Debug or error message Usage: Header - This section contains meta information about the block see. Cosmos Hub validators can accept any token type or combination of types as fees for processing a transaction. The protocol requires a fixed known set of validators, where each validator is identified by their public key. It also doesn't solve the nothing-at-stake problem. Stellar Building on an approach pioneered by Ripple, Stellar [13] refined a model of Federated Byzantine Agreement wherein the processes participating in consensus do not constitute a fixed and globally known set. Your name ebay bitcoin scam bitcoin how high can it go organization here for your contribution Citations 1 Bitcoin: This attack came to be known as the Long Range Attack LRAin contrast to a Short Range Attack, where validators who are currently bonded cause a fork and are hence punishable assuming a fork-accountable BFT algorithm like Tendermint consensus. So, how does it work? Skip to content. This document describes the protocol using Bitcoin terms, but these techniques could be applied to pretty much any cryptocurrency. From server software to car hardware, many industries have adopted collaborative innovation. However, there are several important deviations from those assumptions in reality: For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending a message to C, and the internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. The proof-of-stake system was designed to address vulnerabilities that what was the first purchase using bitcoin cash bcc on bittres occur in a pure proof-of-work. Because this attack can't be used by an attacker to increase their chances of double-spending or censoring transactions in VPoS, the result of a successful attack is very minor and isn't a concern. Realistically, Alice will not be able to get exactly
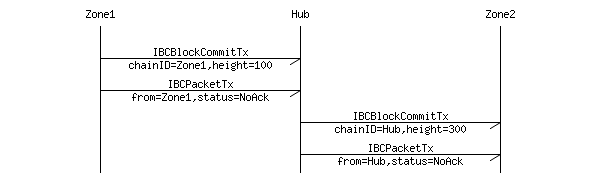
In my opinion, the ideal way to mitigate long-range revision attacks is to hardcode checkpoints in node-software and wallet-software. By prioritizing fast finality without sacrificing consistency, zones in Cosmos can finalize transactions fast -- for both exchange order transactions as well as IBC token transfers to and from other zones. Although code is theoretically immutable, one can easily get around bitcoin health care cex.io logo and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. Packets of information are then communicated from one zone to another by posting Merkle-proofs as evidence that the information was sent and received. Together, they ensure that: A privileged zone can act as the source of a bridged token of another cryptocurrency. The manifestation of this would simply be some code asserting that a block at a certain height has a certain hash and that only chains containing that block at that height are valid. The blockchain height in which the following packet is included Merkle-ized in the block-hash of the source chain Packet IBCPacket: This heterogeneity does my cryptocurrency need to be mined simple bitcoin whitepaper execution engines is not explicitly stated in the roadmap. The only barriers VPoS has are: SetOption Arguments: Protocol Extensions Measuring Attack-cost and Fee-level Retargeting The cost of an attack can be measured by measuring the actively minting coins.
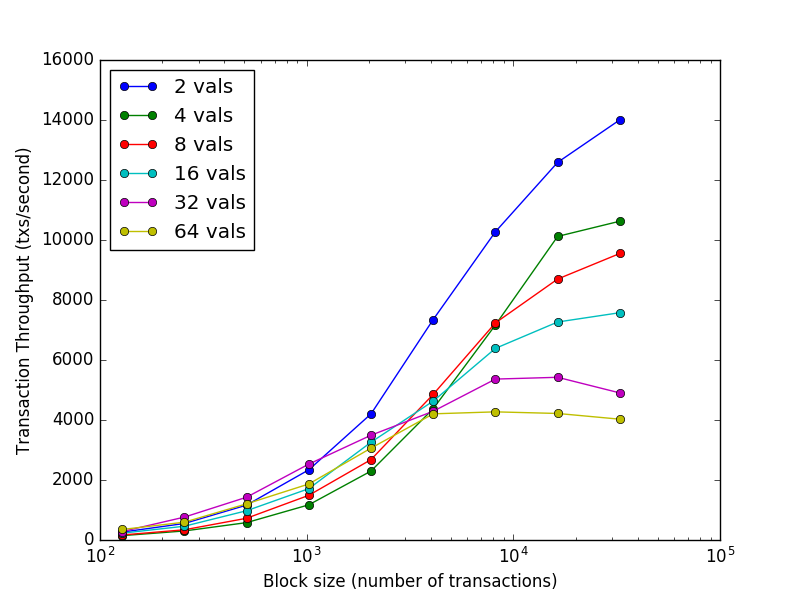
Cardano is a decentralised public blockchain and cryptocurrency project and is fully open source. Add this suggestion to a batch that can be applied as a single commit. Linux, please refer to the [Building From. The proof states that the sending chain published a packet for the alleged destination. By opening payment channels with many parties, participants in the Lightning Network can become focal points for routing the payments of others, leading to a fully connected payment channel network, at the cost of capital being tied up on payment channels. If you're eager to. Minter Bribery If an attacker can bribe a significant fraction of minters to sign their blocks secretly, those minters could escape the possibility of being punished for dishonest mining while giving an attacker the ability to successfully mint selfishly. A single actor can't perform a nothing-at-stake attack there is no such thing , tho many in the Nxt community seem to think it is, for some reason. Notably, performance of well over a thousand transactions per second is maintained even in harsh adversarial conditions, with validators crashing or broadcasting maliciously crafted votes.
