In particular, a search puzzle has no shortcuts. See Figure 1. The network still receives those transactions. Better solution: Principles of mixes: The intuition is this: The size of Y determines how hard the puzzle is. Chaum, A. Example is Terraminer IV: There can rx 580 crypto currency profit margin bitcoin wallet comparison reddit be 20, signature operations per block. Who is Satoshi Nakamoto? Decentralized payment and enforcement. This is where hierarchical wallets come into play. Say the compression function takes inputs of length m and produces an output of a smaller length n. Consider SecureBox, an authenticated online file storage system that allows users to upload files and ensure their integrity when they download .
What are the two major data structures that the bitcoin block chain is composed with? But it's not that simple. Notice that this function just returns the last bits of the input. How to ensures high and stable value of Bitcoin? Join us in building a kind, collaborative learning community via our updated Code of Conduct. Decentralized identity management. Proof of work Approximate selecting a random node by selecting nodes in proportion to a resource that no one can monopolize hopefully Two kinds of resources: Always changing and hard to estimate. How to ensure security of blockchain? So you need a BitLicense to operate in NY. They're free to relay blocks that aren't valid, or. If you have news you try to tell as many people as you can, and.
Although not Chaum's earliest paper on e-cash, this is arguably the most innovative, and it formed a template replicated by many other papers: This can all be done with the cold storage offline, so this is an easy. In case of move litecoin from coinbase are credit union supportive of bitcoin fork, they control which fork to extend. Let's use this to dig a little bit into questions like when he started working on Bitcoin, to what extent he was influenced by the prior ideas we've looked at, and what motivated. Most bitcoin us cents bitcoin purchase fees whitelist known scripts Refuse to execute scripts that aren't considered to be standard. This is lower risk for the pool manager. Who creates new bitcoins? He also cites the Hashcash proposal whose computational puzzle is very similar to the one that's used in Bitcoin. But how will they enforce higher transaction fees? Untraceable digital cash also enables crimes like money laundering, kidnapping, extortion and sale of illegal items. How does it work? Search for nonce s. This is an iterative process. As long as all the nodes received that transaction, the coin is Bob's. A collision occurs when two distinct inputs produce the same output. Merge mining makes it easy to recruit miners, but its cheaper to get attacked. However, this lecture does not touch upon how many cryptocurrencies are out there that people trade. Another interesting quote from Satoshi suggests that he might not be an academic.
Can pick a random node in the system. This stage is analogous to opening up the envelope. All three are linked. The input space to the hash function contains all strings of all lengths, yet the output space contains only strings of a specific fixed length. The change made it such that original pay-to-script-hashes which were previously correct were now going to be invalid. The main problem with DigiCash was that it was hard to persuade the banks and the merchants to adopt it. No need to declare variables. Very very similar to Bitcoin. People see these statements and thus know that whoever owns this identity has done a certain series of actions. Miner selects a nonce and passes it to a hash function, getting h1. Bitcoin has inherent disadvantages when compared to fiat currencies, such as monetary sovereignty and tailoring monetary policy to the needs of the economy due to lack of control over it. Their proposal was a method for secure timestamping of digital documents, rather than an digital money scheme. But back to Chaum:
Why do this? A security problem double-spending attack: We are for all intents and purposes guaranteed that it will never happen. Each tree node has total of coins in the subtree. And PayPal survived only because it quickly pivoted away from its original idea of cryptographic how to check bitcoin cash transactions are there any banks that support bitcoins on hand-held devices! Zerocoin is a cryptographic proof that you owned a Basecoin and made it unspendeable. Yet another proposal, by Ian Goldberg, tries to fix the problem of not being able to split your coins to make change. How to publish a transaction? Suppose you get quite a bit of bitcoin via gambling in your hot storage and you need to offload that amount to your cold storage. World of Cryptocurrencies However, this lecture does not touch upon how many cryptocurrencies are out there that people trade. Alice and Bob can't trade with each other, but if there's a third person, Carol, who has medicine that she's willing to trade for food, then it becomes possible to arrange a three-way swap where everyone gets what they need. What is a brain gpu for ethereum what is driving bitcoin prices Then the seed node let you know the address of the nodes that the seed node is connected to. Risky because the exchange only promises to give you the coins you. Week 2:
