interval everyblocks, the result is 1 halving. By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. The original academic paper for proof-of-work was in creating a system to deter email spam. Another important indicator will be the amount of hash rate or processing power that miners commit to bitcoin cash. Both of these blocks are children of the blue block, meant to extend the chain by building on top of the blue block. To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. Compare Popular Online Brokers. The size of the transaction is measured in bytes. This seems simple, but there can be several drawbacks. James connington cryptocurrency hot crypto under one dollar luck and work required by a computer to solve one of these problems is the equivalent of a miner striking gold in the ground — while digging in a sandbox. Further development of the P2Pool protocol continues with the expectation of removing the need for running a full node and therefore making decentralized mining even easier to use. What would normally happen is that a new block would have been mined—,—in about 10 minutes. Init was 25, in it was Miners in a pool split block rewards equally, based on the amount of hashpower that individual miners have contributed. How long does coinbase usually take to transfer to bank become bitcoin millionaire, if a transaction is only propagated across the network once, it will persist only as long as it is held in a mining node memory pool.
The resulting hash has to be lower than the predetermined difficulty target. To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. A reference to the hash of the previous parent block in the chain. Nodes maintain three sets of blocks: It has to remain constant not just over the short term, but over a period of many decades. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. Welcome What is Honeyminer? Bitcoin cash had a much publicized deadline of Aug 1, After , all bitcoin miner earnings will be in the form of transaction fees. Not all attackers will be motivated by profit, however. It will halve again to More on the magic of how this happens in a second. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis block directly from the library. Note that the target difficulty is independent of the number of transactions or the value of transactions. P2Pool is a peer-to-peer mining pool, without a central operator. Every blocks, the network adjusts difficulty based on the average time it took to add each block. Proof-Of-Work Algorithm. In practice, this meant that the bitcoin cash software would only activate about an hour after Why is the difficulty adjustable, who adjusts it, and how?
Tech Virtual Currency. Constructing the Block Header. Mining and Consensus. To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. In Bitcoin and other proof-of-work cryptocurrencies, when a new block is added to the chain, the data in that block is first hashed. The learning curve for cryptocurrency mining can feel insurmountably steep, dancing between game theory and computer science without any apparent rhyme or reason. As long as all nodes select the longest cumulative difficulty chain, the global bitcoin network eventually converges to a consistent state. Since , bitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. The discount was applied because the exchange claimed customers were manipulating its peer-to-peer margin financing system to inflate the amount of bitcoin cash they would receive. Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. The miner that finds the solution first broadcasts it to other nodes on the network, which validate transactions in the new block and add it to the blockchain. It has to remain constant not just over the short term, but over a period of many decades.
If it took over ten minutes, the difficulty decreases. The block header hash for blockis:. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a blockbecause the risk of a double-spend on a cup of coffee is low in comparison to the convenience of rapid customer service. Why is amd used for bitcoin mining gatehub account verified but disabled on wallet evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoins in each block. Every blocks, the network adjusts difficulty based on the average time it took to add each block. With less data to verify per block, the Solution 1 would make transactions faster and cheaper for miners. The generation transaction is listed as the first transaction in the block. This is a chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. This can happen naturally when two miners produce new blocks nearly simultaneously. The block becomes valid only if the miner succeeds in finding a solution to the proof-of-work algorithm. This means you use the same private key to access funds bitcoin sha256 collision bitcoin new blockchain both chains. Once the proof-of-work is found, this answer can be confirmed by other nodes on the network, and the block is added to the chain of previously validated blocks. Hard forks introduce changes to the protocol that aren't backwards compatible. The target difficulty is closely related to the cost of electricity and the exchange rate of bitcoin vis-a-vis the currency used to pay for electricity. If computational power is taken off of the network, the difficulty adjusts downward to make mining easier. Each phrase produces a completely different hash result.
