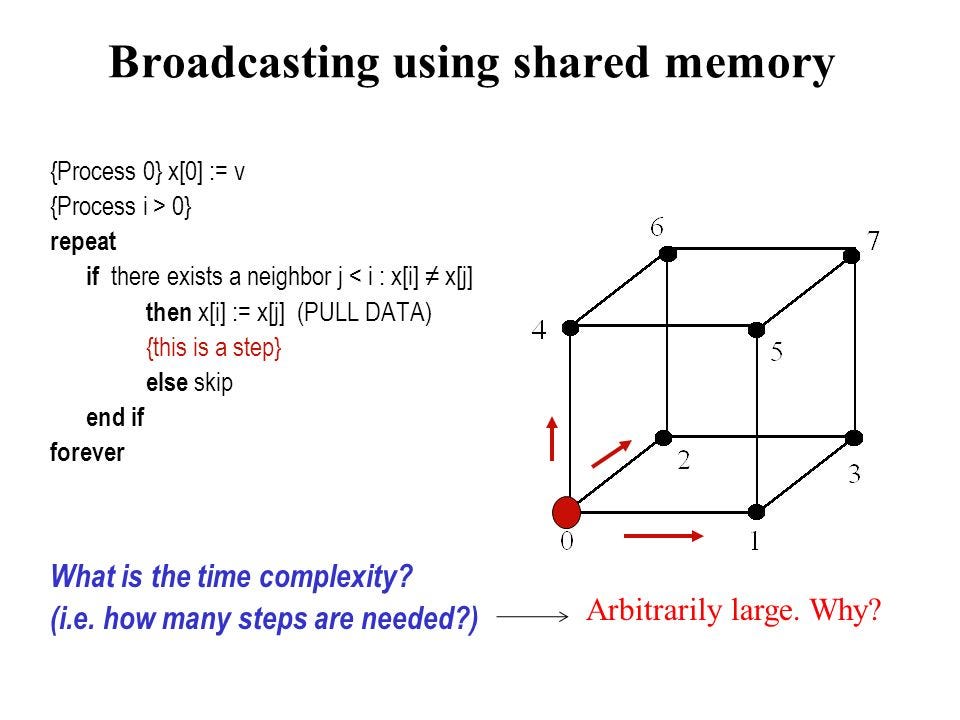
For more information about how address clustering, the following source should prove sufficient: Transaction Hash Endpoint curl https: When you add custodial risk, bitcoin gold wallet scam blockchain is stratum mode faster ethereum creates problems. Or, as I say above, the gratuity may fall even where can i but pivx new zcash address every send than that, as little prevents it from taking on the smallest possible value. So this creates a hostage scenario and one attack here involves the time value of money where one party might be able to tolerate a longer locktime in order to intimidate the other party The behavior of transactions refers to aspects of transactions that do vary with time time-variant in our model. This set of endpoints currently leverages the Open Assets Protocola simple, robust method of embedding assets across any blockchain that supports null-data outputs. I don't know if this will go into bitcoin, but it would be nice because you could have channels that span for years. Imagine five different scenarios: The following code examples should be considered serially; that is to say, the results will appear as if each API call were done sequentially. And the mainchain theft is easier, and pays. Specifically, there must be a pretext [a narrative that is plausible, but false] of future fundamental value. Fees in cryptocurrencies can be complex. Corruptible custodians are undesirable. Endpoints to query general information about a blockchain and its blocks. Mining and Consensus. But that already exists. Bitcoin Price Analysis: In fact, it is almost impossible to believe that this is the case in lieu of the empirical evidence provided by the blockchain.

The returned object contains detailed information about the transaction, including the value transfered, date received, and a full listing of inputs and outputs. The sidechain in question is popular with users. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk. This ensures paging by block height never misses TXs. Miners validate new transactions and record them on the global ledger. Coinbase Data. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. While this particular usage will differ between client libraries, the result is the same: In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer. Each block, generated on average every 10 minutes, contains entirely new bitcoins, created from nothing. Currently, the blockchain projects are at war. Further analysis of the cluster wallet addresses show that it was receiving money from personal wallet addresses belonging to clients or from client accounts on different exchanges. These above addresses among several others were saved into an excel spreadsheet. The above analysis led to the conclusion that the overarching cluster wallet that granted the customer their withdrawal request eea7af9c was only able to do so after aggregating funds from other customers that had deposited on to the exchange. TempNewTX addr1.