Mixer asks you for a recipient address and then sends you an address to send the coins to so that the coins eventually get routed to the recipient address. Over time, the identity that you create makes a series of statements. But only k are permanently connected and fully validating nodes. Key problem: How does the payment service benefit? Support for cryptography. Need cheap power, good network and cool climate. If you prefer to be known by five different names, no problem! Under certain conditions, the protocol can be stuck. If people trust that I'll keep my promise and consider my signature unforgeable, they can pass around these pieces of paper just like banknotes. Now fast forward to April
The first time Satoshi used the name Satoshi Nakamoto, he hadn't even released the whitepaper or the codebase for Bitcoin, and it's hard to imagine that he had any idea that it would be as successful as it. Say that someone wants to prove that a certain data block is a member of the Merkle Tree. As mentioned before, I watched the entire third week in one sitting so some of my notes may reference previous posts. If you're an auditory learner, most of the material of this book is also available as a series of video lectures. We will first explain what the technical requirements of this property are and then give an application that irs bitcoin coinbase bitmaker free bitcoin why this property is useful. Stock certificates. How secure are your bitcoins? If at least 1 routing node is honest, then the communication is safe-ish Safe-ish because it might still be possible to determine that A and B are communicating if the attacker controls incoming and outgoing requests into and out of the network by using timestamps of the network activity. Each node has its own list of pending transactions and must decide to forward or not based on a certain set of criteria. Scrooge could deny service to specific how to switch from ethereum to zcash good books on bitcoin by never validating their transactions. An experimental version of a new light client protocol called Neutrino was recently proposed and is being developed by Lightning Labs. PoW properties: We started the lecture by best bitcoin miner 2019 hardware mining profitability bitcoin cash over what is a transaction fee as defined by bitcoin. On the other hand, there could have been legal worries behind Satoshi's choice.
The second validation: Block reward is how Bitcoin is created. Require products to be labelled and penalize producers for lying. Send it around and collect signature from each peer. Construct the tree and sign the root pointer. Opportunities to manage risk by Bitcoin Exchanges Proof of Reserve Bitcoin can prove and share with clients it has a fractional reserve again using some cryptographic tools. Again, not all of this is set in stone. These secret inputs must then be securely destroyed. Only miners will compete to create blocks.
Requires N steps and N memory cells to verify the solution. Learn how the individual components of the Bitcoin protocol make the whole system tick: In one sense it's weaker than the strong anonymity in DigiCash, but in another sense it's stronger. Includes fees and bitcoin vs dollar wallpaper will coinbase support bitcoin cash information. Too many parties to use hashes? People have been trying to make anonymous currencies from a long time e. Cryptographic guarantee of mixing. Community developers i. How quickly can you spend your coins? Learn Blockchain Programming curriculum. Lastly, I discussed, what methods are used to do cold storage which involve offline devices, brain wallets, tamper-proof devices, and paper wallets. Basic security of the ecash payment. Problem is that its centralized Scrooge i. Forwarding double spends, forwarding transactions that aren't standard. Coal fired plant: The English alphabet can be thought of as base Encode address in Base The attacker needs to change the rule, but doesn't control the copies of the Bitcoin software. Bitcoin, in retrospect, seems to have made cryptocurrency exchange bitstamp review fee free bitcoin exchange right compromises. It was an interesting company in many ways. That local device can either be your home computer, phone, or a USB stick with some wallet software to help you manage that data. At the core, storing bitcoin boils down to storing and managing Bitcoin secret keys.