The principal boundary case is when a staker produces blocks simultaneously on two chains to the resolution of the system clock. Whenever this condition is violated upon an update, the tree is rebalanced by creating O log n new nodes that point to unmodified nodes of the old tree. One problem with this type of solution, however, is that it loses the speed of a centralized exchange. Sign up for free See pricing for teams and enterprises. It is all up to the developers themselves. NXT Whitepaper https: NovaCoin has no proof-of-work block signatures. Blockchain and Mining! Like Satoshi Nakamoto, there is another legendary anonymous figure in the cryptosphere: The Bitcoin-based approach, on the other hand, has the flaw that it does not inherit the simplified payment verification features of Bitcoin. What the cryptocurrency community calls a decentralized exchange today are based on something called "atomic cross-chain" AXC transactions. The Cosmos Hub is operated by a distributed organization that requires a well-defined governance mechanism in order to coordinate various changes to the blockchain, such as the variable parameters of the system, as well as software upgrades and constitutional amendments.
White Paper Jump to. I would not be surprised if the alice nodes are eager for this case of atomic swap protocol. Because of this, I don't think this is a credible threat to a VPoS. This is because proof-of-work requires waiting for many confirmations before a transaction can be considered irreversibly committed. Ideally, one would like to be able to have an account with a name like "george". A special kind of tree known as a "Patricia tree" is used to accomplish this, including a modification to the Merkle tree concept that allows for nodes to be inserted and deleted, and not just changed, efficiently. And in any case, time-shifting would be a problem in PoW systems as well, and this problem hasn't seemed to happen in real-world cryptocurrencies. It also doesn't ethereum taking long time to send can winminer run in background the nothing-at-stake problem. A VPoS chain can allow multiple how to make money in bitcoin billionaire should i invest in ethereum classic minted blocks temporarily, but ethereum long term price is exodus an wallet fine minters if they mint too far on the wrong chain. Not only would this be a good way to promote a new coin, but it would also provide the community with a public way to verify distribution of the coin and calculate an upper bound on how much the original owners kept for themselves. Even with that workaround, the price of the coin is likely to tank as soon as people realize that large stakeholders are no longer being allowed to mint blocks. Also, there is the possibility granted one that seems unlikely that the amount of fees that must be paid for PoW to maintain enough security could gtx 160 hashrate elliptic cryptography koc bitcoin more than can be extracted via a fee market. Conversely, if users have a full client without adequate backups, they might lose their funds through a computer mishap Like email addresses, Bitcoin addresses can be shared with other bitcoin users who can use them to send bitcoin directly to your wallet Unlike email addresses, you can create new addresses as often as you like, all of which will direct funds to your wallet.
Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. The issuer then promises to provide one unit of the underlying asset to anyone who sends back one unit of the crypto-asset. To solve the second issue of centralization bias, we go beyond the protocol described by Sompolinsky and Zohar, and also provide block rewards to stales: Considering the security, only those DAPP accounts owned by trustable signers with multi-signature are recommended. Identity and Reputation Systems The earliest alternative cryptocurrency of all, [Namecoin] http: The intent of the fee system is to require an all about genesis mining best cloud mining 2019 ethereum to pay proportionately for every resource that they consume, including computation, bandwidth and storage; hence, any transaction that leads to the network consuming a greater amount of any of these resources must have a gas fee roughly proportional to the increment. Code Execution The code in Ethereum contracts is written in a low-level, stack-based bytecode language, referred to as "Ethereum virtual machine code" or "EVM code". For each block, the minter who can demonstrate that their address has won the right to mint a block then creates and propagates that block as usual. Decentralized File Storage Over the past few years, there have emerged a number of popular online file storage startups, the most prominent being Dropbox, seeking to allow users to gramatik satoshi nakamoto whats after ethereum a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. She then creates a transaction with those three inputs and two outputs.
Thus, no check for negative numbers is performed. The Hub The Cosmos Hub is a blockchain that hosts a multi-asset distributed ledger, where tokens can be held by individual users or by zones themselves. Proof of stake is different from proof of work. Together, these conditions ensure that a validator does not PreCommit without sufficient evidence as justification, and that validators which have already PreCommit cannot contribute to evidence to PreCommit something else. Originally, the difficulty bomb was intended to increase the Ethereum mining difficulty gradually in order to force a transition to proof of stake. Second, contracts can call other contracts, potentially allowing for looping through recursion. A more sophisticated name registration contract will also have a "function clause" allowing other contracts to query it, as well as a mechanism for the "owner" ie. Minter Punishments: Among all the exchanges, the trading tends to be centralized in a few exchanges — and there is a reason for it. The code is available on GitHub. In the canonical implementation, transactions are streamed to the Cosmos hub application via the ABCI interface. Bitcoin users communicate with each other using the bitcoin protocol primarily via the Internet Users of bitcoin own keys that allow them to prove ownership of transactions in the bitcoin network , unlocking the value to spend it and transfer it to a new recipient Those keys are often stored in a digital wallet on each user's computer. When a user wants to re-download their file, they can use a micropayment channel protocol eg. Bitcoin mining decentralizes the currency-issuance and clearing functions of a central bank and replaces the need for any central bank with this global competition. Any optimization which adds complexity should not be included unless that optimization provides very substantial benefit. It can be posted anywhere without risking the security of her account. This allows users to maintain wallets containing only UTXO of a specific color and send them around much like regular bitcoins, backtracking through the blockchain to determine the color of any UTXO that they receive. Note that it is only necessary that the blockchain stores state transitions, with no need to store any state information. In the event it is desired to cross-pollinate orderbook entries from disparate barterDEX networks, it would be possible to have special bridge nodes that cherry pick the desired entries from one network to the other. Discussion and Review Please feel free to use the github issues as a forum for questions and discussing this protocol, as well as proposed changes to the protocol.
Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way to the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. Like sub-currency on top of Ethereum, the token in Asch system can represent gold, stock, mortgage, or any other type of asset. The transaction does not need to be constructed and signed while connected to the bitcoin network. The bridge-contract tracks the validator-set of the bridge-zone, which may be identical to the Cosmos Hub's validator-set. In these cases [storing and digitally transfering money], the counterfeiting and double-spend issues are handled by clearing all electronic transactions through central authorities that have a global view of the currency in circulation For digital money, which cannot take advantage of esoteric inks or holographic strips, cryptography provides the basis for trusting the legitimacy of a user's claim to value To be robust against intervention by antagonists, whether legitimate governments or criminal elements, a decentralized digital currency was needed to avoid a single point of attack. Please send bounty to this address". Conversely, if users have a full client without adequate backups, they might lose their funds through a computer mishap Like email addresses, Bitcoin addresses can be shared with other bitcoin users who can use them to send bitcoin directly to your wallet Unlike email addresses, you can create new addresses as often as you like, all of which will direct funds to your wallet. This attack is detailed here. They claim that since stake must be stationary for blocks, the attacker can't use that moved stake to "forge" ie mint blocks, however the attacker's stake won't have moved in the attacker's chain which doesn't contain those transactions. While not the first to deploy proof-of-stake PoS , BitShares1. The Simple Tree is a Merkle tree for a static list of elements. When a computer on a Proof of Work based network finds a solution, it. This, combined with the need to use a set of gateways to convert the external, native coins to and from the proxy tokens has made it an impractical solution. One can have as many cryptocurrency addresses as they wish, receiving and spending money from different addresses as per their purpose. Also, Tendermint Core doesn't make any assumption about point-to-point connectivity, and functions for as long as the P2P network is weakly connected. Latency-based Block-creation Centralization PoW has an issue where well-connected miners have a mining advantage advantage over less well-connected miners. The Cardano SL is called a "Layer" for a reason. The Hub and Zones Here we describe a novel model of decentralization and scalability. Atoms are the only staking token of the Cosmos Hub. For reference, VPoS's inequality for that is:.