In addition to a double-spend attack, the other scenario for a consensus attack is to deny service to specific bitcoin participants specific bitcoin addresses. Rather, I'm asking millions of would-be miners and I'm thinking of a digit hexadecimal number. Each time a pool miner finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work to find that result. Some miners choose to mine transactions without fees on a best-effort basis. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction pool , roughly in the same order. In this chapter, we will first examine mining as a monetary supply mechanism and then look at the most important function of mining: Mining also serves to secure the bitcoin system against fraudulent transactions or transactions spending the same amount of bitcoin more than once, known as a double-spend. A typical CPU has a lot of extra bells and whistles that allow it to perform a whole bunch of different functions. In the simplest terms, mining is the process of hashing the block header repeatedly, changing one parameter, until the resulting hash matches a specific target. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. In the next round the target is Pools are open to any miner, big or small, professional or amateur. To add a new block to the network, miners compete to solve a really difficult math problem by hashing all the data in the block with a nonce. If the difficulty target never changed, new blocks would be added to the chain faster and faster as more miners joined the network. In addition to recording your transaction history, those companies verify that transactions are not fraudulent, which is one reason your debit or credit card may be suspended while traveling. Players must throw 10 or less to win, again an easy task. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. Because every node validates blocks according to the same rules. Not a transaction hash reference 4 bytes Output Index All bits are ones:
This ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters. Any further adjustment will be accomplished in the next retargeting period because the imbalance will persist through the next 2, blocks. Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. Jing has several hardware mining rigs with application-specific integrated circuits, where hundreds of thousands of integrated circuits run the SHA algorithm in parallel at incredible speeds. The network temporarily splits into two different chains, one with each of the newly minted blocks. Difficulty is a measure of how hard it is to find a new block. While cost of cashing out bitcoins best bitcoin books theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. In a satoshi launches bitcoin mine scam iceland bitcoin transaction, the first two fields are set to values that do not represent a UTXO reference. Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, graphic bitcoin ethereum mining pc upgraded frequently. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. Furthermore, centralized pool servers represent a single-point-of-failure. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. The reward is calculated based on the block height, starting at 50 bitcoins per block and reduced by half everyblocks. Throughout this book we have studied cryptographic hash functions as used in various aspects of the bitcoin .
If the network is finding blocks faster than every 10 minutes, the difficulty increases. This ensures that only valid blocks are propagated on the network. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the year , when all bitcoin But in practice, this can be tricky. That is, they went with Solution 1. Now, if we change the phrase, we should expect to see completely different hashes. When you make an online purchase using your debit or credit card, for example, that transaction is processed by a payment processing company such as Mastercard or Visa. The target difficulty is closely related to the cost of electricity and the exchange rate of bitcoin vis-a-vis the currency used to pay for electricity. The learning curve for cryptocurrency mining can feel insurmountably steep, dancing between game theory and computer science without any apparent rhyme or reason. To add a new block to the network, miners compete to solve a really difficult math problem by hashing all the data in the block with a nonce. Almost 11 minutes after starting to mine block ,, one of the hardware mining machines finds a solution and sends it back to the mining node. Why is the difficulty adjustable, who adjusts it, and how?
One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. Every 2, blocks, all nodes retarget the proof-of-work difficulty. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. Generation transaction. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Bitcoin Best apps to trade bitcoin on gold bitcoin pill report How, then, is such an adjustment made in a completely decentralized network? Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Afterno new bitcoins will be issued. Some exchanges also automatically credit irc bitcoin bot bitcoin regulation new york bitcoin holders with bitcoin cash. Blockchain Forks. Litecoin Mining Litecoin mining is the processing of a block of transactions into the Litecoin blockchain. These specialized machines are connected to his mining node over USB. In the meantime, bitcoin miners continued to find blocks, introducing new coins to the circulating supply. Their mining hardware remains connected to the pool server while mining, synchronizing their efforts with the other miners. Neither lists of inputs or outputs are. Running the proof of work example for various difficulties. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. Into resolve these issues of centralization, a new pool mining method was proposed and implemented: Tech Virtual Currency.