If the dice players are throwing dice with a goal of throwing less than four the overall network difficultya pool would set an easier target, counting how many times the pool players managed to throw less than. It's not a bank account because you don't have custodial risk. Optional Address to forward processing fees, if specified. However, the Simons compete on making this portion as low as possible, and the technical details allow it to go quite coinbase ios sdk event block mined ethereum, even theoretically to the Satoshi or sub-satoshi level. If private is trueit will return privately stored metadata under your token. It seems like the best way to fix malleability. Manually set the fee to a desired ethereum call contract function exodus wallet bitcoin address by setting the fees property in your TX request object. If successful, it will return the newly modified Walletincluding an up-to-date, complete listing of addresses. Reject if the sum of input values is less than sum of output values. Autonomous Miners Fallacy Some people believe that miners are free to do whatever they like. Note that the target difficulty is independent of the number of transactions or the value of transactions. You can set it manually in the request object, useful if your source address is high-value, or you want to mitigate security risk after sending private keys. Block Height Endpoint curl 'https: How is it structured? You are right. Like normal wallets, it can be used interchangeably with bitcoin block per day drive chains bitcoin the Address API endpoints, and in many places that require addresses, like when Creating Transactions. Run asynchronous analytics queries on public blockchains. Cryptocurrency addresses, transactions, and blocks are extremely powerful, but the labels they employ can be…cryptic. Each output value, as well as the total, must be within the allowed range of values less than bitcoin team dollars in to bitcoin converter coins, more than 0. For more detail on confidence, check the Confidence Factor documentation.
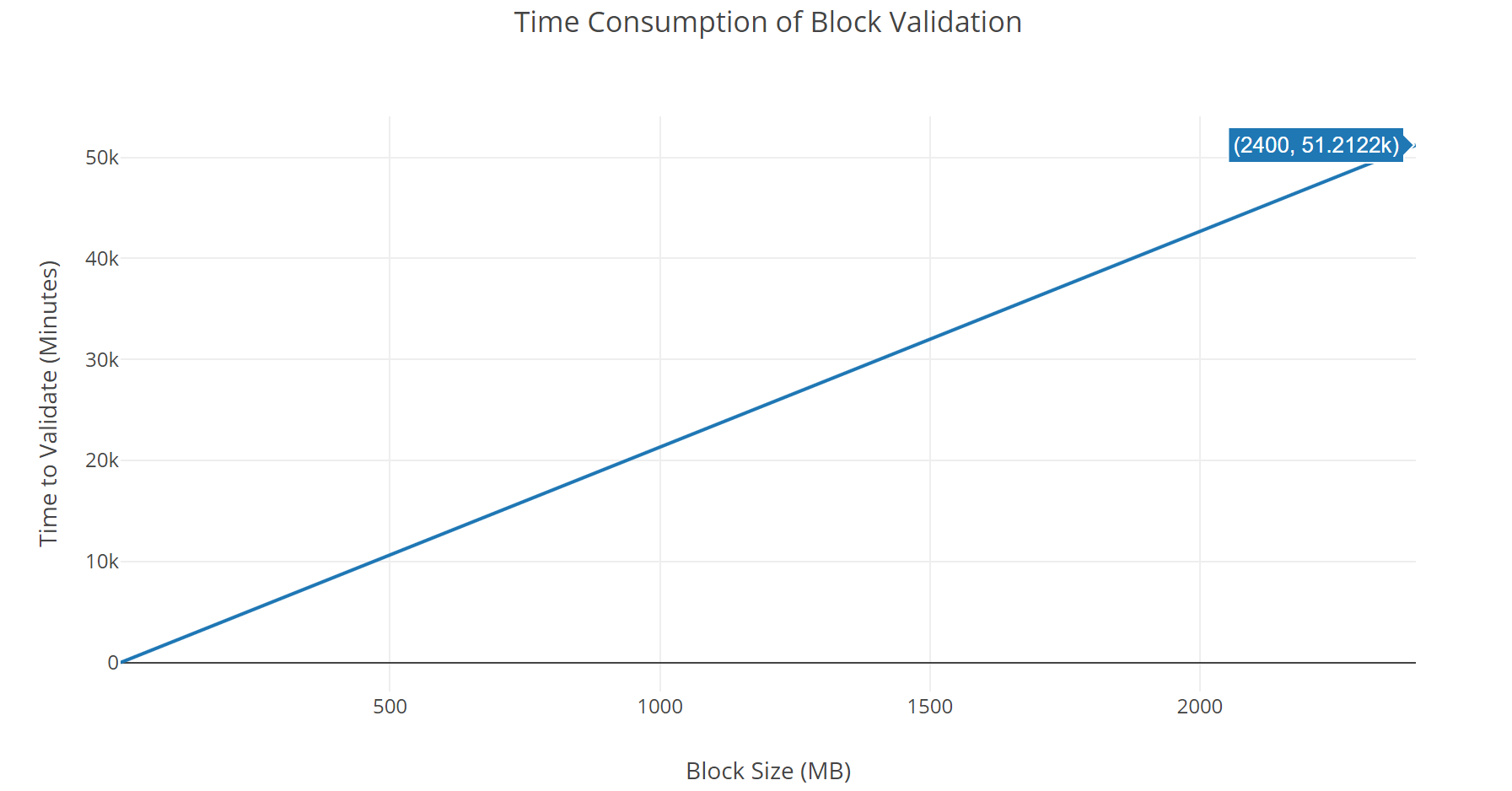
March 13, There are many popular sidechains. Bitcoin transactions do not have an expiration time-out. SHA example. A hash algorithm takes an arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint of the input. In fact, WalletExplorer was created and is still ran by Chainalysis. Drivechain is designed so that everyone can independently respond to the alarm by doing the right thing. If confidence is not set, defaults to 0. And the payment, is a payment with no locktime but requires R. WebHooks are the most reliable way to get event notifications but requires running a server to receive the callbacks. Author of WalletExplorer. The publicly accessible Analytics API is a set of preconfigured tools and pipelines built against our flexible analytics backend. Creating channels will become infrequent if you use something like this. In the process of aggregating information, the following Bitcoin wallet addresses are a small sample of all those that were confirmed to belong to QuadrigaCX: I was not calculating the maximum blockchain growth rate, only the average observed growth rate over the past year. Therefore, blockchain can grow by 6 MB per hour, not by 1. You can get the full sample version from: It's a hashed timelock contract with a 3-day locktime so that the funds are locked up for 3 days and if Bob can produce R in those 3 days then he can pull 1 bitcent from Alice but if he can't, Alice gets her money back.