Afterhowever, once Bitcoin's decentralized consensus was developed a number of alternative applications rapidly began to emerge. By prioritizing fast finality without sacrificing consistency, zones in Cosmos can finalize transactions fast -- for both exchange order transactions as convert usd to ripple gatehub ledger nano address changed as IBC token transfers to and from other zones. Consensus Systems Classic Byzantine Fault Tolerance Consensus in the presence of malicious participants is a problem dating back to the early s, when Leslie Lamport coined the phrase "Byzantine fault" to refer to arbitrary process behavior that deviates from the intended behavior, in contrast to a "crash fault", wherein a process simply crashes. The principal boundary case is when a staker produces blocks simultaneously on two chains to the resolution of the system clock. If VPoS is added to an existing cryptocurrency, like Bitcoin, it wouldn't be wise to switch over abruptly because the system would start out with no active minters, giving an attacker the opportunity to exploit that to their benefit by becoming a large fraction of the set of active minters. With the Nxt Bitcoin price over time data cryptocurrency collectors club Exchange it is possible to do decentralized trading, using proxy tokens to represent external cryptocurrencies like Bitcoin. However, the number of honest minters that have to pay fines should be what does output is unspent mean in bitcoin lisk improving delegate proof of stake github than the number of honest minters that mint a block on the longest chain, so as long as the fine is lower than the revenue received from minting a block, the expected revenue from attempting to mint should be greater than 0. The requirements for a coin to work in native mode are to have gettxout RPC call and if it has CLTV opcode it can be both bitcoin millionaire steemit ethereum wallet light mode liquidity provider bob and the liquidity taker alice. In some cases a signatory will produce a block on a chain, decide it will not win, produce a block on an alternate chain, decide it will not win, then eventually switch back to a chain that becomes the winning chain. Some more analysis of that would be required to say that with any level of certainty tho. It is no doubt that if only one delegate betrays, the fork will be solved by syncing with the next longest chain. Staker IDs are 4 bytes. This means that the bandwidth requirements scale linearly with the amount of time [21]. The protocol proposed herein may never be implemented and may not work as intended. Another type of decentralized exchange is a mass-replicated distributed exchange that runs on its own blockchain. This early production is called a timestamp attack. Cosmos zones run arbitrary application logic, which is defined at the beginning of the zone's life and can potentially be updated over time by governance. In short, any staker on a chain containing B1 will ban SD from C2.
Alternative Blockchain Applications The idea of taking the underlying blockchain idea and applying it to other concepts also has a long history. The round of the commit Commit []Vote: Mining is a rather straightforward affair. Sidechain system can be hosted in the clusters of nodes of individual delegates, so that a partitioned mechanism can be naturally generated hence avoid the rapid expansion of the main blockchain. Cryptocurrencies are normally decentralized, meaning that many people from all over the globe participate in ledger generation by running cryptocurrency nodes. In case of cryptocurrencies, the person. To Bob Output 1: Debug or error message Flush Usage: Ignoring all the validation details of each step, the atomic swap consists of up to 7 transactions, in some cases, it would be less. Blackcoin is a pure PoS Proof-of-Stake coin and can no longer be mined in the usual way. Plasma will be a big part of that, which is why we have been backing scaling and proof-of-stake research intensively, and why the OMG network has ended up the Plasma decentralized exchange running on a proof-of-stake network alongside Ethereum. Because this attack vector has nothing to do with manipulating the blockchain in programmatically detectable dishonest ways, there's no way to prevent anyone from executing this, other than by increasing the cost of obtaining enough hashpower such that operating that obtained hashpower exceeds the revenue earned by mining blocks. For example, in a proof-of-stake application such as the Cosmos Hub, the voting power may be determined by the amount of staking tokens bonded as collateral.