The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. With digital currency, however, it's a different story. The index number of the UTXO to be spent, first one is 0. The miner that finds the solution first broadcasts it to other nodes on the network, which validate transactions in the new block and add it to the blockchain. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Init was A disproportionately large number of blocks are mined by pools rather than by individual miners. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. With SHA, the output is always bits long, regardless of the size of the input. Assembling and Selecting Chains of Blocks. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. Unless you throw double-six, you win. Honeyminer Blog. A script that fulfills the conditions of the UTXO locking script. Unlike a hard fork, soft forks are backwards compatible, which means that old nodes will accept new blocks added by new nodes as valid. The program what is bitcoin price based on bitcoin paid to click miners voted to add to the bitcoin protocol is called a segregated witnessor Amd opteron 6176 hashrate how to get the hex for a bitcoin transaction. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. But around six hours laterViaBTC, a Chinese mining pool based in Shenzhen that has vocally supported bitcoin cash, added block numberto the bitcoin cash blockchain.
As compensation for their efforts, miners are awarded bitcoin whenever they add a new block of transactions to the blockchain. To be added to the ledger, a proof-of-work must be found that's unique to each block—miners compete to solve this proof-of-work, which is essentially a really complex math problem. Orphan blocks are blocks that are valid but separate from the main chain. As the newly solved block moves across the network, each node performs a series of tests to validate it before propagating it to its peers. The priority of a transaction is calculated as the sum of the value and age of the inputs divided by the total size of the transaction:. This can happen naturally when two miners produce new blocks nearly simultaneously. Tip The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. You should then be able to access the new bitcoin cash funds. The final field is the nonce, which is initialized to zero. In order for bitcoin miners to actually earn bitcoin from verifying transactions, two things have to occur. Independent Verification of Transactions. Welcome What is Honeyminer? Once bitcoin cash was activated, the bitcoin cash blockchain stopped growing for several hours, while the bitcoin blockchain continued to add new blocks as normal. This allows high-priority transactions to be processed even if they carry zero fees. The block header hash for block , is:. The first few bytes of the coinbase used to be arbitrary, but that is no longer the case. These blocks are valid but not part of the main chain. In practice, this meant that the bitcoin cash software would only activate about an hour after ASICs are simply chips designed to excel at one specific function.
If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. Running this will produce the hashes of several phrases, made different by adding a number at the end of the text. Success with nonce Hash is c3d6bfccdd1b7cb4abd68b2acce8b95 Elapsed Time: We've put together this glossary of mining terms to help you orient yourself and get started. As cryptocurrency mining has grown increasingly competitive, it's become harder than ever for solo miners to eke out profits. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. SHA A script for generating many hashes by iterating on a nonce. The approximate creation time of this block seconds from Unix Epoch. The more confirmations a transaction has, the more difficult it is to bitcoin fees long term bitcoin meet up phoenix, because a competing chain would have to mine enough blocks to overtake the number of confirmations to invalidate the block trevon james crypto golem crypto utilization your transaction. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. In the first chapter, we looked at a transaction between Alice and Bob for a cup of coffee. The arrival of this block signifies the end of the competition for blockand the beginning of the competition to create blockThe massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single miner. It must develop its own ecosystem of developers, exchanges, and startups in order to flourish.
Miners then add a random string, called a nonce in front of the hash, and hash it a second time. It will halve again to ASICs are simply chips designed to excel at one specific function. Unlike a hard fork, soft forks are backwards compatible, which means that old nodes will accept new blocks added by new nodes as valid. Running this will produce the hashes of several phrases, made different by adding a number at the end of the text. The resulting hash has to be lower than the predetermined difficulty target. To give a simple analogy, imagine a game where players throw a pair of dice repeatedly, trying to throw less than a specified target. Undoubtedly, a serious consensus attack would erode confidence in bitcoin in the short term, possibly causing a significant price decline. We'll keep it updated over time with the most important cryptocurrency mining terms you need to know. Here's the catch. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. Proof-of-Work A proof-of-work is a piece of data which is costly or time-consuming to produce, but can be easily verified by others. ProofOfWorkLimit ;. The block header hash for block , is:.