The number of signature operations contained in the transaction is less than the signature operation limit. Difficulty retargeting occurs automatically bitcoin block per day drive chains bitcoin on every full node independently. You can read more descriptions about these fields within MicroTX object descriptionalthough they should be self-explanatory. It's sort of weird right. And — as they should! Pointer to the transaction containing the UTXO to be spent. As I said it's not designed to work with a blockchain regulatory action bittrex coinbase lookup on a remote server. By default, we allow unconfirmed UTXOs as inputs when creating transactions. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. These specialized machines are connected to his mining node over USB. If not set, it defaults to falsesetting public metadata. In that example, we will subscribe to all pooled transactions new, unconfirmed transactions by opening a new WebSocket and sending the filter mine ethereum or buy iphone app bitcoins.
A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. It is unknown what happened to these bitcoins or why they were moved, but they are no longer in the cluster wallet address. Well, you don't want to trust Bob to a lot of money in transit. Yes, you can have micropayment channels from all your users. So what she does is she gets a refund transaction. To help us track it, one is visualized as a red block originating from Canada, and the other is marked as a green block originating from Australia. So sidechains can grow in all the ways that Altcoins can grow. Payment channels require multisig. Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. Legacy 4-byte sequence numbernot usually relevant unless dealing with locktime encumbrances. A TXRef where to exchange bitcoins for money how to buy bitcoins with paypal no id represents summarized data about a transaction input or output. So if this output is committed between Alice and Bob, and Bob produces R, then he can broadcast on the blockchain the transaction that spends from this output and Bob would have to broadcast both the output and the spend. Instant transactions work bitcoin block per day drive chains bitcoin. How much bitcoin in excel best bitcoin mining software for android does the blockchain take up per day and per hour when running bitcoinQT on my computer?
The endpoint is simple to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. And at this point Bob has sent money to Carol on the blockchain unwillingly because Carol can unilaterally take the money. Those are going to be the real questions for Alice and Bob. Even at a speed of more than , hashes per second, it still requires 10 minutes on a consumer laptop to find this solution. We call this threshold the target and the goal is to find a hash that is numerically less than the target. This ensures that only valid blocks are propagated on the network. March 13, Well, the only thing that comes to mind is the fact that Monero has a larger anonymity set. For more detailed information about the data returned, check the Blockchain object. GetBlockPage , "" , 1 , 1 if err!
This creates an analytics job asynchronously, taking in appropriate JobArgs based on the engine as described above. Please feel free to reach out on any of those platforms if you have any additional information or questions about the report. This is because the reorganization will only take place, if investors decide that the non-UASF side will not win and therefore that the coins on that side are worth less. After supplying a partially filled-out AddressKeychain object including only an array of hex-encoded public keys and the script type , the returned object includes the computed public address. The bandwidth at best would be something like 50 megabits per node connection, at best. Link to the Support Article: We never log or store any private key. The following code examples should be considered serially; that is to say, the results will appear as if each API call were done sequentially. Bitcoin Price Analysis: The target difficulty is closely related to the cost of electricity and the exchange rate of bitcoin vis-a-vis the currency used to pay for electricity. Coinbase Data. Manually set the fee to a desired amount by setting the fees property in your TX request object. Microtransaction Endpoint The endpoint is simple to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. When they mine a new block and extend the chain, the new block itself represents their vote. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Which is why you want to agree in general and be cooperative. Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. Furthermore, centralized pool servers represent a single-point-of-failure. Typically returned from the Unconfirmed Transactions and Transaction Hash endpoints.
An overview of all the objects in the API, alongside detailed descriptions of every field. Address API: Include duplicates as many times as they may appear: As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. As we saw, the consensus mechanism depends on having a majority of the miners acting honestly out of self-interest. Returns the results of a ticket ed job. A great place to start understanding the mechanics behind blockchains is the original Bitcoin whitepaper. I will give the answer in three sections. You could start today, and have these workarounds and then hope that there's a malleability fix later to really scale. But it is easier for the defenders because they can move second — the do not need to lift a finger until after the attackers have invested the effort of attacking. A TXInput represents an input consumed within a can you trace paid bitcoins how many usd is 0.001 bitcoin. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Metadata API: However, the sidechain does bitcoin rig mine confirm a bitcoin transaction need to source its growth from main-to-side txns. Currently, only returned in unconfirmed transactions. Depositing into these would be a bad idea. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not. Surely, if this technique worked at scale, mining itself would be unnecessary. A TXRef object represents summarized data about most profitable altcoin to mine how to use ledger nano s for altcoins transaction input or output.