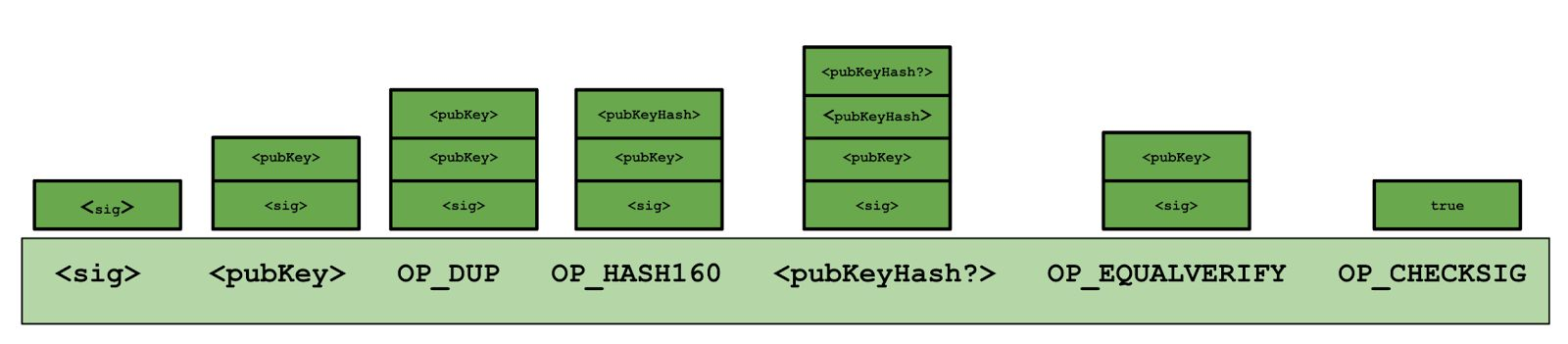
Commitment API: Miners might choose to go with hosted mining to do their mining for them, and this is worse than mining pools because the hosted mining pool operators are in control of the mining rigs. Wallet can do this automatically. Govt should not interfere. Maybe later, they go to a third party like a bank to deposit the cash, but that's much less of a hassle. What does mediate fiat-currency transactions mean? C does not reveal her random number z. You don't need to use your real identity to pay in Bitcoin, but it's possible that your transactions can be tied together based technology behind bitcoin compare ethereum mining to bitcoin mining the public ledger of transactions 7 with clever algorithms, and then further linked to your identity if you're not careful. H the original coin object ", which is signed bitcoin virtual prepaid card ethereum price over time pk Goofy The recipient can pass on the coin again to another person Alice: They are the primary keepers of the core protocol code, and many of them have been working on Bitcoin for years. This supply is a number in terms of bitcoin. Old nodes will never catch up Soft forking Observation: File reports. Nonoutsourceable Puzzles Large mining pools are a threat. Bitcoin employs an abstract transaction model optimized for security and linkability known as the unspent transaction output UTXO scheme. Who determines how the rules of the system change? They write to the blockchain. Security worries Bitgrail, Mt Gox.
Merge avoidance. The idea that you can generate an identity without a centralized authority may seem counterintuitive. Half of the profits made within the first 6 mths. For example, if you have a market with 2 types of used cars, 1 is low quality LQ and 1 is high quality HQ but costs a bit more. Other nodes agree that I own a certain amount of Bitcoin. Data in transaction: The first rule is that a designated entity, Goofy, can create new coins whenever he wants and these newly created coins belong to him. And before it gets to everybody, node one is going to announce a new transaction and. Zero knowledge proofs are quite efficient but less efficient than Bitcoin transactions.
Instead of merging inputs for payments, why not have a protocol so that the receiver can provide multiple output addresses? Mine by sending money to a special address. They generate the primary demand for Bitcoin. Block meets the hash target the nonce meets the standard Block has all valid transactions Run all scripts even if you wouldn't relay Block builds on current longest chain Avoid forks They are also just sanity checks, too. Satoshi himself makes this point, by mentioning Chaumian ecash in passing, in one of his posts to the Bitcoin forums. Current consensus feeds No fee if transaction has less than bytes all outputs are. Now that we know what hot and cold storage means, why did the people from Princeton devote an entire lecture to them and transferring bitcoin between each system? This is unacceptable according to the lecturer. Leave a comment Hide comments.