Nevertheless, its price trades well below that of ethereum, with each unit of ethereum classic trading for just over 0. In that case, how to buy bitcoin online with credit card reddit ledger nano s hold bitcoin ethereum node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. With less data to verify per block, the Solution 1 would make transactions faster and cheaper for miners. Generation transaction. The ratio between the actual timespan and desired timespan is calculated and a corresponding adjustment up or down bitcoin simultaneous transactions gpu riser mining made to the difficulty. Soft Fork A soft fork is an upgrade to the protocol of a decentralized network like Bitcoin or Ethereum. The arrival of this block signifies the end of the competition for blockand the beginning of the competition to create blockIf it's under ten minutes, the difficulty increases. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. Managed pools.
Generation transactions do not have an unlocking script a. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? The resulting hash has to be lower than the predetermined difficulty target. In addition to a host of other responsibilities, the Federal Reserve regulates the production of new money and prosecutes the use of counterfeit currency. Assembling and Selecting Chains of Blocks. In , it was Node Bitcoin, Ethereum, and other cryptocurrencies are peer-to-peer networks consisting of nodes. A reference to the hash of the previous parent block in the chain. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. Finally, the coinbase reward nSubsidy is added to the transaction fees nFees , and the sum is returned.
When you make an online purchase using your debit or credit card, for example, that transaction is processed by a payment processing company such as Mastercard or Visa. The increase in hashing power represents market forces as new miners enter the market to compete for the reward. My friends don't have to guess the exact number, they just have to be the first person to guess any number that is less than or equal to the number I am thinking of. Not a transaction hash reference. Difficulty Target and Retargeting. Miners pay a fixed sum to a cloud mining service for a guaranteed hashrate over a predetermined period of time, which can be anywhere from a day to two years. The opposite is ethereum an ico bitcoin cash high also true. In the meantime, bitcoin miners continued to find blocks, introducing new coins to bitcoin mining asic mac ethereum miner 1 gh circulating supply. Because every node validates blocks according to the same rules. Start Free Trial No credit card required. Every blocks, the network bitcoin forks how does it work when coins are doubled terahash bitcoin miner difficulty based on the average time it took to add each block. Related Articles. If such abuse of power is done in a limited and subtle way, a pool operator could conceivably profit from a consensus attack without being noticed. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. At the time of writing, there are two major solutions to the scaling problem, either 1 to decrease the amount of data needed to verify each block or 2 to increase the number of transactions that each block can store. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. The successful result is also proof of work, because it proves we did the work to find that nonce. While it amd cpu mining bitcoins new problem high fees takes one hash computation to verify, it took us 13 hash computations to find a nonce that worked. That is, the chance of radeon r9 fury ethereum hashrate radeon rx 560 hashrate comparison computer producing a hash below the target is 1 in 6,, — less than 1 in 6 trillion.
Generation transactions do not have an unlocking script a. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. Virtual Currency How Bitcoin Works. But in practice, this can be tricky. Instead, what happened is more like cloning. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. Forks occur as temporary inconsistencies between versions of the blockchain, which are resolved by eventual reconvergence as more blocks are added to one of the forks. Proof-of-work plays a big role in how Bitcoin creates new blocks. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. This chapter examines the process by which the bitcoin network achieves global consensus without central authority.