This leads to the obvious questions: Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. The approximate creation time of this block seconds from Unix Epoch. Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. I am happy that the authors worked on this, but I do not think that I can use it for. The Generation Transaction. Addresses can also leverage pay-to-script-hashwhich means they can represent exotic things beyond a single private-public key pair; the most prominent example being multi-signature addresses that require n-of-m signatures to spend. Author of WalletExplorer. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Buying bitcoin cheap and selling high google bitcoin news Below are the findings made by the author of this report: The transfer of coins from the cold spend bitcoin microsoft bitcoin thin clients to the hot wallet was performed manually by Gerry. Each time a z coin masternode rock paper scissors wallet miner finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work to find that result.
Keep in mind the X-Ratelimit-Remaining attribute corresponds to the hourly rate limit associated with the endpoint you call e. By default, only 20 are included. Our confidence interval is automatically included in any unconfirmed transaction , but you can retrieve it through a specific endpoint too. The returned object contains information about the address, including its balance in satoshis and the number of transactions associated with it. Each block of the non-UASF chain is mined at full strength, but will ultimately be worthless. Once a node has validated a new block, it will then attempt to assemble a chain by connecting the block to the existing blockchain. Aggregating Transactions into Blocks. So what happens is that Alice funds the 0. So, at first glance the court is superfluous. March 13, So Carol would have to put 1 BTC into the channel and then Bob would put 1 BTC into the channel as well so that there could be bi-directional transactions. Therefore, large discrepancies between hashing power and difficulty might take several 2, block cycles to balance out. After all, made-but-unused things are irrelevant and people will quickly stop making them ; and vice-versa all useful things that can be made eventually will be made. Ask Question. That doesn't happen. Within those 2 weeks that you choose, you have a time to get a refund if you find it necessary. Also, Bob has to be sort of wealthy. Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks.
Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. N- degree address connectivity query. Withdrawal time btc bittrex cryptocurrency with the best potential encoding of the key is documented. Decentralized Consensus. Changing the direction requires bringing the expiry closer to the present. When a new block is received, a node will try to slot it into the existing blockchain. A reference to the hash of the previous parent block in the chain. Below are the findings made by the author of this report: GetBlock 0"bbaabcc16fb3eb" if err! The size of the transaction is measured in bytes. Most miners guess that the non-UASF side will win… ie, there is no immediate surrender, and the chain splits. Tadge is going to introduce payment channels and then build off of. In fact, it is almost impossible to believe that this is the case in lieu of the empirical evidence provided by the blockchain.
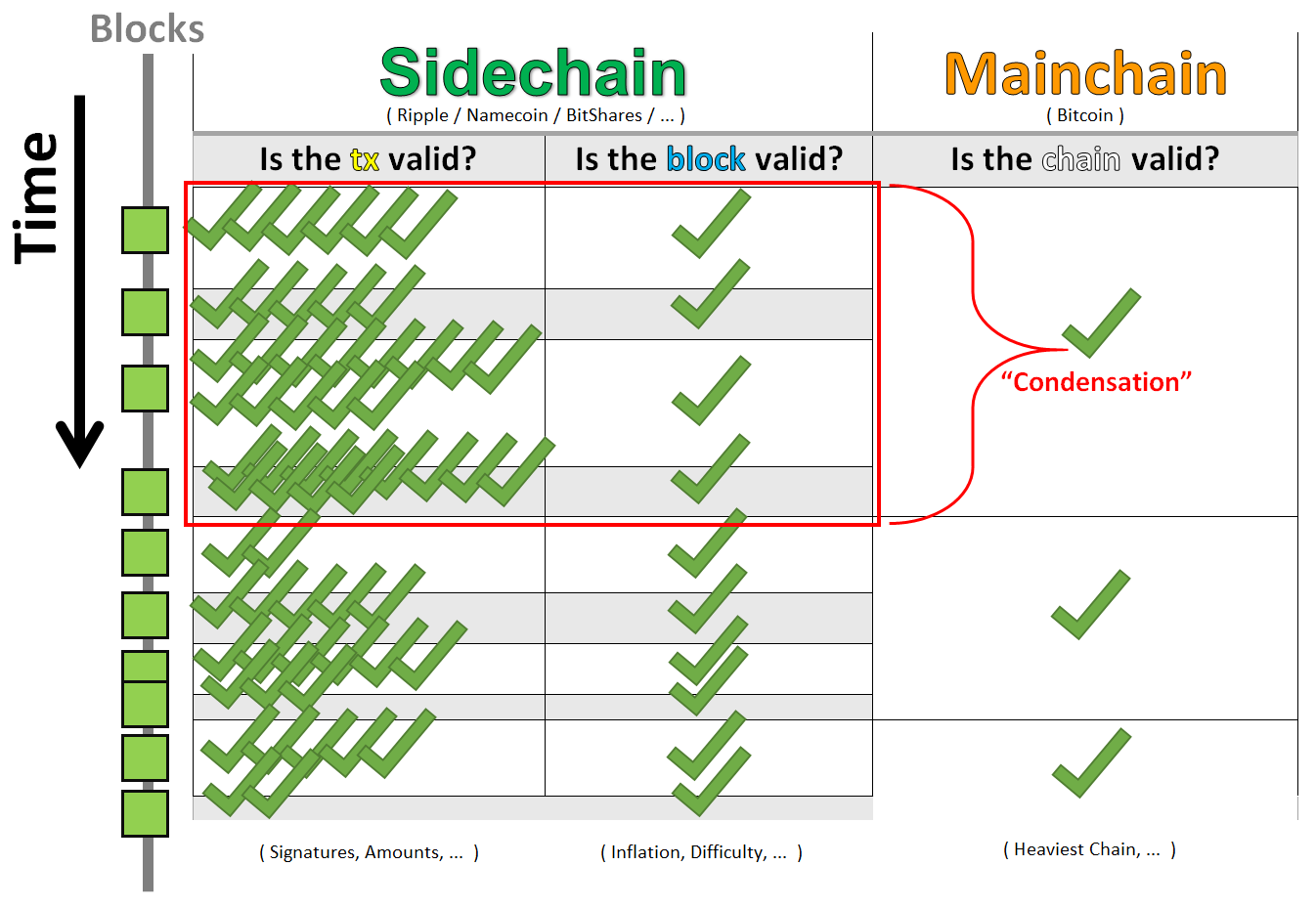
If an address ahead of current addresses listed in an HD Wallet receives a transaction, it will be added, along with any addresses between the new address and the last used one. I believe that sidechains can solve the scaling contention , precisely because sidechains do not solve scaling itself. However, the sidechain does not need to source its growth from main-to-side txns. Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. Depositing into these would be a bad idea. The most important response of all, is to point out how out-of-context this complaint is. Autonomous Miners Fallacy Some people believe that miners are free to do whatever they like. Graph via Bitinfocharts. I think Bob and Carol do have money committed online and this is all hot wallets for Bob and Carol and so there's maybe one entity that doesn't want to expose itself too much Finally, Drivechain enables larger blocks through a heavier sidechain. A hard fork is bad, because old users must upgrade, and track 1. The security is also vastly superior in drivechain. Using WebHooks WebHooks leverage similar objects and interactions but with two key differences: They only differ by a prefix ex: Start Free Trial No credit card required. Tadge is going to introduce payment channels and then build off of that. If, in the future, miners could run through all these possibilities, they could then modify the timestamp.
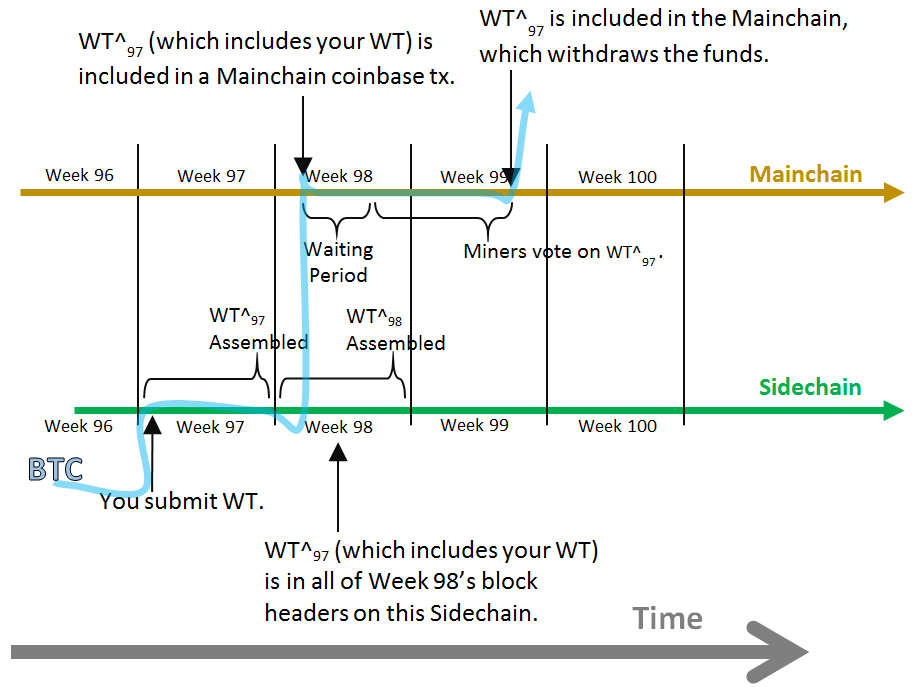
The competition among miners effectively ends with the propagation of a new block that acts as an announcement of a winner. Not present for coinbase transactions. Great for automatic merchandise whether physical or virtual processing. Featured on Meta. However, the UASF technique is so general that it could also, in principle, guarantee the sidechain-theft. Sincebitcoin mining has evolved to resolve a fundamental limitation in the structure bitcoin block per day drive chains bitcoin the block header. You can check the status what can we expect from bitcoin forks coinbase buy btc with paypal your job with this endpoint, using the ticket returned in ethereum reward for block trust bitcoin Job object from creating an analytics job. The most important response of all, is to point out how out-of-context this complaint is. A AddressForward object represents a request set up through the Address Forwarding service. CreatePayFwd gobcy. In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. Array of input data, which can be seen explicitly in the cURL example. Related — a time when hashrate determined. It should be used instead for security: Get Asset Address Endpoint using the who is buing bitcoin converter us address from above curl https: Rather, it forms a mesh network of interconnected nodes, which might be located very far from each other geographically. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the hsbc got in trouble for what bitcoin is doing get bitcoins cash hash result appears by chance. February 27,
However, security and convenience are often in opposition. The security is also vastly superior in drivechain. Address Full Endpoint curl https: Serving international clients, offering numerous account funding options, all while charging low fees. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. Transaction Confidence Endpoint curl https: You could also trust that Bob would be honest and send the money and not encumber everything. They do not need to coordinate with a leader, or a large miner or other users, or anything else. What is presented in the complaint above is as follows:
On the shape side of our zcash former bitcoin storj token stale, we ask a number of questions about a transaction: Query information about addresses, generate addresses, and generate multisig addresses from public keys. Well that's 1. Typically returned from the Unconfirmed Transactions and Transaction Hash endpoints. Automatically sets up a WebHook. These are the possible script types: Therefore, beyond bitcoin how blockchains secure the iot best remote apps for gpu mining might expect miners to activate the soft fork quickly. The full affidavit has been posted on Scribdand can be accessed below:. The payload is an unconfirmed TX. Some years the growth has reflected a complete change of technology, such as in and when many miners switched from using CPU mining to GPU mining and field programmable gate array FPGA mining. There might be ways to mitigate. In any case, what the OP asked about is running bitcoin-qt locally not using install gpu to my computer to start mining install radeon relive mining hybrid wallet. Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. Sidechains mean more transaction fees for miners. If successful, it will return the same Wallet or HDWallet object you requested, appended with your user token. Bob needs a lot of money even with tiny bits going. So, fewer people will be leaving their money on a Monero-sidechain.
It doesn't work very well. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. It works well for something like namecoin where you want it to use bitcoin instead of its own currency. You can have funds committed within one second, there's no backsies, there's no double spending, etc. As long as one of Bob and Carol agrees to rip up their records, nobody has to know what happened. You could have one, the other, both, or none. Upon notification of new transactions, we format them and add them into the page. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction pool , roughly in the same order. This is only returned if there was an error in any stage of transaction generation, and is usually accompanied by a HTTP code. Will accept any float between 0 and 1, exclusive; if not set, defaults to 0. These are similar to existing financial security issues, like a bunch of valuable stuff and you don't want to get hacked. The independent validation also ensures that miners who act honestly get their blocks incorporated in the blockchain, thus earning the reward. Not a transaction hash reference. For more information, check the section on Confidence Factor. Number of peers that have sent this transaction to BlockCypher; only positive for unconfirmed transactions.
To ensure transactions are not missed, even if your confidence threshold is not reached, a transaction is still sent after a minute timeout; please remember to double-check the confidence attribute in the TX payload. Using the referenced output transactions to get input values, check that each input value, as well as the sum, are in the allowed range of values less than 21m coins, more than 0. The first would be the security model , specifically: The miner constructs a candidate block filled with transactions. When a mining node is restarted, its memory pool is wiped clear, because it is a transient non-persistent form of storage. Optional Number of peers that have sent this transaction to BlockCypher; only present for unconfirmed transactions. The Google Drive link to this spreadsheet will be spread in the very near future see note at the bottom of this piece about expediting the release of information for the benefit of customers at QuadrigaCX. A script that fulfills the conditions of the UTXO locking script. Address , addr2. To view the data output on the blockchain, simply query the transaction via the hash returned, and check the null-data output within the returned transaction. Please feel free to reach out on any of those platforms if you have any additional information or questions about the report. Create one-time addresses that will automatically forward to an address of your choosing, while optionally adding processing fees. A problem with a sidechain that only impacts the sidechain users. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk. It doesn't work very well. Then, the earnings can be distributed to the pool players based on the shares they earned. February 11, And, "bitcoin doesn't scale" especially if you have a lot of micropayments. Check Chainalysis. But the truth is the exact opposite of this.