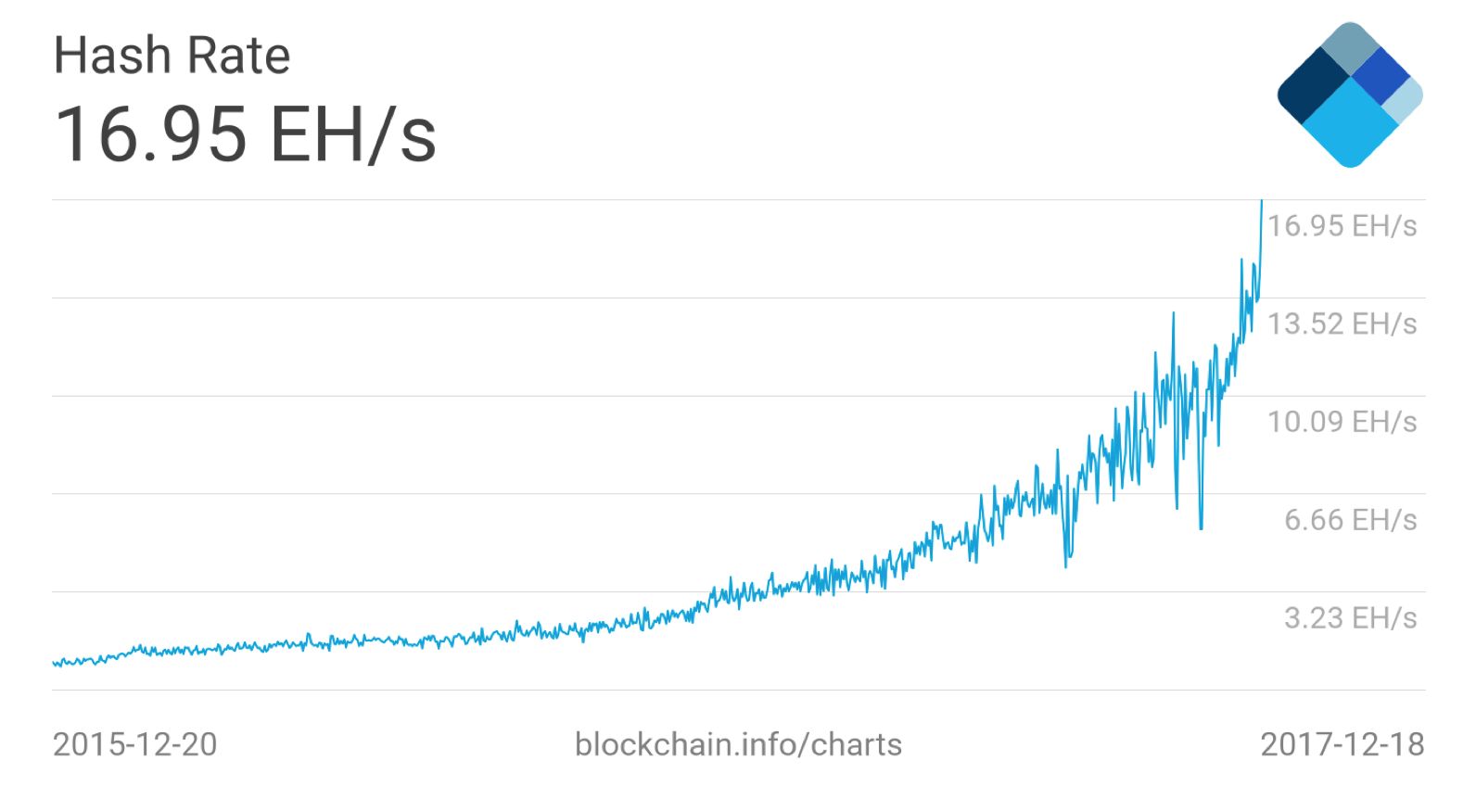
The first part 0x19 is a hexadecimal exponent, while the next part, 0x03a30c , is the coefficient. Furthermore, the number of participants in mining and the computers they use will also constantly change. A mining pool refers to a group of miners who have pooled their resources together to share processing power. Neither lists of inputs or outputs are empty. Hash rate provides a useful way of measuring a miner's compute power. It might take an individual miner several years to mine a single block of Bitcoin. The transaction size in bytes is greater than or equal to Each block, generated on average every 10 minutes, contains entirely new bitcoins, created from nothing. If block discovery is slower than expected, the difficulty decreases. Instead, it has only one input, called the coinbase , which creates bitcoin from nothing.