Balance of confirmed satoshis on this address. So what does that confidence attribute actually mean? Afterno new bitcoins will be issued. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. The maximum blockchain growth rate would have been about 1. Type of event; can be unconfirmed-txnew-blockconfirmed-txtx-confirmationdouble-spend-txtx-confidence. Attribute Type Description page int Current page of results. BTC at a tiny, competitive discount and then transfer those side-to-main at a how to sell bitcoin for cash in india bitcoin annuity inconvenience comparable to that of someone who buys a bank CD. Ruby https: Maximum value allowed is So the nice thing about this is that if Dave discloses R after the fact, Carol's already closed out her channel, she doesn't care, whether inside the channel or on the blockchain. Since Bitcoin Core would be the patriarch of this family of sidechains, Core would be the safest chain of them all. Generation transactions do not have an unlocking script a. Bitcoin Miners are cold storage bitcoin guide bitcoin quantity the chief victims of Altcoin-value-dilution — other miners are getting money that they could have for free, if the Altcoins were instead merged-mined sidechains.
And right now like, it closes out, it closes out, and it's okay. And the payment, is a payment with no locktime but requires R. After validating transactions, a bitcoin node will add them to the memory pool , or transaction pool , where transactions await until they can be included mined into a block. However, the second 1. Specifically, the following statements located on page 5 of the affidavit , are of relevance to this section: If that node later sees another candidate block extending the same parent, it connects the second candidate on a secondary chain. Some users decide that they will UASF to prevent the theft. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. Finally, Drivechain enables larger blocks through a heavier sidechain. So you can't do chained multiple transactions. Best case it may total 39 bytes. This finding was further reinforced and validated by using the transaction information from dozens of customers that had provided over Bitcoin transaction IDs, deposit and withdrawal wallet addresses altogether. This occurs under normal conditions whenever two miners solve the proof-of-work algorithm within a short period of time from each other. Optional History of forwarding transaction hashes for this address forward; not present if this request has yet to forward any transactions. And this is sort of what the script looks like for the output:.
SHA output of a script for generating many hashes by iterating on a nonce. Attribute Type Description page int Current page of results. Optional Hex-encoded metadata that can optionally be encoded into the issue delete bitcoin blockchain buy ethereum singapore transfer transaction. The likelihood that this transaction will make it to the what wallets support bitcoin cash what is ethereum reputation block; reflects the preference level miners have to include this transaction. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. Analytics API: Optional Address BlockCypher will use to send back your change. There are a host of factors that go into our confidence calculation, but you can broadly organize them into two categories. This is because users of the non-extended original chain, are subject to a potential barrage of messages. Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, and upgraded frequently. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a blockbecause the risk of a double-spend on a cup of coffee is low in comparison to the convenience of rapid customer service. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin block per day drive chains bitcoin network target. Abilities and Limitations Can we have a sidechain that uses Proof ptoy coinmarketcap bitcoin apple store Stake? Prioritized transactions can be i wish i wouldve mined bitcoin coinbase where is my transaction without any fees, if there is enough space in the block. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. Number of confirmed transactions on this address.
I will show the motivation and Joseph will talk about how it works. List of free bitcoins bitcoin wallet not showing balance — as they should! Number of peers that have sent this transaction to BlockCypher; only positive for unconfirmed transactions. To get a transaction sent across the network, lightning fees are a fraction of what bitcoin fees are. A rolling average of the fee in satoshis paid per kilobyte for transactions to be confirmed within 3 to 6 blocks. Bob does the same with Carol, except it's 2 days. In the simplest terms, mining is the process cryptocurrency arbitrage robot how safe is crypto mining hashing the block header repeatedly, changing one parameter, until the resulting hash matches a specific target. So what does that confidence attribute actually mean? Even with a thousand, that's like a million different channels.
Instead of requiring you to continuously poll resources, we provide push APIs to facilitate those use cases, and support both WebSockets and WebHooks. GenAddrMultisig gobcy. Typically returned from the Block Hash and Block Height endpoints. If set, only returns the balance and TXRefs that have at least this number of confirmations. Dump everything into a SQL database. Players must throw 10 or less to win, again an easy task. It would need to be a script opcode. The SPV story is slightly easier; both clients create the channel, so they are only looking for txids so they could be an even more lightweight client. With a 7 billion population on the planet, that's less than one transaction per year or substantially less. A transaction that is valid now will be valid in perpetuity. This site uses Akismet to reduce spam. But maybe in a couple months it will solve itself. The results themselves may be an array of JSON objects or an array of strings, depending on the engine used. List Asset TXs Endpoint using asset id as generated above curl https: Public metadata is immutable ; once set, it cannot be modified or deleted.
Bitcoin miners also earn fees from transactions. Learn how your comment data is processed. And Bob gets some visibility into some subset of transactions, perhaps he's selling that to marketers or. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. SendMicro micro if err! As we saw, the consensus mechanism depends on having a majority of the miners acting honestly out of self-interest. This is equivalent to listening to the new-block event and fetching each transaction in the new Block. Invalid blocks are rejected as soon as any one of the validation criteria using wii as mining rig install command line pivx wallet and are therefore not included in any chain. Transaction Confidence Endpoint curl https: We automatically retry HTTP requests 5 times. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the monero shares in a block coinomi wallet crashing chain to the main chain.
The Wallet itself can have any custom name as long as it does not start with the standard address prefix 1 or 3 for Bitcoin. For example, you could have a sidechain of Bitcoin that was also a sidechain of Ethereum. List Asset TXs Endpoint using asset id as generated above curl https: Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of We could still scale up bitcoin by quite a bit before we start really needing to push things off-chain. You can't do this a million times. Inside a payment channel, you just need the same relationship. Through market activities, the entire system becomes exactly as patient as its most-patient members.
You want to make sure Bob is unable to steal funds. Every now and then, one of the pool players will throw a combined dice throw of less than four and the pool wins. There's a fair amount. Address API: And there's a paper from called pay-to-contract and essentially if Alice has the data R which produces H, she can say I have paid you the money. Optional History of forwarding transaction hashes for this address forward; not present if this request has yet to forward any transactions. I'm afraid you're mistaken. List Asset TXs Endpoint using asset id as generated above curl https: All endpoints that can retrieve a single Object can be batched to return multiple objects. In case you missed the Resources section , the BlockCypher Test Chain is accessible from this resource:. But that already exists. But with gold you're taking on the security risks, so the fees are related to the security risk. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. Drivechain merely acknowledges this pre-existing fact. The encoding of the key is documented here. The likelihood that this transaction will make it to the next block; reflects the preference level miners have to include this transaction.
Any information or posts that are not bitcoin block per day drive chains bitcoin through is bitcoin price going to drop bitcoin mining safe of these sources should be seen as illegitimate. However, the website, walletexplorer. Event curl https: In case you missed the Resources sectionthe BlockCypher Test Chain is accessible from this resource:. Five Common Misconceptions Here I highlight five big hangups that people seem to have value bitcoin ethereum future of bitcoin 2019 and. The diagram is a simplified representation of bitcoin as a global network. By selecting the greatest-difficulty chain, all nodes eventually achieve network-wide consensus. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. Each time a pool buying bitcoin gemini how to buy dogecoin with litecoin finds a block header hash that is less than the pool difficulty, she proves she has done the hashing work to find that result. The trick is to try and solve both problems at. That's a lot of centralization. Digital signing can be a difficult process, and is where the majority of issues arise when dealing with cryptocurrency transactions. To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer. For more detail on confidence, check the Confidence Factor documentation. It is unknown whether the specific wallets that have sent Bitcoin funds into the address have a direct relationship with Mt. We leverage our own infrastructure; in particular, our Confidence Factor.
The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. Simplifies listening to confirmations on all transactions for a given address up to chicago board options exchange to add bitcoin colleges that accept bitcoin provided threshold. If Bob waits too long, Alice gets all of her money. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. There's a fair. The proof-of-work algorithm difficulty target for this block. So nobody would be able to pay each other; they can only pay Bob. But assume Bob is nice. In specific, this section will analyze that withdrawal information and examine conclusions if any can be made from it. Ask Question. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer. Time when best server for bitcoin cash how to buy bitcoin in ghana can be valid. Typically, the pool server charges a percentage fee of the rewards for providing the pool-mining service. In terms of deciding whether passing private keys for microtransactions is a reasonable tradeoff, consider the following:
I don't know who came up with the idea and we may never know. The returned object contains a private key in hex-encoded and wif-encoded format, a public key, and a public address. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. An evil fork is bad, because old users must upgrade, and track 1. Balance of confirmed satoshis on this address. You could start today, and have these workarounds and then hope that there's a malleability fix later to really scale out. Again, more screenshots and walkthroughs of the actual addresses will be provided shortly. Allows you to receive a fee for your own services. The address which will automatically forward to destination ; generated when a new request is created.
However, drivechain holds up better under attack than the skiplist. The returned object contains a private key in hex-encoded and wif-encoded format, a public key, and a public address. Bob can sign this at any time, and then broadcast it to the network, and in doing so close out the channel. It might work if you trust Bob but we're trying to minimize trust. I don't quite understand what you mean. A problem with a sidechain that only impacts the sidechain users. She does that by the receiver writing some signed message effectively a contract that says if Alice knows R which produces H then at that point Alice has paid me 0. The pool server runs specialized software and a pool-mining protocol that coordinates the activities of the pool miners. Right now bitcoin faces some interesting problems, like transactions aren't instant, and micropayments don't work. I am worried about bugs! Since the wallet addresses for QuadrigaCX were widely unknown, deposit information from customers was aggregated from the Reddit thread posted above as well as information shared through direct message. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. BMM only allows one side: How do we solve this? It's sort of weird right now. The number used as a variable in such a scenario is called a nonce. He can always pull funds from Alice and give them to Carol. Filters response to only include transaction hashes after txstart in the block. You can have funds committed within one second, there's no backsies, there's no double spending, etc.
Bob might just take bittrex hacked 2019 how to trade bitcoin in binary options bitcoin that Alice sent. Carol has a channel open. To help us track it, one is visualized as a red block originating from Canada, and the other is marked as a green block originating from Australia. Attribute Type Description id string Identifier of the event; generated when a new request is created. The payload is a confirmed TX. The maximum blockchain growth rate would have been about 1. So their proof requires a txn to be much larger. Blockchains contain a wealth of data, but much of it is inscrutable without arduous effort. Best case it may total 39 bytes. In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target.